
A critical security lapse at DeepSeek, a Chinese AI startup, exposed a publicly accessible ClickHouse database containing over a million log entries, including chat history, API keys, and backend operational details. The misconfigured database, discovered by Wiz Research, allowed full control over its contents without requiring authentication. DeepSeek has since secured the exposure following responsible disclosure.
Wiz Research, a cybersecurity firm specializing in cloud security, uncovered the exposed database while assessing DeepSeek's external security posture. During routine reconnaissance, researchers identified two unauthenticated ClickHouse database instances hosted at oauth2callback.deepseek.com:9000 and dev.deepseek.com:9000. These instances were entirely open, enabling unrestricted access to sensitive internal data.
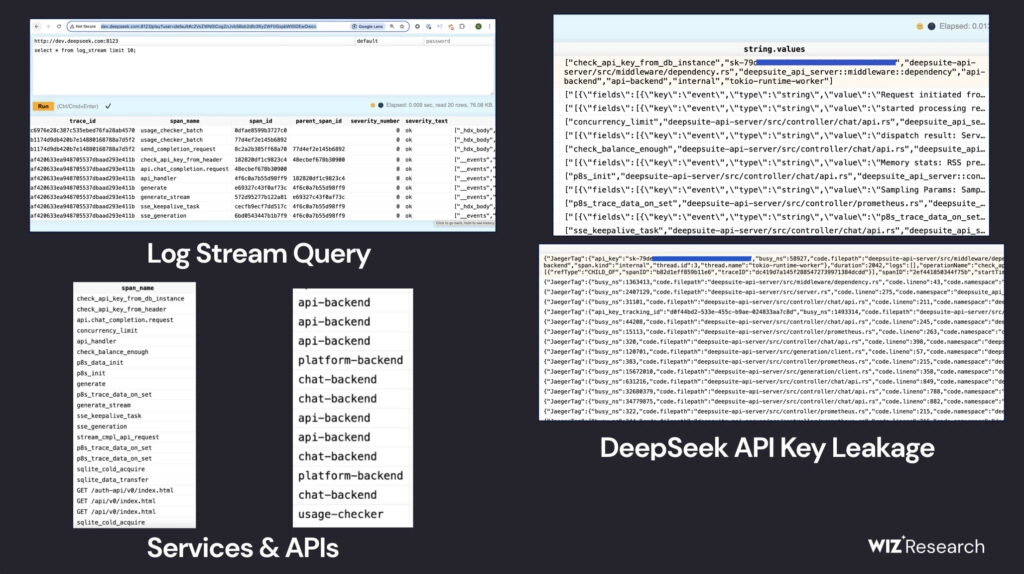
ClickHouse, an open-source columnar database management system designed for fast analytics, is widely used for large-scale data processing. However, its exposure without authentication meant that anyone could execute SQL queries via its HTTP interface. A simple SHOW TABLES; query revealed a log_stream table containing extensive internal logs.
Key exposed data included:
- Chat history: Logs of user interactions with DeepSeek's AI models.
- API keys: Potentially allowing unauthorized access to DeepSeek's internal services.
- Backend metadata: Details about system operations, including references to internal API endpoints.
- Timestamps and origins: Logs dating back to January 6, 2025, revealing the structure and function of DeepSeek's internal services.
Beyond passive data retrieval, the exposed database also enabled full database control, meaning a malicious actor could have escalated privileges within DeepSeek's environment, potentially modifying or exfiltrating additional data.
Wiz
DeepSeek's security stance
This revelation comes just days after our previous report on DeepSeek R1's security and privacy vulnerabilities. As we previously detailed, DeepSeek R1 — an AI model designed for advanced reasoning — was found to be highly susceptible to jailbreak attacks, enabling it to generate harmful content such as malware, disinformation, and illicit instructions.
Additionally, DeepSeek's privacy policy raised concerns by confirming that all user interactions are stored on servers in China, raising the risk of government access under China's data-sharing laws. The latest discovery of exposed chat logs now provides concrete evidence that DeepSeek's security posture is alarmingly weak, reinforcing concerns about the safety of user data.
Wiz Research emphasized that the rapid adoption of AI services without proper security measures is a growing risk. While much of the AI security conversation revolves around advanced threats, the most immediate dangers often come from fundamental lapses — such as exposing critical infrastructure to the open internet.







Leave a Reply