
Security researcher mr.d0x has detailed two powerful techniques that can be abused to spy on users by exploiting Chrome-based browsers.
While the methods are not remote exploits, and require local access to the target machine, they provide a stealthy way for malware operators to silently monitor screen activity, take webcam snapshots, and record microphone audio once the initial infection has occurred.
The researcher discovered the methods while exploring Chromium’s command-line options to find interesting post-compromise use cases. He discovered that the –auto-select-desktop-capture-source flag, when combined with JavaScript using the getDisplayMedia API, allows a browser to automatically share the user’s full screen without user interaction. Normally, browsers show a selection prompt and require a user gesture to start screen sharing, but this flag bypasses that safeguard.
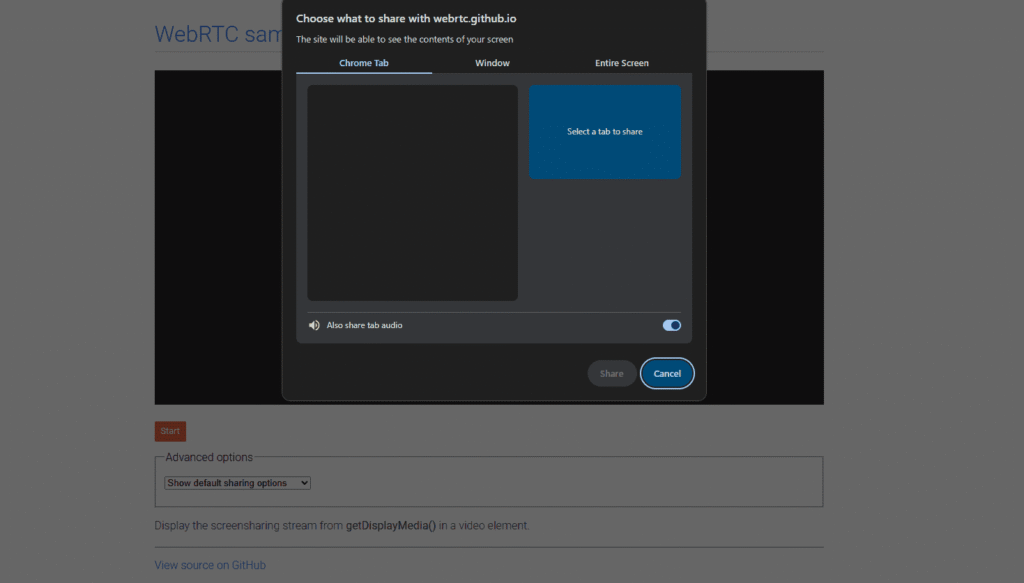
The attack setup involves launching the browser from the command line with the right flags, navigating it to a malicious website, and running JavaScript that continuously takes screenshots from the screen stream. The images are then base64-encoded and posted to a remote server via a backend PHP script (upload.php). This can happen in near real-time, with snapshots taken every three seconds, providing an attacker with a running visual feed of the victim’s screen.
