
A sophisticated adversary-in-the-middle (AitM) attack campaign by a China-linked threat actor dubbed TheWizards, leverages IPv6 SLAAC spoofing to redirect legitimate software updates and infect victims with a modular backdoor known as WizardNet.
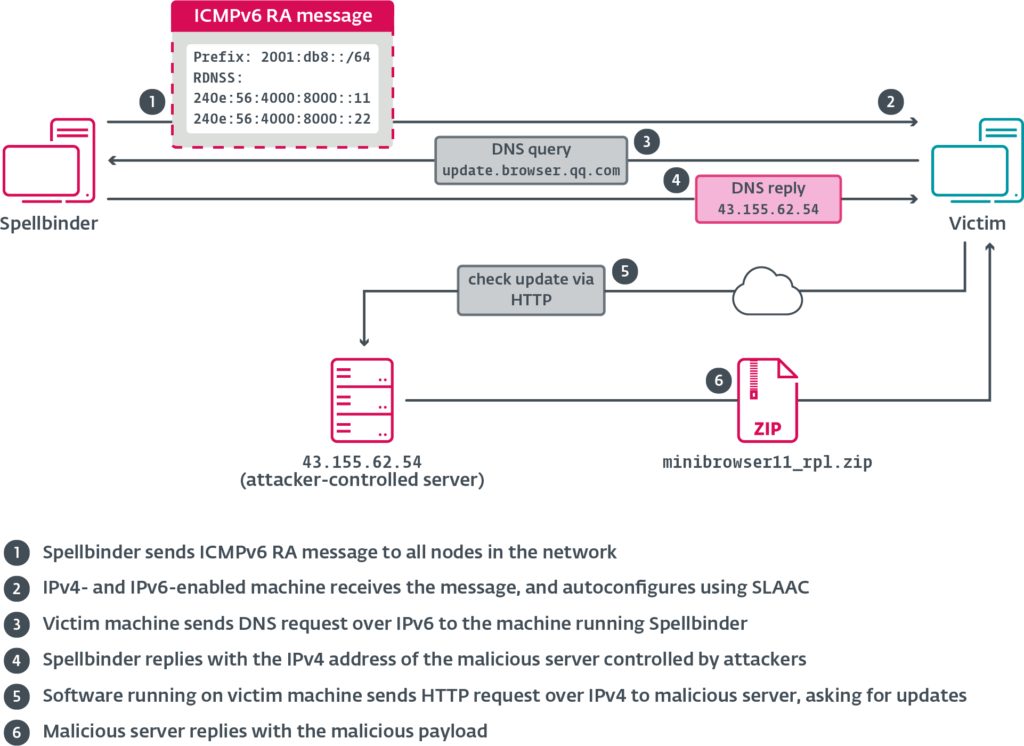
The campaign, active since at least 2022 and still ongoing as of 2024, centers around a custom-built tool named Spellbinder. This utility facilitates lateral movement within compromised networks by exploiting weaknesses in IPv6 stateless address autoconfiguration (SLAAC). Once inside a network, the attackers impersonate legitimate IPv6 routers using rogue ICMPv6 Router Advertisement (RA) packets. This technique, rooted in vulnerabilities discussed as early as 2008, effectively reroutes traffic to attacker-controlled infrastructure, enabling stealthy malware delivery and data interception.
