
Central Tickets, a UK-based seat-filling service, confirmed a data breach affecting over 722,860 accounts. The breach, originally listed on a hacking forum in July 2024, exposed sensitive data, including names, email addresses, phone numbers, IP addresses, purchases, and hashed passwords.
Breach details and impact
The breach reportedly occurred on July 1, 2024, taking advantage of a poorly secured database. The exposed database contained email addresses, customer names, mobile numbers, IP addresses, device information, and purchase histories. Most concerning was the inclusion of hashed account passwords. These passwords were stored using SHA-1 hashing — a weaker hashing algorithm without added salts — and hence posed a significant risk to users.
The breach impacted customers who used Central Tickets, a platform founded in 2017 that connects productions with audiences, including underserved groups, through a socially and climate-responsible approach to ticket distribution.
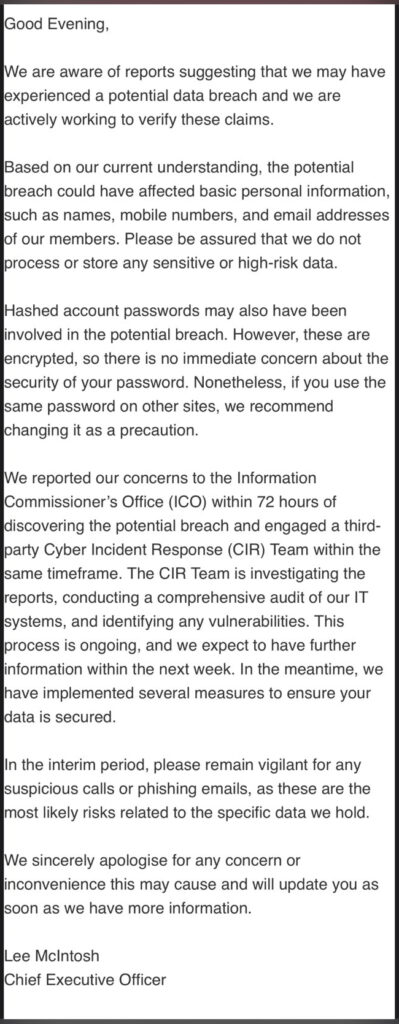
Central Tickets informed impacted users through a letter, acknowledging the situation and offering transparency. In the message, Chief Executive Officer Lee McIntosh noted:
“Based on our current understanding, the potential breach could have affected basic personal information, such as names, mobile numbers, and email addresses of our members… Hashed account passwords may also have been involved in the potential breach.”
The company emphasized that these hashed passwords were encrypted, thus reducing immediate security concerns. However, users were advised to change their passwords as a precautionary measure, especially if they used similar passwords across other sites.
@jonathanitb
