
A network of at least 35 hidden Chrome extensions with over 4 million combined installations exhibits behaviors consistent with spyware or information-stealing tools.
These extensions request excessive permissions, perform obfuscated tracking, and allow remote server-controlled configurations — posing a significant threat to user privacy.
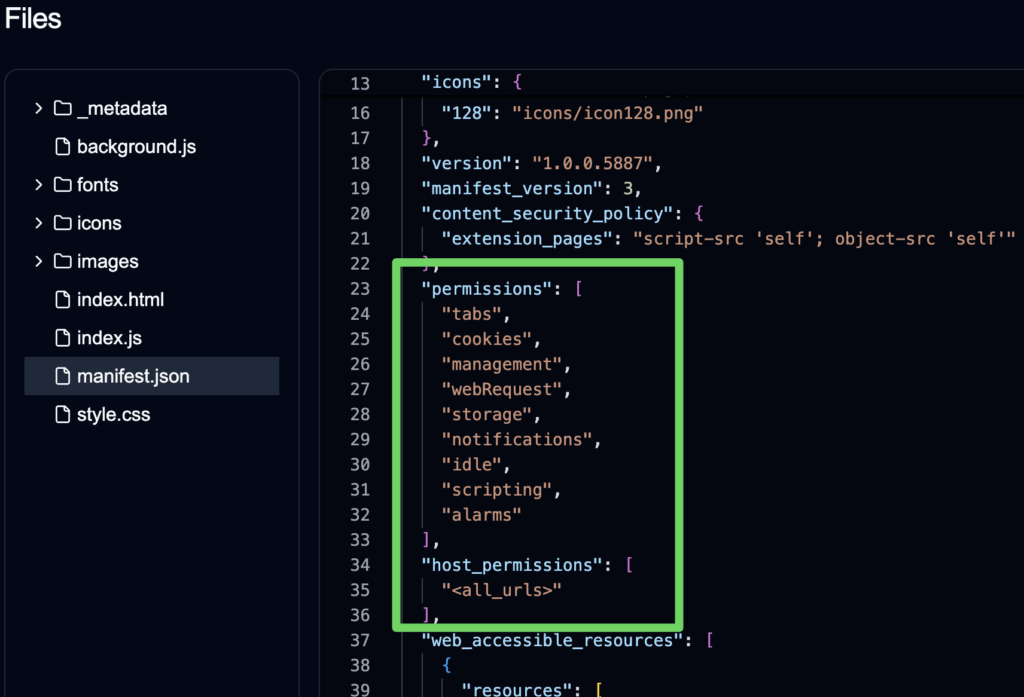
The investigation was conducted by SecureAnnex researcher John Tuckner, who initially reviewed a list of 132 browser extensions flagged for monitoring. He noticed several unlisted Chrome Web Store extensions — a distribution method often used by enterprises but also abused by malicious actors to avoid detection. One such extension, Fire Shield Extension Protection, raised immediate concerns. Despite its unlisted status, it had 300,000 users and permissions far beyond what was necessary for its stated functionality.
A deeper analysis revealed that Fire Shield accessed cookies intercepted sensitive HTTP headers like ‘Authorization,' and could execute remote scripts. Secure Annex's AI-based code review confirmed multiple red flags, including connections to suspicious domains such as fireshieldit.com, and the presence of YARA signatures indicative of privacy-invasive behavior.
