
A recent analysis by XLab's cybersecurity threat monitoring system has revealed a significant increase in activity by the CatDDoS botnet group over the past three months.
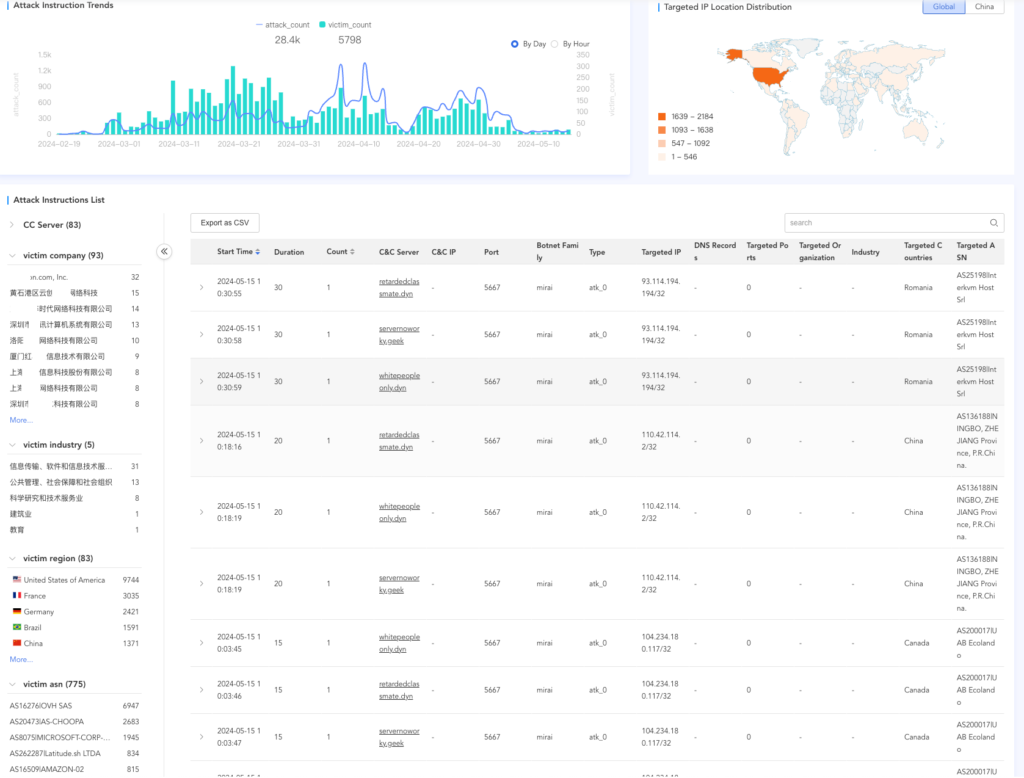
The botnet has been exploiting over 80 known vulnerabilities and targeting more than 300 entities daily at its peak, mostly focusing in the United States.
XLab's threat detection system, which continuously monitors active DDoS botnet families, has recorded a surge in CatDDoS activity. This botnet group has been actively exploiting various vulnerabilities in various devices and services, making it a notable threat in the cybersecurity landscape.
In the past three months, CatDDoS has exploited over 80 known vulnerabilities. The affected vendors and products include:
- Cameras: A-MTK, Avtech, Barni, Billion, LILIN, MVPower, Shenzhen TVT
- Firmware: Cambium Networks, Cisco, D-Link, DrayTek, Fastweb, Huawei, Netgear, TP-Link, Zyxel
- Software: Apache (ActiveMQ, Log4j, RocketMQ), FreePBX, GitLab, Jenkins, ThinkPHP
- Others: Realtek SDK, SonicWall Global Management System, Seagate Blackarmor NAS, Tenda routers
The botnet group also uses several zero-day vulnerabilities, identified through sample run parameters such as “skylab0day.”
CatDDoS targets were distributed globally, focusing on industries like cloud services, education, research, information transmission, public administration, and construction. Notable incidents include multiple DDoS attacks against “Shanghai X Network Technology Co., Ltd.” on April 7, 2024. These attacks lasted 60 seconds each and used an internal attack type labeled “atk_0.”
XLabs
CatDDoS evolution
CatDDoS is a variant of the Mirai botnet, named for its frequent use of “cat” and “meow” in domain names and samples. It first appeared in August 2023. Recent samples show little change in communication methods compared to earlier versions. The botnet is suspected to be a successor to the Aterna Botnet, which was shut down in December 2023. The source code leak of Aterna led to new variants like RebirthLTD, Komaru, and Cecilio Network.
The v-snow_slide variant was first discovered in October 2023. It retained much of the code from the Fodcha botnet and used similar encryption and communication protocols. This variant expressed disdain for security vendors through offensive strings in its code.
CatDDoS variants often share the same source code, leading to similar configurations and encryption methods. At least three other botnet families use the same chacha20 encryption algorithm with identical keys and nonces. These include Hailbot, Woodman, and Vapebot.
CatDDoS and other botnet variants frequently attack each other's C2 infrastructure, indicating ongoing conflicts between different botnet operators. Examples include multiple attacks between servers associated with RebirthLTD and other botnet families.
The CatDDoS botnet remains a significant threat due to its widespread activity and exploitation of numerous vulnerabilities. Continuous monitoring and timely patching of affected systems are essential to mitigate the impact of such botnets.







Leave a Reply