
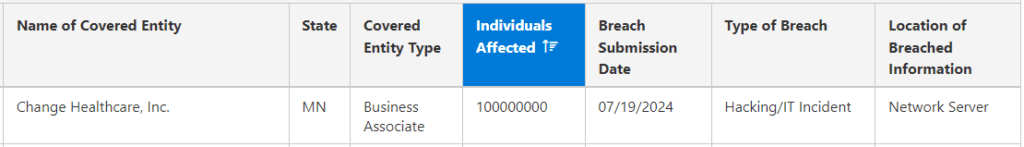
The cyberattack on Change Healthcare, a key subsidiary of UnitedHealth Group, has potentially compromised the personal information of 100 million individuals across the United States.
The breach, which occurred in February, was classified as a hacking/IT incident affecting the company's network servers, marking one of the largest healthcare-related breaches in recent history.
The cyberattack targeting Change Healthcare was linked to the ALPHV ransomware group, also known as BlackCat. In this latest disclosure to the U.S. Department of Health and Human Services (HHS), Change Healthcare revealed that a staggering 100 million individuals could have had their protected health information (PHI) and personally identifiable information (PII) compromised. The breach involved unauthorized access to sensitive data on the company's network servers.
The healthcare organization had submitted a report to the government portal on July 19, but without including a number of affected individuals back then. This figure was added today, setting the tally to a staggering 100,000,000 people.
Cyberattack details
In February 2024, Change Healthcare was targeted by BlackCat, using stolen credentials to gain access to a Citrix portal without multi-factor authentication (MFA). Over nine days, the attackers moved laterally within the network, stealing data and deploying ransomware. While UnitedHealth Group took swift action to isolate infected systems, significant damage had already been done.
UnitedHealth Group CEO Andrew Witty testified before Congress, detailing how Change Healthcare's IT infrastructure was significantly impacted, with payment processing, pharmacy claims, and other critical services disrupted. The company has since been collaborating with top security experts from firms like Microsoft, Google, and Palo Alto Networks to rebuild its systems and enhance cybersecurity.
Despite extensive recovery efforts, the cyberattack exposed millions of sensitive records, with reports indicating that stolen data may have been circulating on the dark web. Earlier this year, another ransomware group, RansomHub, claimed to have obtained four terabytes of data from Change Healthcare, including military personnel records, dental and medical information, and payment processing files.
Massive impact on Americans
Change Healthcare is a major business associate in the U.S. healthcare system, processing millions of medical claims and transactions daily. The company serves numerous high-profile clients, including Medicare, Tricare, and CVS-Caremark. Given its role in the healthcare ecosystem, any disruption to Change Healthcare's operations has wide-reaching implications for the U.S. healthcare system.
The company processes insurance claims and payments for numerous hospitals, pharmacies, and medical practices, meaning that such a breach could lead to cascading effects on healthcare providers and patients alike.
While the specifics of the data compromised in this breach have not been fully disclosed, prior reports suggest that both PHI and PII are likely involved. This could include:
- Names, addresses, and Social Security numbers
- Medical treatment and diagnosis information
- Insurance claims and payment details
- Data from affiliated organizations, including Medicare and other health insurers
Given the magnitude of this breach, individuals who may be affected are encouraged to take proactive steps to protect their personal information, such as activating credit monitoring and identity theft protection services, changing their account passwords, enabling multi-factor authentication, and keeping an eye on medical bills and insurance claims for any unusual activity.







Leave a Reply