
Security researchers from Akamai's Security Intelligence and Response Team (SIRT) have uncovered a new botnet campaign leveraging an unfixed zero-day vulnerability in AVTECH IP cameras.
This command injection vulnerability in the camera’s brightness function allows remote code execution, enabling the spread of a variant of the infamous Mirai botnet with ties to the COVID-19 pandemic.
The flaw was discovered by Akamai researcher Aline Eliovich and represents a significant threat, particularly because it targets outdated AVTECH IP camera devices for which there is no fixing patch available. Despite being discontinued, these devices remain in use globally, including within critical infrastructure managed by transportation authorities.
Attack details
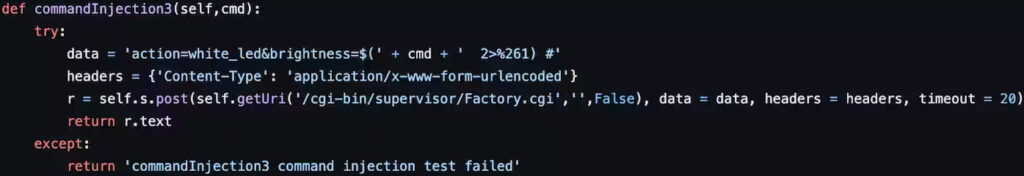
The botnet, referred to as Corona Mirai due to its code strings referencing the COVID-19 virus, exploits the zero-day vulnerability to execute remote commands on compromised systems. The attack chain begins by targeting the “brightness” argument in the camera’s configuration file, /cgi-bin/supervisor/Factory.cgi, to inject malicious code. Once the vulnerability is exploited, the malware establishes connections to numerous hosts through Telnet, often targeting ports 23, 2323, and 37215. The malicious payload then spreads across networks, compromising other vulnerable devices.
Akamai
Notably, the botnet also targets additional older vulnerabilities such as CVE-2014-8361 and CVE-2017-17215, which affect various widely-used IoT devices. These vulnerabilities have been exploited in the wild for years, but they continue to be effective due to many devices remaining unpatched.
Wider implications
The discovery of CVE-2024-7029 is concerning not only because of its immediate impact on AVTECH devices but also due to the broader implications of unpatched, legacy systems still in active use. The exploit was first observed in March 2024, although signs of this variant date back to December 2023, highlighting the persistence of these threats. Despite the availability of a proof-of-concept for this vulnerability since 2019, a formal CVE assignment was only made in August 2024, further complicating detection and mitigation efforts.
The compromised devices often belong to organizations that manage critical infrastructure, making the potential impact of this botnet campaign particularly severe. The ability of the Corona Mirai botnet to remain under the radar for so long underscores the growing trend of attackers exploiting older, low-priority vulnerabilities that are frequently overlooked in patching cycles.
Given the nature of the vulnerability and the critical areas it affects, it is imperative for organizations to prioritize the following steps to mitigate risks:
- Ensure all AVTECH devices and other IoT equipment are updated to the latest firmware versions. In this case, however, replacing the EoL devices with new and supported models is the only solution.
- Isolate IoT devices from the main network to limit the spread of infections and reduce the impact of compromised devices.
- Replace default credentials on IoT devices and disable remote/internet access admin portals if not needed.







Leave a Reply