
Cybereason has published a follow-up analysis on the “Cuckoo Spear” campaign, a covert cyber-espionage operation linked to China's state-sponsored APT10 group. The latest report delves into the technical details of two malware components used in the campaign — NOOPLDR and NOOPDOOR — shedding light on their operation and capabilities.
Background recap: the Cuckoo Spear campaign
In the initial report, Cybereason highlighted APT10's focus on critical sectors in Japan, India, and Taiwan. The group has leveraged sophisticated tactics to persist in compromised networks for extended periods. Key to their persistence are NOOPLDR, a malware loader, and NOOPDOOR, a backdoor. The group uses legitimate Windows processes and advanced techniques to evade detection, such as deploying NOOPLDR via MSBuild and maintaining persistence through scheduled tasks, WMI event consumers, and malicious Windows services.
In-depth arsenal analysis
The latest analysis provides a technical breakdown of the NOOPLDR loader and NOOPDOOR backdoor, revealing the intricacies of their operation, stealth mechanisms, and capabilities.
NOOPLDR-DLL variants and capabilities
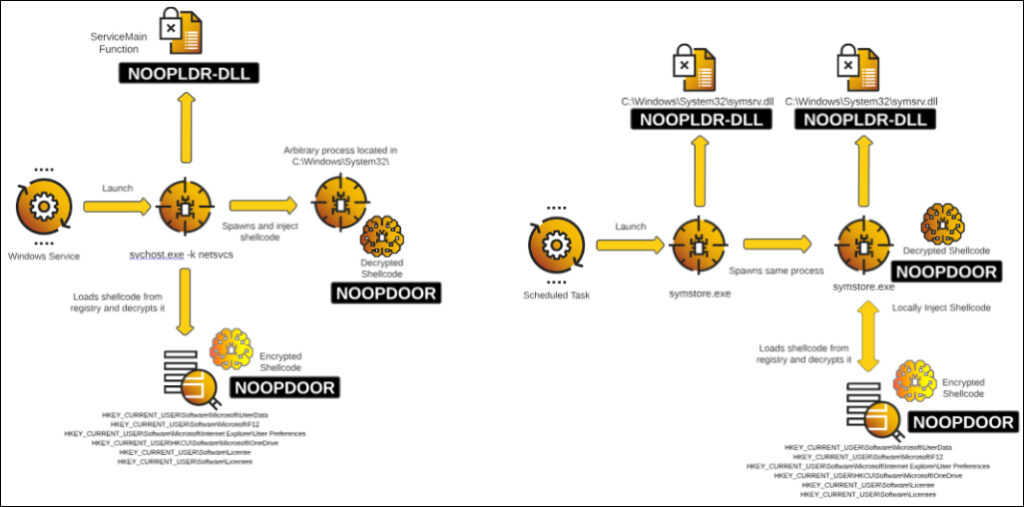
Cybereason found different versions of NOOPLDR-DLL, which function as loaders for the main payload. The DLL variants achieve persistence through several mechanisms:
- The malicious DLL files are registered as services and loaded as part of the system process svchost.exe through DLL side-loading.
- The code within the DLLs is heavily obfuscated using control flow flattening, and key strings are XOR-encoded to complicate reverse engineering.
- Shellcode, encrypted and stored in the registry, is injected into processes by leveraging system APIs and custom syscalls, potentially bypassing user-mode hooks.
Cybereason
NOOPLDR-C# Variant
Another variant of NOOPLDR, written in C#, is stored within an XML file and loaded through MSBuild, a legitimate Windows tool. This variant is highly obfuscated and employs unique configurations for different victim devices. NOOPLDR-C# can retrieve shellcode from a specified .dat file or registry key, decrypt it, and inject it into target processes. The obfuscation techniques and custom encryption routines add to the complexity of analyzing this variant.
Cybereason
NOOPDOOR shellcode and execution
NOOPLDR decrypts shellcode from several potential registry locations using an AES-CBC encryption scheme with an initialization vector derived from the MachineId of the infected machine. This allows APT10 to securely retrieve and execute NOOPDOOR, maintaining a stealthy and persistent backdoor on victim systems.
The NOOPDOOR backdoor exhibits several advanced capabilities:
- It dynamically resolves Windows API calls through a hashing mechanism and employs anti-debugging measures by detecting common debugging tools such as x64dbg, ollydbg, and Wireshark.
- It utilizes a Domain Generation Algorithm (DGA) to create changing C2 domain names. While the DGA generates HTTP-like URLs, actual communication with C2 servers is conducted via a custom TCP protocol.
- NOOPDOOR allows for data exfiltration to remote servers and supports internal pivoting for lateral movement within the network if external C2 communication is blocked.
C2 server capabilities
A variant of NOOPDOOR observed by Cybereason suggests it can function as an internal C2 server within compromised networks. This variant can modify firewall rules, listen on designated ports, and execute various commands such as file manipulation and process creation.
Detection and defense recommendations
Cybereason advises organizations to implement a multi-layered detection and response strategy, focusing on identifying abnormal behavior linked to the Cuckoo Spear campaign. Key recommendations include:
- Use dedicated queries to detect suspicious MSBuild executions, service creations involving .xml files, WMI consumer events, and DGA-like network behavior.
- Organizations should block known NOOPDOOR-related C2 domains and registry key paths.
- Monitor critical directories like System32 for unauthorized DLL files and analyze traffic on internal ports (e.g., 5984) for unusual patterns.







Leave a Reply