
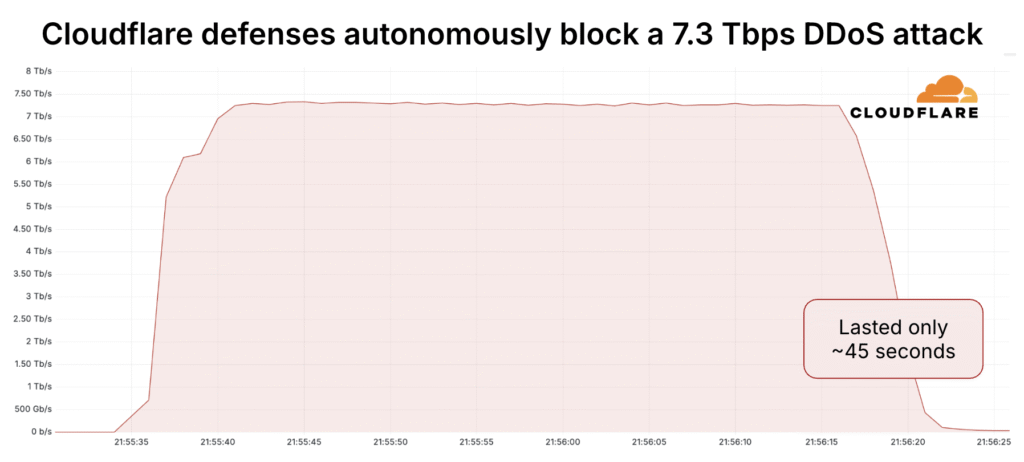
In May 2025, Cloudflare successfully mitigated the largest distributed denial-of-service (DDoS) attack ever recorded, peaking at a staggering 7.3 terabits per second.
The volumetric assault, which lasted under a minute but delivered 37.4 terabytes of traffic, was autonomously blocked by Cloudflare’s global mitigation systems without human intervention or service disruption.
The victim in this case was a hosting provider protected by Cloudflare’s Magic Transit service, which is specifically designed to shield entire IP subnets from volumetric and protocol-based attacks.
Cloudflare
Cloudflare, a leading web infrastructure and security company with a global presence in nearly 300 cities, has long served as a frontline defense for hosting firms, ISPs, and enterprises. Its Magic Transit product routes network traffic through Cloudflare’s global network, filtering malicious packets before they reach their destination. The targeted IP in this incident was advertised via global anycast, distributing the malicious traffic to 477 Cloudflare data centers worldwide and absorbing the massive payload without any centralized bottleneck.
The attack delivered an average of 21,925 destination ports per second, peaking at over 34,000, in what Cloudflare describes as a multi-vector campaign. Although 99.996% of the flood was raw UDP traffic, several classic reflection and amplification vectors were detected, including:
- QOTD (Quote of the Day): Leveraging UDP/17 to bounce amplified replies.
- Echo: Abusing legacy UDP/TCP port 7 services to reflect traffic.
- NTP (Network Time Protocol): Exploiting misconfigured servers using the deprecated monlist command.
- Portmap: Targeting UDP/111 services commonly used in legacy RPC-based systems.
- RIPv1: Misusing outdated routing protocols via UDP/520.
- Mirai UDP floods: Launched by infected IoT devices under botnet control.
These vectors, although representing only a fraction of the overall volume, underscore the lingering presence of outdated services across the Internet. Cloudflare emphasized that disabling obsolete protocols and properly configuring services are essential in preventing devices from being weaponized in DDoS attacks.
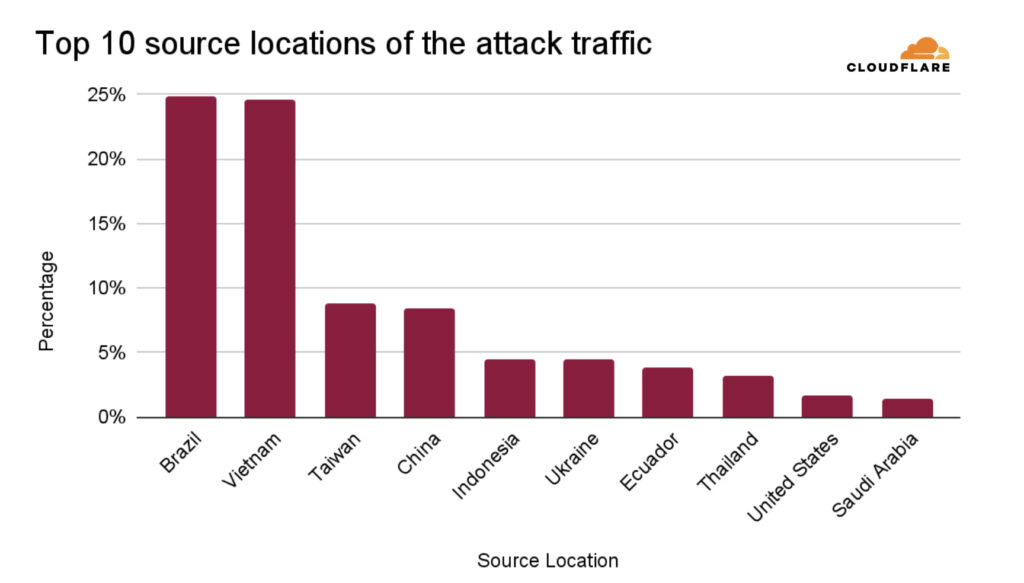
The origin of the attack was notably diverse, involving over 122,000 source IPs spread across 5,433 autonomous systems in 161 countries. Brazil and Vietnam were the top contributors, each accounting for roughly a quarter of the traffic. Other major contributors included networks in Taiwan, China, the U.S., and Saudi Arabia. AS27699 (Telefonica Brazil) and AS7552 (Viettel Group) were the top source networks, together responsible for over 20% of the malicious traffic.
Cloudflare
Cloudflare detected and mitigated the traffic using a combination of real-time packet sampling, fingerprinting, and autonomous mitigation logic. Packets entering any of its edge data centers were analyzed using extended Berkeley Packet Filter (eBPF) programs operating within the Linux kernel’s eXpress Data Path (XDP). A heuristic engine, dosd (Denial-of-Service Daemon), then identified and fingerprinted attack patterns. The most accurate fingerprints were compiled into eBPF-based mitigation rules and automatically deployed without human involvement. Once attack signatures ceased, the mitigation rules expired naturally.







Leave a Reply