
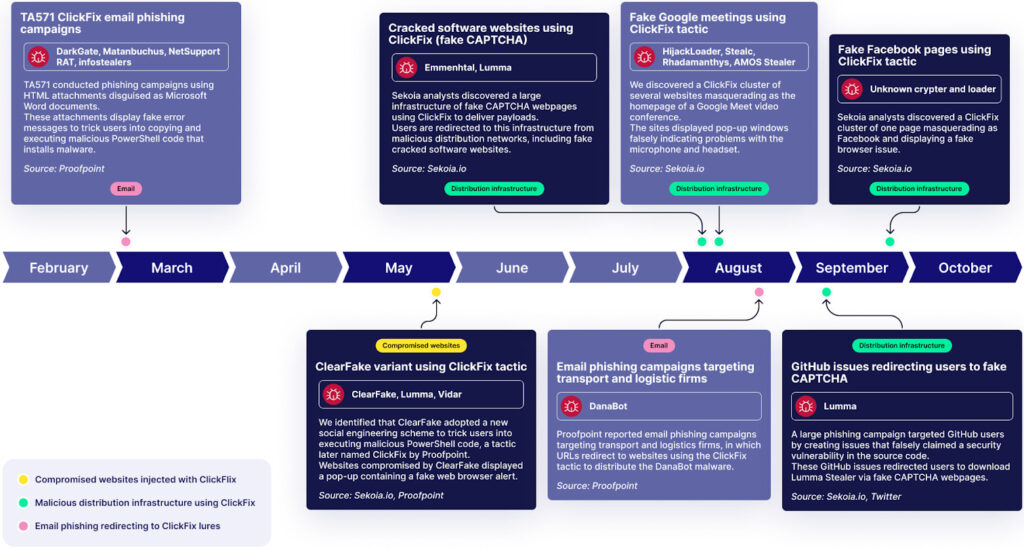
A newly identified social engineering campaign, dubbed ClickFix, uses fake Google Meet pages to distribute infostealers and other malware, targeting both Windows and macOS users.
First observed in mid-2024, the campaign has been closely monitored by the Sekoia's team, which earlier today released a detailed analysis of the campaign and the threat groups behind it.
ClickFix expanding
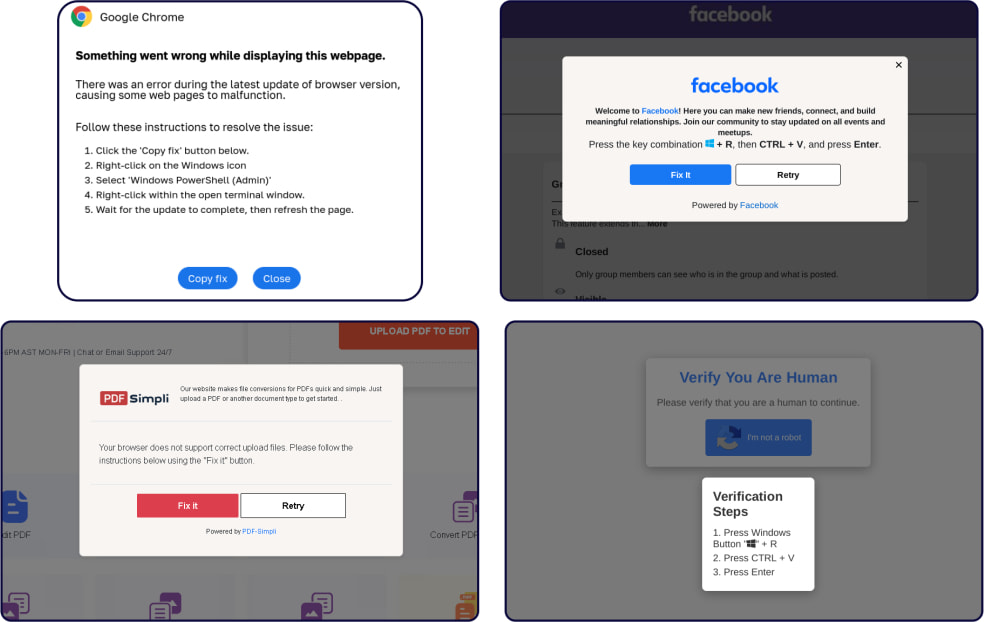
ClickFix was first identified by researchers from Proofpoint in early 2024, while subsequent campaigns were also documented by McAffee last summer. Initially, ClickFix targeted users with fake error messages, leading them to copy malicious PowerShell scripts into their systems.
