
The dismantling of a sophisticated dark web laundering network tied to over $24 million in illicit funds has revealed just how vulnerable even the most anonymity-conscious actors can be when digital traces are left behind — particularly across encrypted messaging platforms and cloud services.
Anurag Pramod Murarka, a 30-year-old Indian national operating under aliases like “elonmuskwhm” and “la2nyc,” was sentenced earlier this year to over 10 years in U.S. federal prison for operating a sprawling international money laundering service. Murarka’s operation converted cryptocurrency — sourced from darknet marketplaces, hacking operations, and drug trafficking — into untraceable cash sent via U.S. Postal Service mail. While the laundering network used layered anonymization techniques, it ultimately unraveled due to missteps in digital hygiene and the persistent visibility afforded by metadata and cloud surveillance.
Tracking down the suspect on the cloud
Blockchain analysis firm TRM Labs, which has had private involvement aiding the law enforcement investigations, shed more light into how exactly the authorities unmasked the identity of Murarka.
The man coordinated with clients via Telegram, WhatsApp, and Wickr, relying on these platforms to confirm exchanges and validate payments. Couriers in the U.S. sent photo proof of dollar bills, whose serial numbers were then matched by buyers — a three-way trust mechanism built entirely on ephemeral messages. But the very tools that gave the illusion of security became central to the case against him.
A breakthrough came when FBI agents tied a WhatsApp number used in post-delivery coordination — +91 9867615027 — to Murarka’s identity through Indian visa records. That number also linked to an Apple ID, enabling law enforcement to secure a sealed search warrant for his iCloud account. This move gave investigators access to a trove of synced data, including screenshots of crypto receipts, Telegram logs, and GPS-tagged images placing Murarka at the scene of laundering activities.
The iCloud data formed a bridge between pseudonymous online activity and Murarka’s real-world identity. Despite operating offshore and avoiding in-person interactions, his use of mainstream devices and cloud services undercut the operational security of his laundering empire. Once inside his Apple ecosystem, agents uncovered archived communications, detailed exchange logistics, and evidence of coordination across multiple encrypted platforms—all preserved in backups.
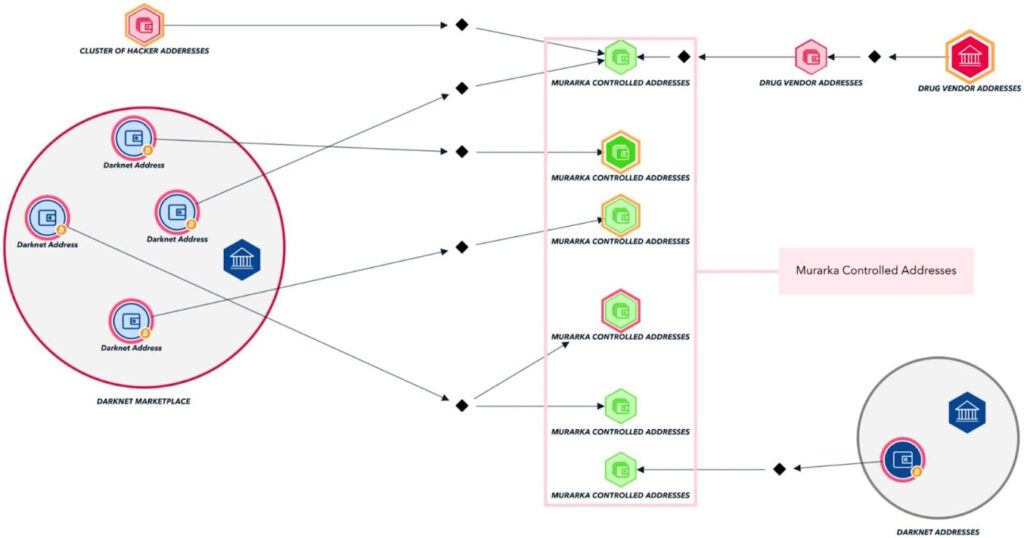
Murarka’s arrest occurred in 2023 after he entered the U.S. for medical reasons, at which point the FBI covertly assumed control of his laundering infrastructure. Over the following year, agents ran the operation undercover, gathering intelligence on hundreds of users. Many transactions were traced using blockchain forensics, revealing funds tied to drug sales, crypto theft, and even proceeds from violent crime. Public blockchain data, once enriched with communication metadata from messaging apps and phone records, became a high-resolution map of his laundering network.
Murarka’s fall illustrates a growing trend in cybercrime enforcement: pseudonymity is not immunity. While his operation used the hawala system, dark web markets, and peer-to-peer platforms like LocalMonero to stay hidden, it was his personal device footprint and reliance on consumer services — especially Apple and Meta’s infrastructure — that led to attribution. The FBI’s ability to cross-reference cloud-stored communications with blockchain transactions exemplifies the shift toward multi-vector investigations, where end-to-end encryption offers protection only until metadata or backups are exposed.
Ultimately, the illusion of compartmentalized identities across services can be shattered when a single phone number or cloud account bridges them. Law enforcement’s use of pen registers, cloud warrants, and blockchain tracing demonstrates how encrypted apps, while secure in transit, are often undermined by usage patterns, account linkage, or careless device configuration.







Leave a Reply