
McAfee Labs has unveiled an intricate infection mechanism of the DarkGate malware, which employs the AutoHotkey scripting utility to bypass Microsoft Defender SmartScreen. The report details a novel infection chain starting from deceptive HTML and XLS files, advancing through multiple stages of evasion and execution.
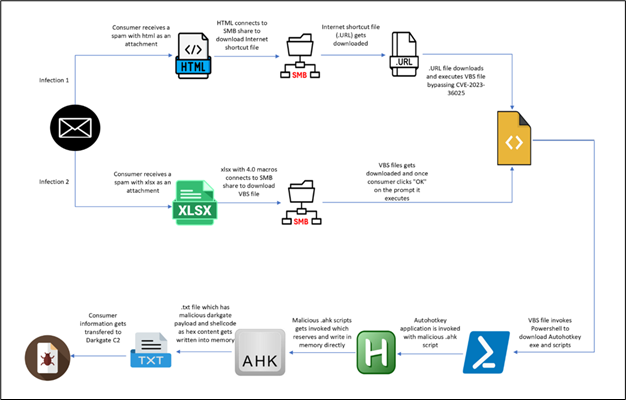
DarkGate, a Remote Access Trojan (RAT) developed using Borland Delphi and marketed as Malware-as-a-Service (MaaS) since at least 2018, utilizes a multistage infection process. It starts with HTML and XLS vectors carrying identical shellcode and payload. The HTML infection begins with a phishing page mimicking a Word document which prompts users to open the document in “Cloud View.” This leads to a series of deceptive interactions culminating in the execution of a malicious .URL file.
The .URL file is designed to evade the security mechanisms of Windows Defender SmartScreen, exploiting the CVE-2023-36025 vulnerability, which allows execution without any security prompts on unpatched systems. The attack chain presented in the McAfee report is facilitated by downloading a VBScript, which then downloads and executes a series of files, including the AutoHotkey executable.
McAfee
Technical Breakdown
- Initial Vectors: The infection uses HTML and XLS files to lure users into initiating the malware's execution.
- Evasion Techniques: Utilizes CVE-2023-36025 and CVE-2024-21412 vulnerabilities to bypass SmartScreen prompts.
- Payload Delivery: Involves multiple file downloads that culminate in the execution of the AutoHotkey script. This script, loaded with malicious instructions, is capable of executing further payloads.
- Persistence Mechanisms: Achieved through a .LNK file dropped in the startup folder, ensuring the malware's activation upon system reboot.
Infection Process
The HTML-based attack vector deceives users into allowing a redirection to Windows Explorer, displaying a manipulated window title to appear as if it's accessing a legitimate OneDrive link. It then prompts the execution of a .URL file, which directly triggers the download and execution of a VBScript. This script initiates a series of command-line operations involving PowerShell and AutoHotkey to establish a foothold on the infected machine.
Subsequent steps include downloading additional scripts and executables, setting file attributes to hide malicious activities, and executing further commands to maintain persistence and control over the compromised system.
McAfee
Mitigation
To combat threats like DarkGate, organizations and individuals should adhere to keeping operating systems and applications, especially security software, up-to-date, scrutinizing emails for unusual sender information, grammatical errors, and suspicious links or attachments, and using spam filters, verifying HTTPS connections on websites, and deleting any suspicious emails or files immediately.
The discovery of DarkGate's latest evasion techniques highlights the persistent and evolving nature of the emerging threat. Since the disruption of Qbot (Qakbot), DarkGate has assumed a more prominent position in the initial infection cybercrime market, standing above other candidates including Pikabot.







Leave a Reply