A chain of four critical vulnerabilities collectively dubbed PerfektBlue has been discovered in OpenSynergy's BlueSDK Bluetooth stack, exposing millions of automotive systems to over-the-air one-click remote code execution (RCE) attacks.
Despite patches being released in September 2024, many affected vehicles remain unpatched due to complex supply chains and inconsistent vendor updates.
The vulnerabilities were uncovered by the PCA Security Assessment Team, who are active in automotive security research, and recently uncovered severe flaws in VW and Skoda cars.
The team didn't have access to BlueSDK source code. Instead, researchers performed a binary analysis of compiled Bluetooth executables found in embedded systems. The findings were reported to OpenSynergy in May 2024 and confirmed by the vendor in July 2024. Public disclosure occurred on July 7, 2025, after repeated evidence of unpatched deployments.
OpenSynergy's BlueSDK is a widely adopted embedded Bluetooth protocol stack, especially popular in the automotive industry. It supports both Bluetooth Classic and Low Energy modes and implements a wide range of profiles, including A2DP, AVRCP, HFP, HID, and GATT, making it attractive for in-vehicle infotainment (IVI) platforms. As a configurable and closed-source Bluetooth framework, BlueSDK is licensed by the Bluetooth SIG and used by major auto manufacturers such as Mercedes-Benz, Volkswagen, and Skoda.
PerfektBlue is composed of four CVEs:
- CVE-2024-45434 (Use-After-Free in AVRCP, CVSS 8.0 – Critical)
- CVE-2024-45431 (Improper validation in L2CAP, CVSS 3.5 – Low)
- CVE-2024-45433 (Incorrect function termination in RFCOMM, CVSS 5.7 – Medium)
- CVE-2024-45432 (Incorrect parameter in RFCOMM function call, CVSS 5.7 – Medium)
These issues can be chained to obtain remote code execution on a vulnerable device following a Bluetooth pairing operation. Depending on the implementation, the attack may require only a single click or no user interaction at all, particularly if insecure pairing modes, such as “Just Works,” are enabled.
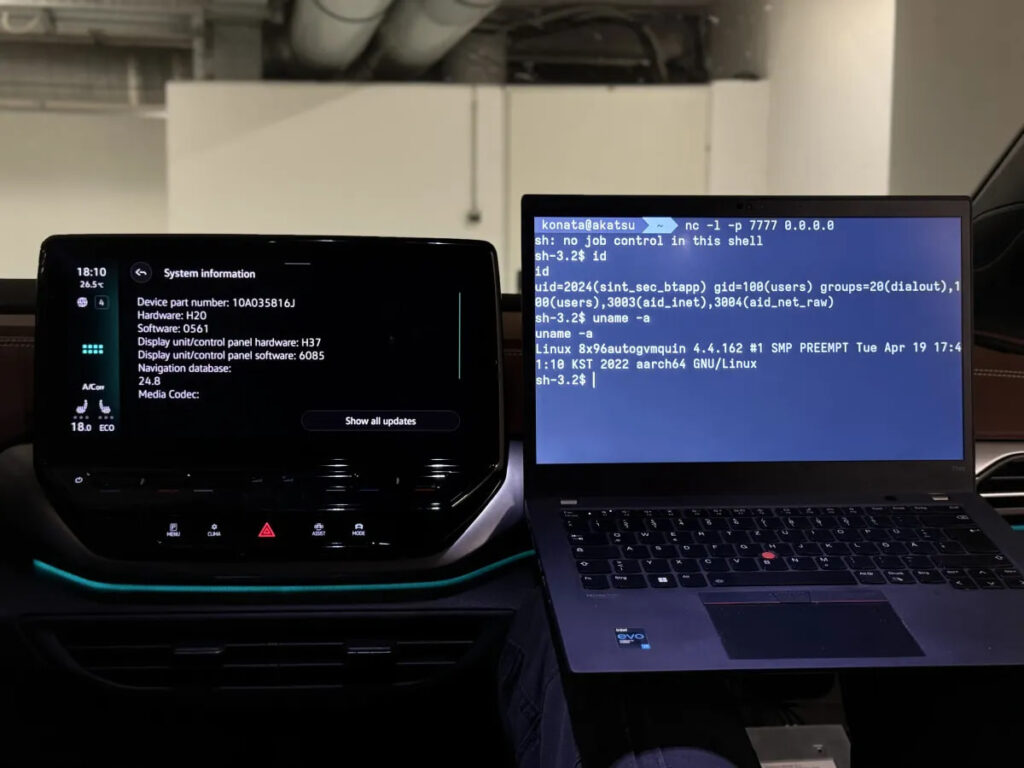
The impact of PerfektBlue is significant. PCA researchers demonstrated successful exploitation on IVI systems of three major automotive brands:
- Mercedes-Benz NTG6: Attackers gained phone-level user permissions after exploiting a 2020–2021 firmware.
- Volkswagen ID.4 ICAS3: Exploitation of both 2021 and 2023 firmware versions showed attackers could access the system with sint_sec_btapp privileges.
- Skoda Superb MIB3: A similar outcome was demonstrated, again confirming broad vulnerability across multiple firmware generations.
PCA
These RCE footholds allow attackers to potentially access GPS data, microphone input, contact lists, and even pivot to other electronic control units (ECUs) within the vehicle, depending on the system architecture.
While OpenSynergy confirmed to PCA that patches were distributed to BlueSDK customers in September 2024, several OEMs, including an unnamed manufacturer, reported in mid-2025 that they never received the necessary security updates. PCA attributes the patching delays to the layered and often opaque automotive supply chains.
BlueSDK's status as a configurable framework complicates detection and mitigation efforts. Without direct firmware inspection, it's difficult to know if a given device is vulnerable. For users, especially vehicle owners, this presents a challenge, as they must rely on their manufacturer's update cadence and transparency.
The best course of action for them would be to update their infotainment system firmware to the latest available version. If you're concerned about security, consider disabling Bluetooth functionality entirely.







Leave a Reply