
A cybercriminal has posted samples of data allegedly stolen from CACI International, a U.S. government contractor, on a popular hacker forum.
CACI is an IT service provider with 23,000 employees and an annual revenue of $7 billion. The company provides a range of services to multiple U.S. federal government branches, including defense, homeland security, intelligence, healthcare, and others. Hence, the firm holds sensitive data relating to the operations of various government agencies, some of which are critical for national security.
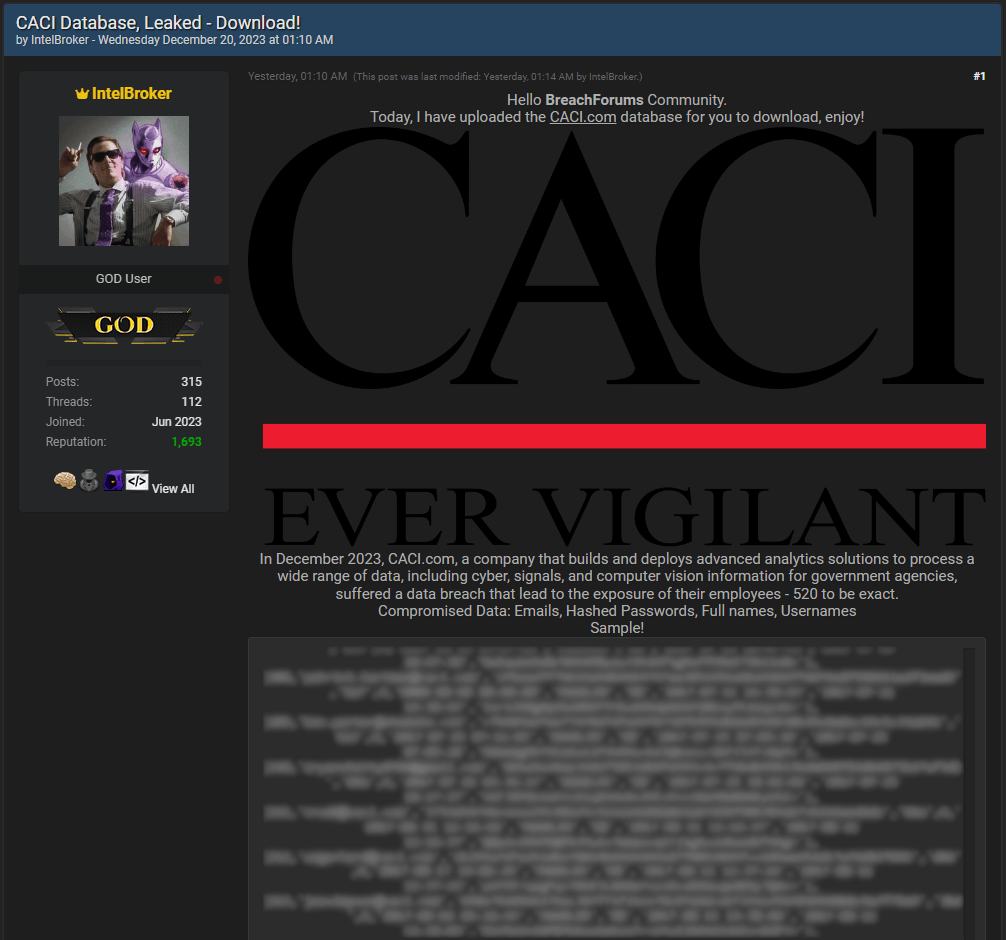
Yesterday, the prolific cybercriminal IntelBroker leaked a database he claims to have stolen from a recent (December 2023) breach on CACI systems. IntelBroker says the database contains info on 520 CACI employees.
The exposed information includes the following:
- Email addresses from where full names can be deduced
- Hashed passwords
- Unique record identifiers
- Account creation timestamps
- Account status (‘ENABLED’)
A sample of the data corresponding to 30 employee entries was leaked freely and not sold or auctioned, but the entire database can only be downloaded by registered forum users after paying a small amount.
If the leak is real and CACI did not realize the breach quickly enough, IntelBroker and his co-conspirators could have accessed employee accounts to steal sensitive information from the firm’s networks, which the cybercriminal may sell privately.
The hashed strings are 64 characters long, suggesting that the algorithm used for encrypting the account passwords is likely SHA-256, which is strong and collision-resilient. However, its final robustness against brute-forcing/cracking also depends on the salts used to add randomness to the result, making deciphering more challenging.
RestorePrivacy has contacted CACI with a request for a comment on the validity of the leaked data and whether they have detected any unusual activity on their systems, but we have not received a statement by publication time.
IntelBroker and the hacking collective ‘CyberNiggers’ have been very active in recent months, claiming multiple attacks against high-profile entities and leaking sensitive data on hacker forums. In late November 2023, the cybercriminal claimed that he had breached General Electric and accessed confidential information relating to the U.S. government defense R&D agency DARPA.
In a different case, the threat actor leaked 146,000 lines of data exposing users of the Android meal prep planning app KitchenPal.
Further reading
- Hacker Boasts Access to Con Edison Customer and Contractor Database
- T-Mobile Retailer Suffers Breach, Employee Data Leaked on Hacking Forum
- International Law Enforcement Operation Dismantles QBot Botnet
- Massive New Twitter Leak Allegedly Exposes 400M+ Users
- 23andMe Accounts Hijacked and Data Put Up for Sale on Hacker Forum







Thank you Heinrich for informing about any new leak. Merry Christmas!