
A 25-year-old Santa Clarita man has agreed to plead guilty to hacking a Disney employee's personal computer, stealing login credentials, and exfiltrating 1.1 terabytes of confidential data from internal Slack channels used by the entertainment giant.
According to a plea agreement filed by the U.S. Department of Justice on May 1, 2025, Ryan Mitchell Kramer will plead guilty to two felony counts: unauthorized access to a computer and threatening to damage a protected system. The charges stem from a targeted cyberattack carried out in the spring and summer of 2024 that compromised Disney's internal communications and led to the public leak of sensitive corporate data.
Kramer, operating under the alias “NullBulge,” created and distributed a malicious program disguised as an AI art generation tool. He uploaded this trojanized application to GitHub and other public repositories in early 2024, enticing users interested in generative AI. At least three victims, including one Disney employee, downloaded the program. Once executed, the software provided Kramer with remote access to the victims' machines and stored credentials.
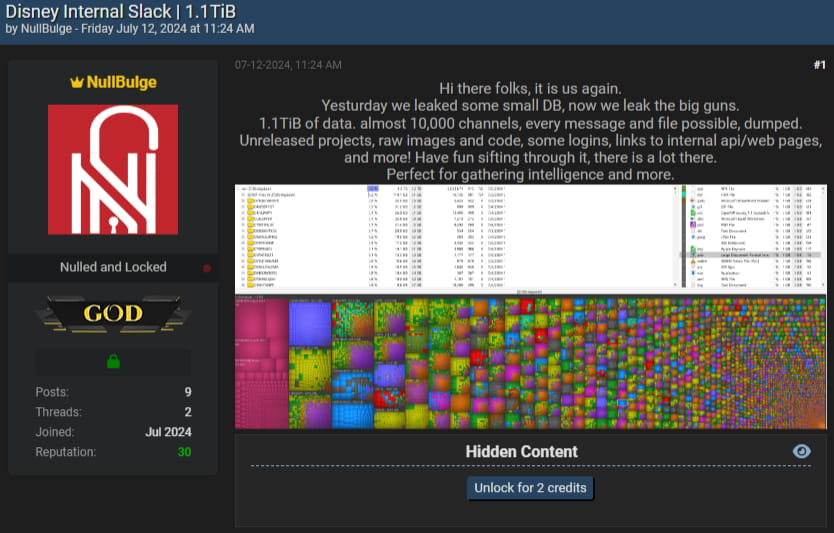
After infiltrating the Disney employee’s personal system between April and May 2024, Kramer accessed corporate Slack credentials stored in the victim’s account. Using those, he infiltrated Disney's internal Slack workspace and downloaded around 1.1 terabytes of data from nearly 10,000 channels. The dataset included unreleased media projects, internal code, links to APIs, and credentials for internal web services.
Disney, headquartered in Burbank, California, is one of the world’s largest media conglomerates, with operations spanning entertainment studios, television networks, and theme parks. The internal Slack environment Kramer compromised played a central role in facilitating project collaboration across the company’s divisions.
In July 2024, Kramer escalated the breach by contacting the employee he had hacked. Masquerading as a member of a fictitious Russian hacktivist group named “NullBulge,” he threatened to publish both the stolen Slack data and the victim’s personal information — including banking and medical records — unless he received a response. When the victim ignored the threats, Kramer followed through by leaking the entire dataset and personal documents on BreachForums and other file-sharing platforms on July 12.
Cyber Insider
At the time of the leak, Disney did not publicly confirm the breach, but cybersecurity observers quickly noted the scale of the data dump. The files, available via magnet link or for purchase on the dark web, contained sensitive intellectual property, potentially impacting Disney's upcoming releases and internal operations. The breach also raised alarms about the misuse of developer platforms like GitHub for malware dissemination and highlighted the risks of storing work credentials on personal devices.
The FBI conducted the investigation, which uncovered at least two additional victims who had their systems accessed by Kramer through the same malicious AI art tool.
Kramer is expected to appear in federal court in Los Angeles in the coming weeks. Each felony charge carries a maximum sentence of five years in prison.







Leave a Reply