
FreeVPN.One, a Chrome extension with over 100,000 installs and a verified badge on the Chrome Web Store, is exposed by researchers for taking screenshots of users’ screens and exfiltrating them to remote servers.
A Koi Security investigation of the VPN tool reveals that it has been capturing full-page screenshots from users’ browsers, logging sensitive visual data like personal messages, financial dashboards, and private photos, and uploading it to aitd[.]one, a domain registered by the extension’s developer.
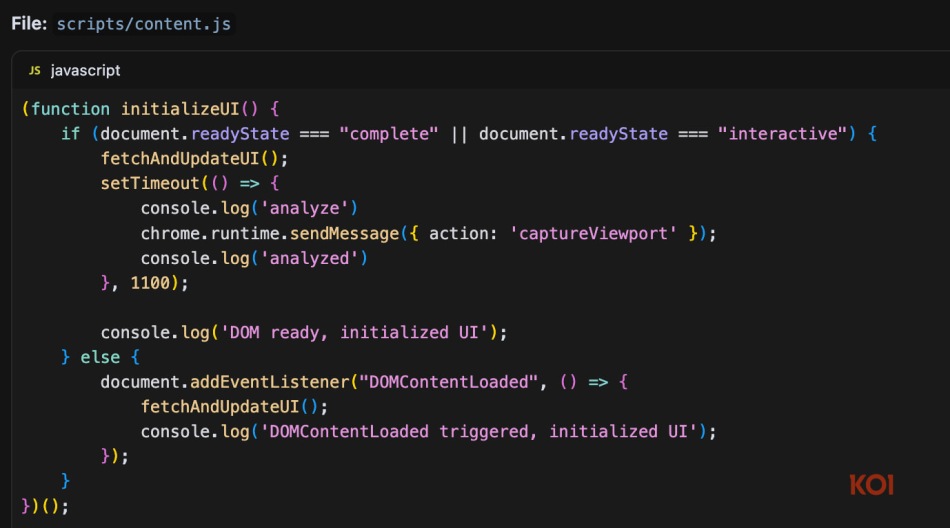
Koi Security's forensic analysis showed that the surveillance mechanism is triggered automatically, within seconds of loading any web page. Using Chrome’s privileged chrome.tabs.captureVisibleTab() API, screenshots are silently taken in the background and bundled with metadata including page URLs, tab IDs, and unique user identifiers. This data is then transmitted to the attacker-controlled server aitd.one/brange.php, without user interaction or visible indication.
The spying behavior is powered by a two-stage architecture:
- A content script injected into every visited site using matches (http:///, https:///).
- A background service worker that listens for an internal captureViewport message and initiates the screenshot capture.
Koi Security
The extension also promotes an “AI Threat Detection” feature which, when clicked, captures another screenshot and sends it to aitd.one/analyze.php. However, the real issue lies in the fact that screenshots are being taken long before users ever interact with this feature, making the user interface a decoy.
Koi Security further explains that the latest version of the extension, v3.1.4, introduced AES-256-GCM encryption with RSA key wrapping to obfuscate the exfiltrated data, making it harder to detect or analyze with network monitoring tools.
Specifically, the researchers presented the timeline below of FreeVPN.One development that turned it from a privacy protection tool to a privacy risk:
- April 2025 (v3.0.3): Extension requests, a step that broadens surveillance capabilities, but no spying yet.
- June 2025 (v3.1.1): Introduction of “AI Threat Detection” branding; content scripts expand to all websites; scripting permission added.
- July 17, 2025 (v3.1.3): The spyware activates. Screenshots, location tracking, and device fingerprinting begin.
- July 25, 2025 (v3.1.4): Exfiltration is encrypted, evading detection tools.
Developer rejects claims
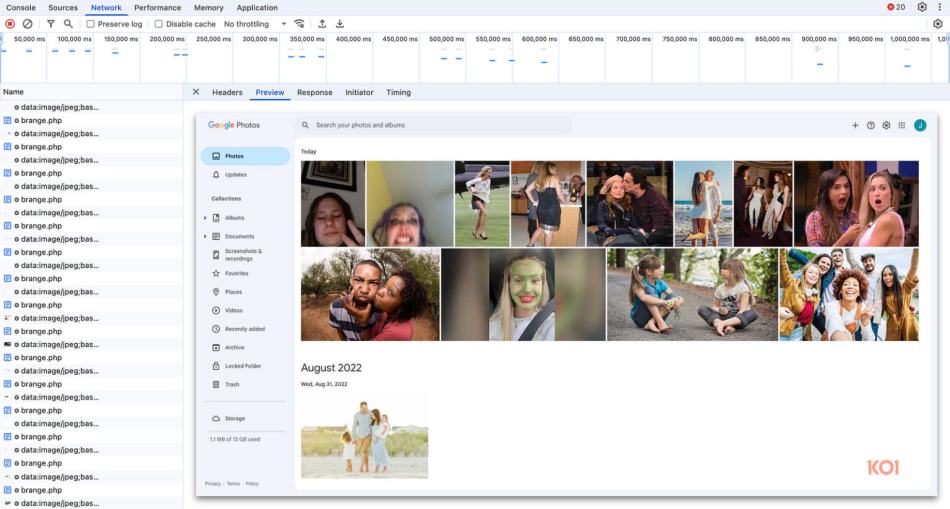
The extension’s developer claimed to Koi Security that the background screenshot functionality is part of a “security scan” intended to detect threats. Yet, Koi Security found the tool indiscriminately captured data from safe and commonly used sites such as Google Sheets, banking portals, and photo galleries. The developer also claimed screenshots are not stored but merely analyzed by AI tools, yet offered no verifiable way to confirm this.
Koi Security
Further scrutiny of the publisher revealed no legitimate company presence, according to Koi Security. The domain phoenixsoftsol.com, linked to the developer’s contact email, leads to a free-tier Wix page devoid of any corporate details or transparency.
Reportedly, after initially responding to questions, the developer ceased communication with the researchers.
FreeVPN.One is still listed and available on the Chrome Web Store at the time of writing, maintaining its verified status.
CyberInsider
CyberInsider has also reached out to the publisher for comment, but has not received a response as of publication. Hence, we could not verify their intentions and whether there’s real malice or they just implemented a security system in a risky way.
In any case, it would be advisable to change passwords for any services accessed through Chrome while the extension was active on your browser, and consider using independently audited VPN providers with transparent privacy policies and data handling practices.







Just had a look at the Chrome store and they’ve taken it down \o/ (UK) – well found
I gave up on microsoft products and operating systems long ago, for this reason… Spying…
lol but guys, I thought Google was safe!
I would think that they would vet these malware extension a little better since they don’t want any competition in the “we are surveilling you” market.
Great article, Bill; thanks! Browser extensions are a worry!
Well, its free snd not independently vetted by anybody so, why is anyone surprised?
Oof