
This flaw allows attackers to extract VPN credentials directly from memory, a tactic used in conjunction with the DEEPDATA malware to gather sensitive information from compromised systems. Despite being reported to Fortinet in July 2024, the issue remains unresolved.
Discovery and Fortinet's inaction
Volexity's researchers identified the zero-day vulnerability during the analysis of the DEEPDATA malware family. DEEPDATA is a modular post-exploitation tool designed for Windows, capable of extracting credentials, recording audio, and gathering information from various applications. The vulnerability was confirmed to affect FortiClient version 7.4.0 but did not impact older versions. Fortinet was notified on July 18, 2024, acknowledging the issue six days later, but a CVE has yet to be assigned.
BrazenBamboo, a suspected Chinese state-affiliated group, is attributed to developing DEEPDATA alongside other malware families such as LIGHTSPY and DEEPPOST. These malware tools have been observed targeting multiple platforms, including Windows, macOS, and iOS, emphasizing BrazenBamboo's advanced capabilities and cross-platform reach.
Details of the vulnerability
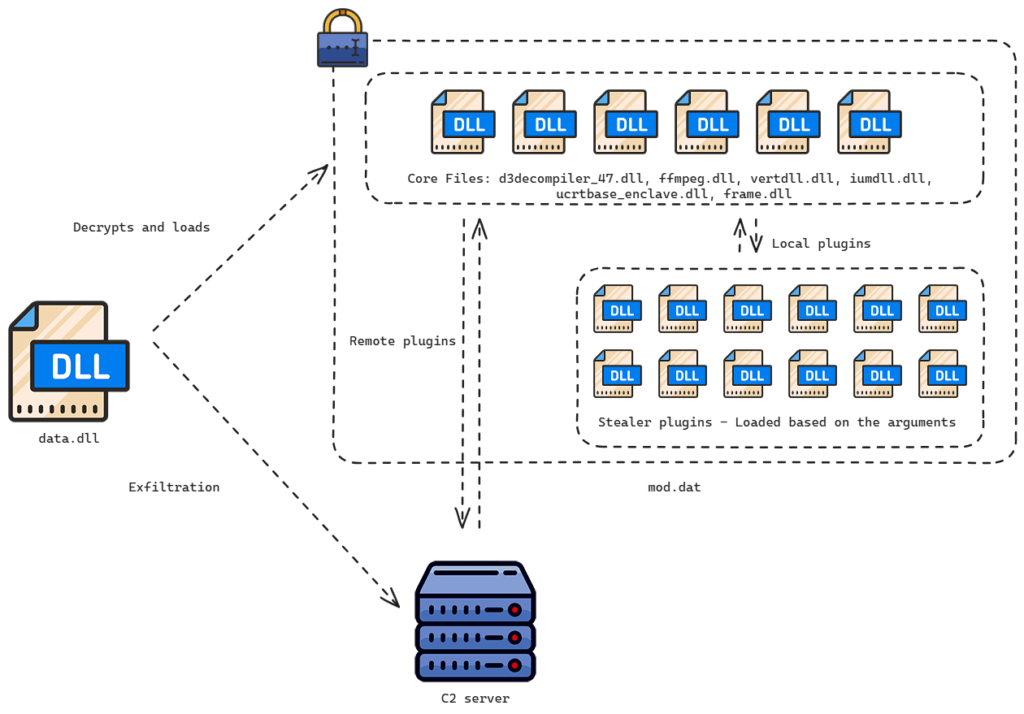
The vulnerability resides in FortiClient’s handling of user credentials in process memory. DEEPDATA’s specialized FortiClient plugin leverages this flaw to retrieve usernames, passwords, remote gateways, and ports stored in JSON objects within the client’s memory. The plugin exploits the vulnerability using a library named msenvico.dll and supports credential theft from over a dozen other sources, including popular applications like Outlook, Telegram, and WeChat.
The DEEPDATA malware comprises several core components and plugins:
- Core files include frame.dll (plugin orchestrator), iumdll.dll (WeChat data collector), and ffmpeg.dll (enables 32-bit code execution in 64-bit processes).
- Plugins extract data from various sources, including web browsers, instant messaging apps, and system logs.
Volexity
Rich toolkit, domestic ops
BrazenBamboo’s toolkit extends beyond DEEPDATA. The group has developed LIGHTSPY, a multi-platform malware family initially identified in 2020. Recently, Volexity documented a new Windows variant of LIGHTSPY that deploys a sophisticated execution chain using encoded files and in-memory code execution. The malware supports a range of functionalities, from keystroke logging to webcam surveillance.
DEEPPOST, another tool in BrazenBamboo’s arsenal, facilitates data exfiltration through encrypted HTTPS channels. Its ability to upload files from compromised devices further underscores the group's operational sophistication.
Volexity also identified six active command-and-control (C2) servers associated with DEEPDATA and 26 linked to LIGHTSPY. The infrastructure employs unique URL patterns and ports for managing plugins, orchestrating attacks, and exfiltrating data. The researchers noted poor operational security in the infrastructure, suggesting a focus on domestic surveillance rather than covert foreign intelligence operations.
To defend against the BrazenBamboo threat, Volexity recommends system auditing for exposed credentials, blocking of known IoCs, and application of strict endpoint monitoring to mitigate post-exploitation risks.







Leave a Reply