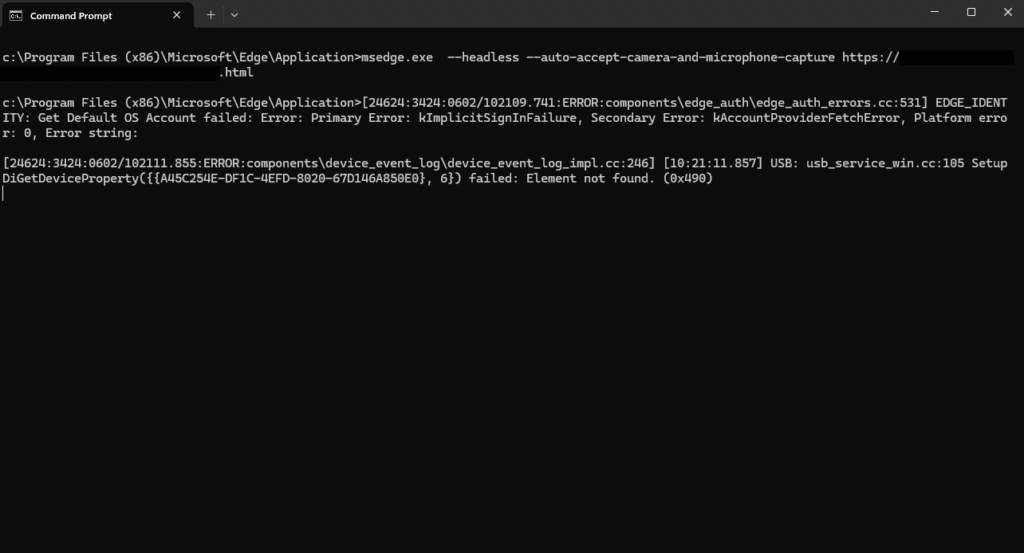
To make the spying even more discreet, the attacker can run the browser in headless mode (using the –headless flag), making the browser window invisible and avoiding on-screen cues that screen sharing is active. Alternatively, the browser can be launched in a tiny off-screen window using –window-position=-10000,0 –window-size=1,1. While this second method produces higher-quality screenshots, it briefly shows a GUI notice that the screen is being shared, making it slightly riskier for stealth operations.
The second technique focuses on the user’s camera and microphone. Here, mr.d0x demonstrated that the –auto-accept-camera-and-microphone-capture flag can be used alongside the getUserMedia API to bypass the usual permission prompts for camera and mic access. Once launched with this flag, a Chromium browser will grant full access to the webcam and microphone streams without the user needing to click “Allow” on any dialog boxes.
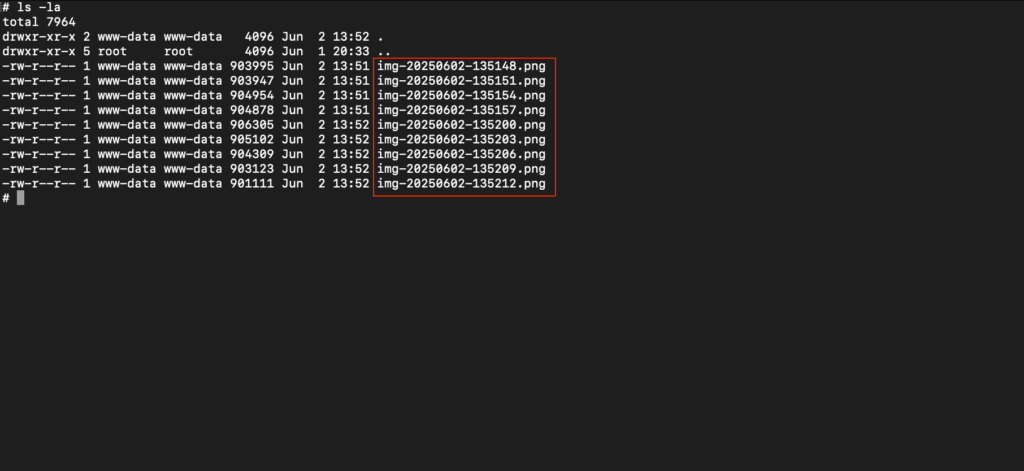
The accompanying attack script captures webcam snapshots every few seconds and uploads them to the server, just like the screen captures. In a more advanced setup, the script also records 60-second audio segments using the microphone, saving them as .webm files and sending them to a separate PHP endpoint (upload-mic.php). The collected media files, both audio and video, are stored on the attacker-controlled server, offering continuous monitoring capabilities.
It is important to stress that these attacks do not work remotely and require local code execution on the victim’s machine, meaning the attacker already needs a foothold, typically gained through malware infection or insider access. However, once that foothold is established, these techniques offer a low-friction, largely invisible way to monitor user activity without needing to deploy separate spyware tools.
Chromium-based browsers, including Google Chrome, Microsoft Edge, Brave, and Opera, together represent over 70% of the global desktop browser market. Their vast user base and reliance on shared Chromium components mean such abuse paths, while niche, carry significant post-compromise surveillance potential.







Leave a Reply