
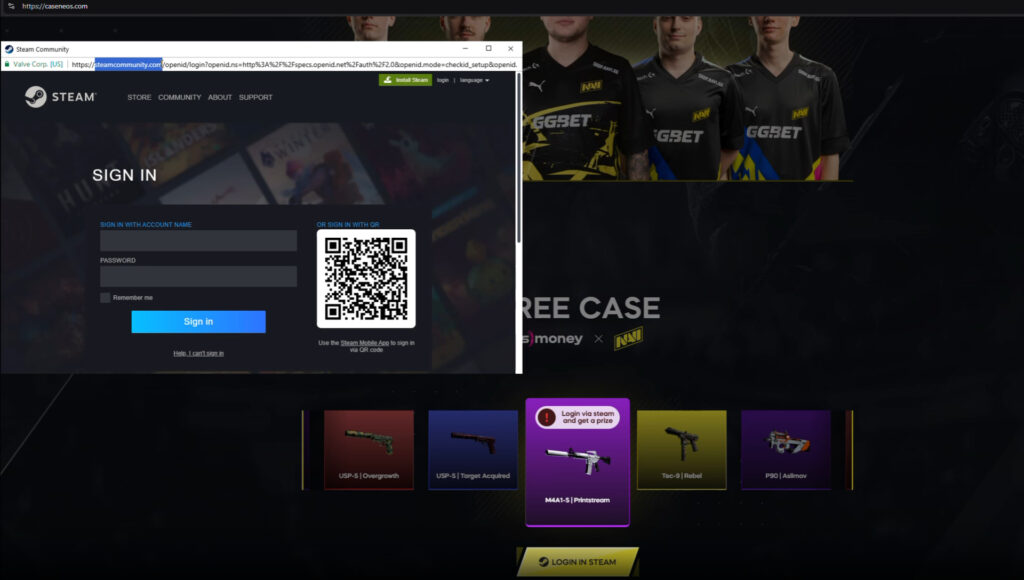
A phishing campaign leverages browser-in-the-browser (BitB) techniques to steal Steam credentials, with attackers primarily targeting Counter-Strike 2 players by impersonating the professional eSports team Navi.
The campaign was detailed by Silent Push threat analysts, who reported that the attackers are leveraging fake browser pop-up windows that mimic legitimate Steam login prompts. These deceptive windows include realistic interface elements, such as URL bars and branding, designed to lure users into entering their login credentials. Once entered, the data is siphoned by the attackers, likely to be sold on black markets or through online gaming account reselling platforms.
The phishing campaign appears to be focused on English-speaking users, though Silent Push also identified a Mandarin-language variant hosted on simplegive[.]cn, suggesting the campaign may have international aspirations. The attackers specifically target fans and followers of Counter-Strike 2 and the renowned Ukrainian eSports team Natus Vincere (NaVi), using their logos and branding to add legitimacy to the scams.

Silent Push
Counter-Strike 2, released in September 2023 by Valve, is a free-to-play tactical shooter available through Steam, the world’s largest digital distribution platform for PC games. Steam, also developed by Valve, holds approximately 75% of the global PC gaming market. Due to the high value of some accounts — especially those containing rare in-game items or extensive game libraries — Steam profiles are often sold for thousands of dollars on marketplaces like playerauctions[.]com.
Silent Push
According to Silent Push’s analysis, the phishing campaign is being promoted via platforms like YouTube, where domains such as caserevs[.]com were pushed through suspiciously popular videos. The attackers also reused phishing templates and JavaScript code across domains including caseneus[.]cfd, caseners[.]com, and caseneiv[.]com. All sites attempt to present a convincing login experience using BitB tactics.
Silent Push
BitB attacks are particularly deceptive because they embed fake browser windows within actual webpages, making them look like legitimate pop-ups. Unlike real browser windows, these fake pop-ups cannot be moved or resized independently. They are especially effective on desktop systems and are harder to detect by casual users, many of whom remain unaware of this phishing vector.
Silent Push has tied the campaign to a dedicated IP address (77.105.161[.]50), and identified repeated use of identical HTML titles and code hashes across multiple phishing domains. These technical fingerprints can be used to track and block similar campaigns. The firm has published sample Indicators of Future Attacks (IOFAs) and provided tools in its Community Edition platform to help security teams proactively hunt for similar threats.
To defend against BitB attacks, Silent Push advises the following:
- Verify pop-up authenticity by attempting to drag login pop-up windows outside the browser frame. Legitimate windows can be moved freely; fake ones cannot.
- Double-check URLs, especially on pop-ups, claiming to be login forms.
- Enable Steam Guard and two-factor authentication (2FA) which adds a secondary layer of protection even if credentials are stolen.







Leave a Reply