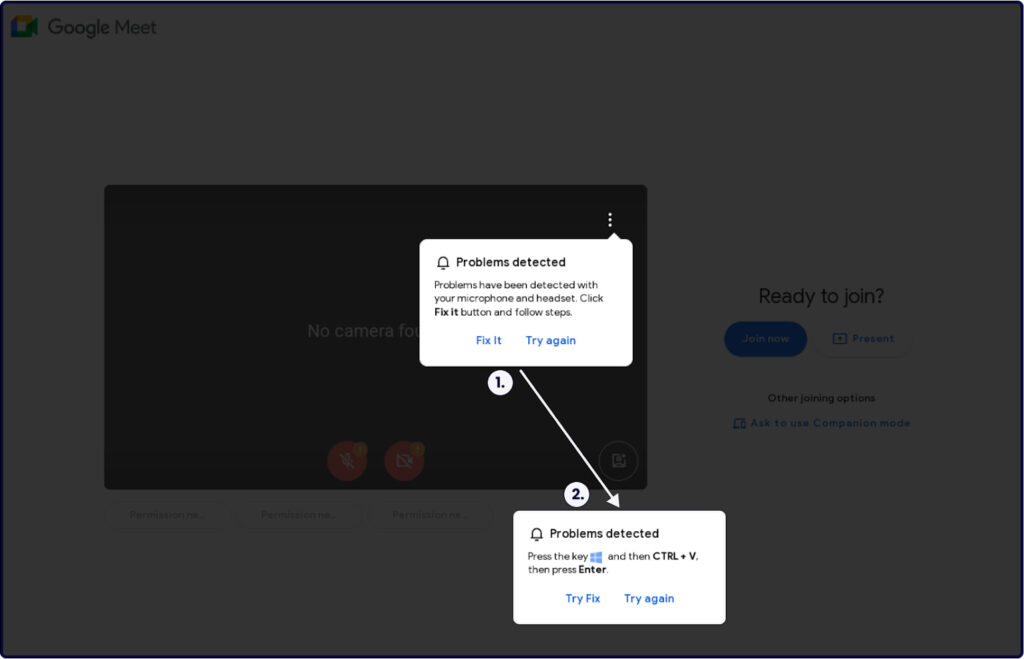
More recent attacks seen by Sekoia mimic legitimate Google Meet video conference pages, tricking victims into downloading malware by presenting fake pop-ups about technical issues with their microphones or headsets.
Sekoia
These pages, which appear nearly identical to legitimate Google Meet login pages, are hosted on phishing domains designed to resemble Google URLs, such as meet.google.webjoining.com and googiedrivers.com.
Sekoia
Sekoia analysts linked this campaign to two major cybercrime groups: “Slavic Nation Empire (SNE)” and “Scamquerteo,” both of which are sub-teams of larger cryptocurrency scam groups, Marko Polo and CryptoLove. These groups use the ClickFix lure to target individuals and businesses, primarily focusing on stealing sensitive information, including financial data, cryptocurrency wallets, and credentials.
Sekoia
Malware distribution tactics
The ClickFix campaigns deploy a variety of malware depending on the victim's operating system:
- Windows users are typically infected with Stealc and Rhadamanthys, distributed via malicious executables (stealc.exe and ram.exe). The infection begins when users click on a “Try Fix” button on the fake Google Meet page, triggering the download of an HTML file with obfuscated VBScript that initiates the infection chain.
- macOS users are targeted with AMOS Stealer, a less common infostealer for macOS, which is delivered through a malicious .dmg file (Launcher_v1.94.dmg). The infection chain is triggered by similar fake error messages, and the payload is downloaded via compromised websites.
The malware is distributed using a sophisticated infrastructure involving multiple phishing domains and C2 servers. For example, the C2 server for Stealc is hosted at 95.182.97[.]58, and Rhadamanthys connects to 91.103.140[.]200. These campaigns are further protected by traffic redirection services and evasion techniques designed to bypass security filters.
Traffers teams and their role
The ClickFix cluster has been linked to traffers teams, cybercriminal affiliates who distribute malware and scams. The Slavic Nation Empire (SNE) and Scamquerteo teams have been using ClickFix infrastructure to spread malware, working together to share phishing domains and tools. SNE primarily targets cryptocurrency assets, Web3 applications, and decentralized finance platforms, while Scamquerteo focuses on a wider range of victims.
Sekoia's investigation into Telegram chat logs associated with these traffers revealed detailed discussions between key players in these cybercriminal groups, including a developer named “sparkhash” who appears to have created and managed the fake Google Meet cluster.
Broader implications
The use of fake Google Meet pages in this campaign represents a significant threat to organizations that rely on Google Workspace, especially amid the growing popularity of remote work. By mimicking a widely trusted service, attackers can easily deceive users into executing malicious files, bypassing traditional security measures.
While the ClickFix technique initially involved convincing users to execute PowerShell commands, its evolution toward mimicking corporate platforms like Google Meet highlights the attackers' increasing sophistication. This technique exploits trust in cloud services, posing a risk to corporate and individual users alike, especially in cryptocurrency and Web3 ecosystems.







Leave a Reply