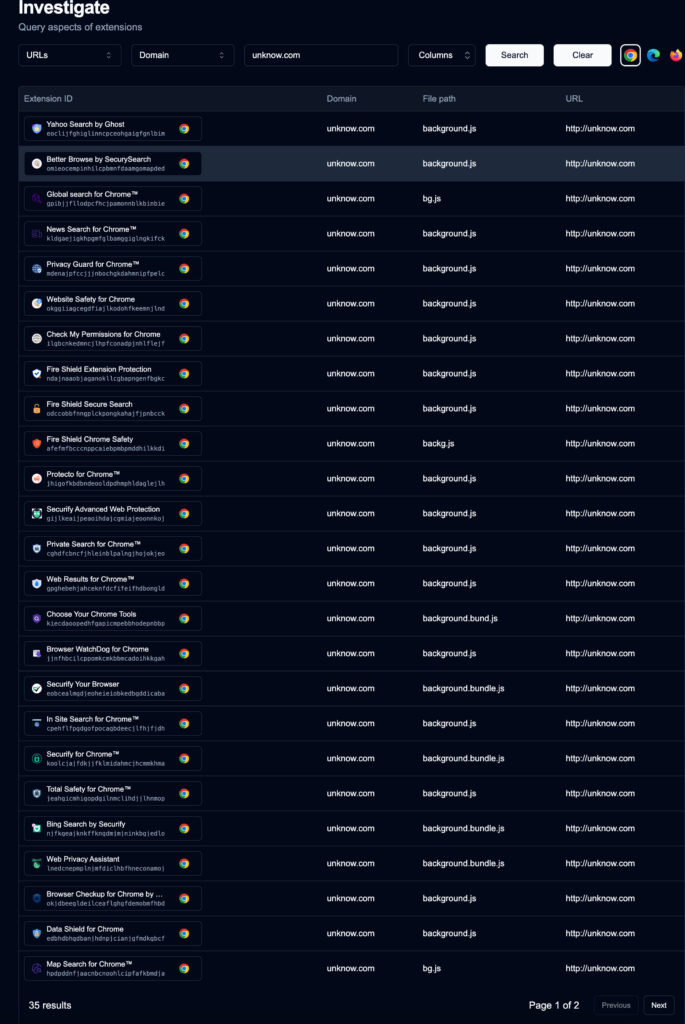
Further investigation exposed that this extension shared a background service domain — unknow.com — with 34 others, all bearing similar code patterns and manifest file permission hashes (permhashes). Although unknow.com had no functional purpose in the code, it became a pivotal clue in linking these extensions as part of the same malware ecosystem.
The ecosystem includes extensions masquerading as ad blockers, privacy tools, and productivity enhancers. Their functionality is either minimal or entirely absent, and in many cases, they are designed to silently log browser activity, manage tabs, retrieve cookies, and inject scripts from external sources.
Secure Annex identified several behaviorally distinct but technically similar extensions, including:
- Browse Securely for Chrome
- Web Privacy Assistant
- Cuponomia (a Brazil-based shopping extension resembling Honey)
- Watch Tower Overview
- Incognito Shield for Chrome
While Cuponomia presents a slightly more legitimate interface and business model, it still contains code capable of reading cookies and executing functions based on external server instructions. Uniquely, it uses AWS Lambda and Google Analytics for tracking, deviating from the more obfuscated approaches used by others in the group.
SecureAnnex
Despite subtle differences, all 35 extensions share the following key technical capabilities:
- Access to all cookies across domains
- Monitoring and manipulation of HTTP request headers
- Execution of remote scripts via iframe injection
- Overriding browser search settings to inject monetized redirects
- Remote configuration updates that can elevate surveillance intensity
While credential theft was not conclusively observed, the breadth of permissions and the remote configuration capabilities create a clear and ongoing risk. The possibility of escalating data collection behavior at a future time — or in response to user activity — aligns these extensions more closely with spyware than legitimate software.
SecureAnnex
Some of the extensions, including Watch Tower Overview and Incognito Shield for Chrome, were already delisted from the Chrome Web Store at the time of reporting. Many others, however, remain active, with several bizarrely marked as “Featured” by Google — a designation typically reserved for reputable software.
Several of these extensions have not been updated in over a year, suggesting long-standing persistence without scrutiny. Moreover, their unlisted status means they are not discoverable via search, raising questions about how they amassed millions of users. Possible vectors include malicious advertisements, bundling with freeware, or direct links from phishing campaigns.
It is recommended that users review the list of IDs SecureAnnex shared in the report to determine if they have any of the risky extensions installed and remove them immediately. Unless provided directly by a trusted source (e.g., enterprise IT), it is generally recommended to avoid installing unlisted Chrome extensions.







Google is the worst. There are countless spoofed extensions/add-ons that are named, look, and have all the same information including developer as the original. Google has pretty much eliminated reporting malware for extensions. They also removed the ability to flag bogus comments in the webstore. Should one be successful in reporting the extension, say, you live in a region that mandates Google to offer such reporting, any such report will take a year or so for Google to action, if ever. This is no joke.