
Check Point's Quantum Security Gateways have become the focus of a significant threat activity as hackers are now actively exploiting a critical vulnerability using publicly available exploits.
The issue came to light last week, when Check Point Cybersecurity alerted customers to an increase in attacks targeting VPN devices. Follow-up investigations revealed the root cause as CVE-2024-24919, a high-severity information disclosure flaw that hackers have leveraged as a zero-day to gain remote access to firewalls and potentially infiltrate corporate networks.
Vulnerability exploitation
CVE-2024-24919 is a path traversal vulnerability in Check Point's CloudGuard Network Security appliance, involving the improper implementation of the strstr function in the HTTP request handler at the /clients/MyCRL endpoint.
This flaw allows attackers to craft paths with traversal sequences, such as “../”, to bypass controls and access sensitive files. Exploiting this vulnerability requires no user interaction or privileges, making it particularly dangerous.
By sending specially crafted HTTP POST requests, attackers can manipulate the path to read arbitrary files on the system, including critical files like /etc/shadow. Security firm Wallarm reported detecting and blocking over 13,000 attacks exploiting this vulnerability within the first two days following its public disclosure.
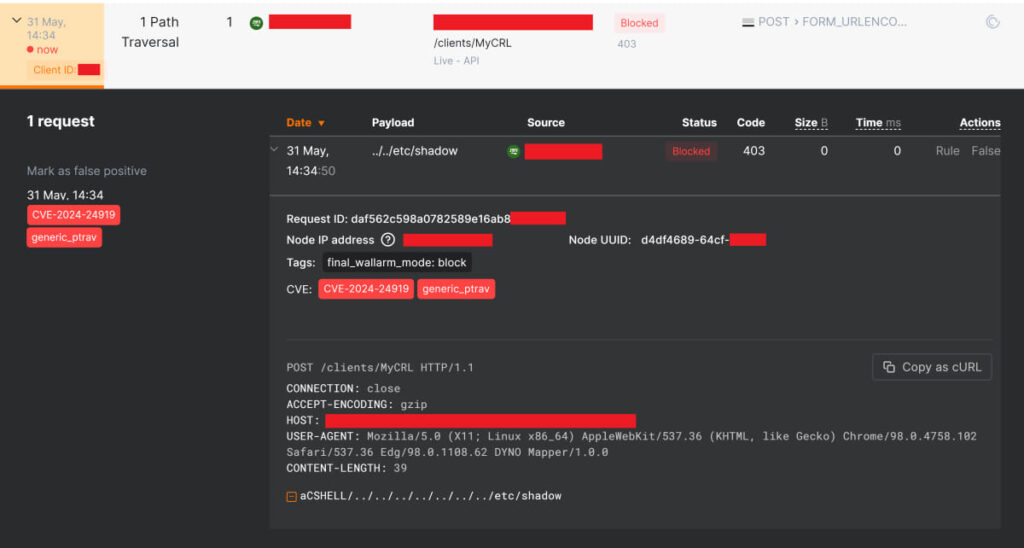
Wallarm
Scope of impact
As of May 31, 2024, Censys observed over 13,800 internet-facing devices globally that potentially expose this vulnerability. The affected products include:
- CloudGuard Network
- Quantum Maestro
- Quantum Scalable Chassis
- Quantum Security Gateways
- Quantum Spark Appliances
Specific versions impacted are R80.20.x, R80.20SP, R80.40, R81, R81.10, R81.10.x, and R81.20. A significant number of these exposed devices are located in Japan and Italy, with Japan hosting 6,202 of these systems.
Censys
Mitigation
Check Point has issued hotfixes to address CVE-2024-24919. Users are urged to update their systems immediately to mitigate the threat. The steps to apply the hotfix are:
- Navigate to the Security Gateway portal.
- Go to Software Updates.
- Select Available Updates.
- Click on Hotfix Updates.
- Install the updates.
In addition to applying the hotfix, Check Point recommends several security measures, including assessing and disabling unused local accounts, implementing multi-factor authentication for necessary local accounts, and regularly monitoring and adjusting VPN configurations for optimal security.
Check Point criticism
While Check Point has released updates soon after the discovery of the zero-day flaw, there has been criticism regarding the downplaying of the vulnerability's severity. Experts at Watchtowr argue that the advisory's language minimizes the risk, which is, in reality, a full unauthenticated arbitrary file read that can lead to credential theft and potential network compromise.
With active exploitation of CVE-2024-24919 in the wild, it is crucial for administrators of Check Point's Quantum Security Gateways to apply the hotfixes immediately and follow recommended security practices to protect their networks.







Leave a Reply