Additionally, Central Tickets promptly reported the breach to the Information Commissioner's Office (ICO) within 72 hours of discovery, engaging a third-party Cyber Incident Response (CIR) team to thoroughly investigate their systems and identify any vulnerabilities. The CIR team is currently working to secure the data and provide further updates.
Attempted sale and eventual leak
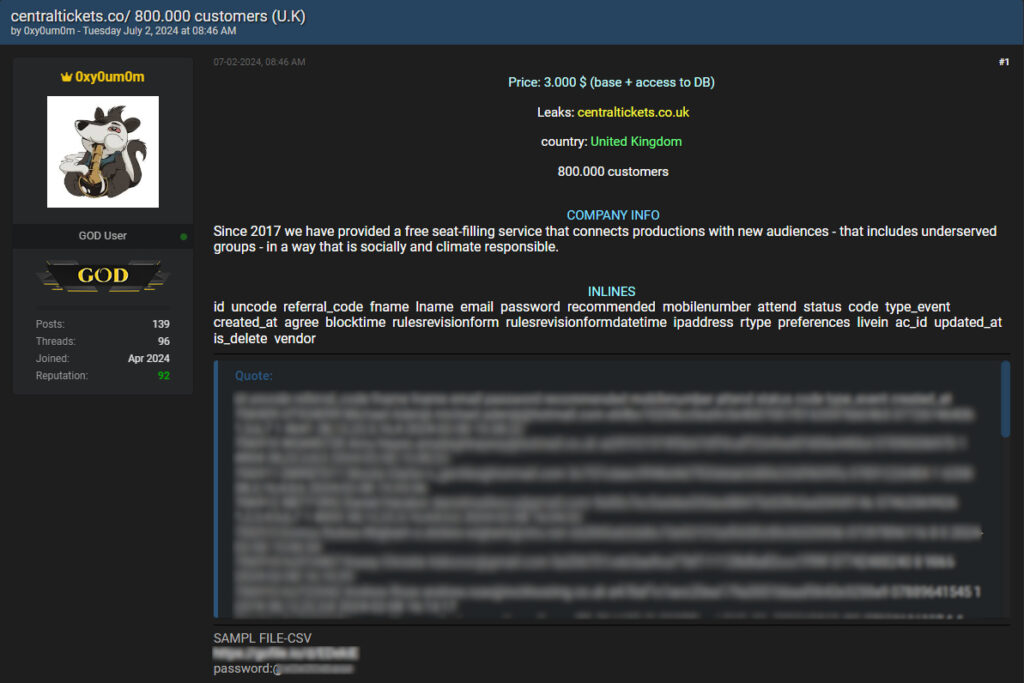
The breach was initially posted on July 2, 2024, by a user under the alias “0xy0um0m” on BreachForums. The post claimed access to the details of 800,000 customers and offered the data for $3,000, including access to the database. The data set included names, emails, mobile numbers, and passwords hashed with SHA-1 without salting. It also included other personal details such as account creation dates, attendance, and status codes related to ticket purchases.
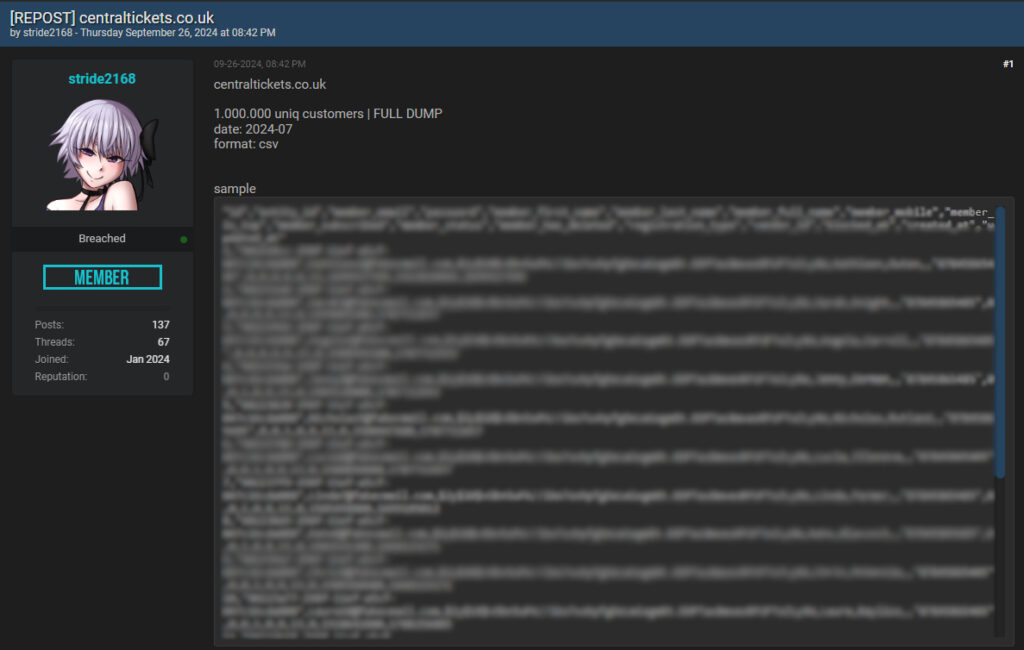
A few months later, another forum user, “stride2168,” freely leaked the data dump containing what was reported as one million unique customer records, marking the information as fully public.
HIBP alerts users
According to HIBP, a reputable data breach notification platform, the database actually included a total of 722,860 compromised accounts and was added to its records on September 30, 2024. The data was categorized as containing device information, email addresses, IP addresses, passwords, phone numbers, and purchase details. The inclusion of unsalted SHA-1 hashed passwords in the data has raised security concerns due to the relatively insecure nature of the hashing method.
The data breach tracking platform also reported that roughly 80% of the exposed people were already in its database from previous security incidents, so for about 144,500, this was the first time they had their information compromised.







Leave a Reply