ESET
Hijacking software updates
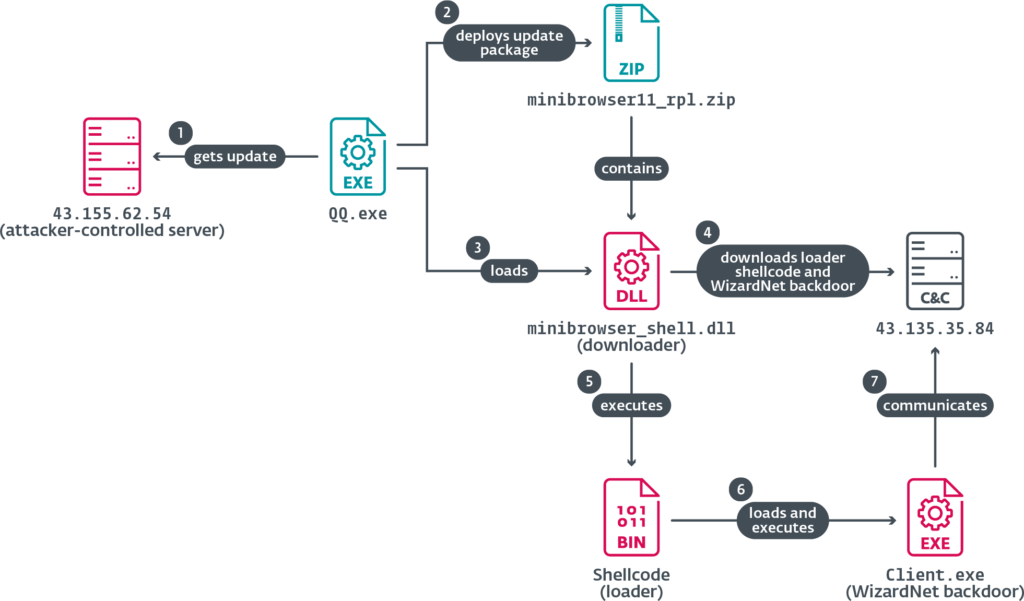
The operation was uncovered and analyzed by ESET, that detailed how TheWizards hijack update mechanisms in widely used Chinese software — including Tencent QQ and Sogou Pinyin — to deliver malware. In one illustrative case from 2024, the QQ.exe application’s DNS request to update.browser.qq.com was intercepted by Spellbinder, which replied with a spoofed DNS record pointing to a malicious server. The fake server returned JSON-formatted update instructions that triggered the download of a ZIP archive containing a malicious DLL. This DLL then launched a downloader, which retrieved and executed WizardNet in memory.
The initial infection chain is engineered with remarkable precision. The attackers package components into a ZIP archive named AVGApplicationFrameHostS.zip, dropping them into a phony AVG Technologies directory. Key components include winpcap.exe for packet capture and AVGApplicationFrameHost.exe — a renamed legitimate binary used to sideload a malicious DLL (wsc.dll) that executes shellcode from a log.dat file, decompressing and launching Spellbinder directly into memory.
Spellbinder uses the WinPcap library to monitor and intercept local traffic. It captures DNS, ARP, ICMPv6, and DHCPv6 traffic, selectively responding to targeted domains with forged responses. A hardcoded list of domains within Spellbinder includes Chinese tech giants like Tencent, Baidu, Youku, Xiaomi, Kingsoft, and Qihoo 360. In affected cases, fake update payloads include encrypted shellcode that disables AMSI and ETW logging, loads the .NET runtime, and ultimately executes WizardNet.
ESET
WizardNet malware
The WizardNet backdoor is modular, communicating over encrypted TCP or UDP sockets. It uses a uniquely generated SessionKey — based on system identifiers — for AES encryption. The implant can load and execute .NET modules in-memory, extract system metadata, list running processes associated with antivirus solutions, and maintain persistence through Windows registry keys. Its command set supports loading, invoking, and unloading remote modules, as well as transmitting detailed system reports back to command and control servers.
Victim telemetry indicates TheWizards’ operations span China, Hong Kong, Cambodia, the Philippines, and the UAE, targeting individuals and gambling-related entities. Notably, the infrastructure and payloads used differ from other China-linked threat groups. However, ESET’s analysis highlights technical and operational overlaps with malware attributed to the Chinese company Sichuan Dianke Network Security Technology Co., Ltd. (also known as UPSEC). UPSEC has previously been linked to the DarkNimbus (or DarkNights) malware — used against Android devices — and was identified as a vendor to another group, Earth Minotaur, by Trend Micro and Intelligence Online.
Though ESET has not observed TheWizards targeting Android users directly through its telemetry, they obtained malicious update instructions designed to deliver DarkNights to mobile users. This aligns with broader evidence suggesting UPSEC may act as a malware supplier across multiple Chinese cyberespionage operations.







Leave a Reply