
A large-scale cybercriminal operation known as BADBOX is spreading pre-installed malware on Android-based devices, including smartphones, TVs, and tablets, sold through major retailers like Amazon, eBay, and AliExpress. Despite earlier attempts to dismantle the botnet, recent findings from Bitsight indicate that BADBOX remains active and larger than previously thought, compromising over 192,000 devices globally.
BADBOX operational overview
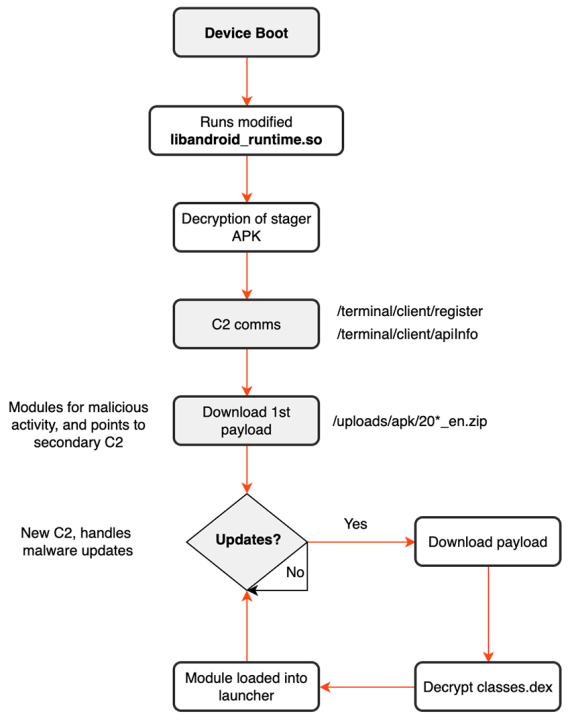
The BADBOX operation leverages compromised firmware on Android devices, enabling malware installation before the devices reach consumers. Upon booting, these devices connect to malicious command-and-control (C2) servers, allowing cybercriminals to:
- Deploy secondary payloads for remote module installation.
- Exploit devices as residential proxies for illicit activities.
- Commit ad fraud by generating fake interactions with online ads.
- Abuse user accounts for unauthorized purposes.
Researchers believe the infection occurs either as part of a supply chain attack — where malware is introduced during manufacturing or shipping — or as an intentional feature embedded by malicious actors. The malware shows strong resemblances to Triada, a stealthy firmware backdoor first identified in 2016, but BADBOX has evolved into a more potent threat.
Bitsight
Major brands impacted
Bitsight reveals that BADBOX has expanded to infect new device models, including the Yandex 4K QLED Smart TV and Hisense Instawall_T963 smartphone, alongside numerous off-brand Android devices. Telemetry shows:
- Over 160,000 infections involve previously unseen device models.
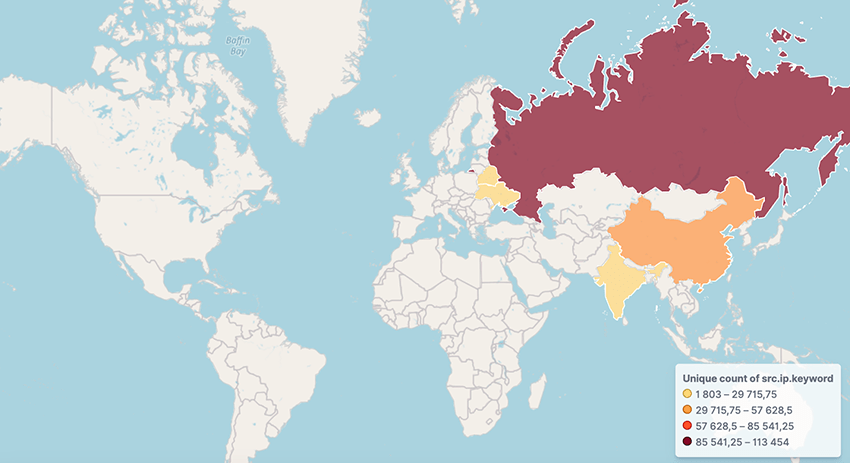
- The most affected regions include Russia, China, India, Belarus, Brazil, and Ukraine.
- A Yandex Smart TV model and Hisense smartphone collectively account for 85% of the recorded infections.
The scale of infection was highlighted in a recent operation by Bitsight, which sinkholed a BADBOX domain and observed traffic from 160,000 unique IP addresses within 24 hours, with numbers steadily increasing.
Bitsight
Germany’s Federal Office for Information Security (BSI) had previously disrupted a BADBOX variant affecting 30,000 devices in December 2024. This malware targeted digital photo frames and media players with outdated Android firmware. While that operation temporarily curtailed the botnet’s activity, it had minimal impact globally due to its limited geographic scope.
Bitsight’s research reveals that BADBOX is now targeting devices from established brands like Yandex, suggesting that the botnet’s operators are shifting their focus beyond low-cost, off-brand devices. This diversification raises concerns about the malware’s growing reach and sophistication.
Consumer security recommendations include purchasing devices only from trusted manufacturers and resellers, ensuring they are running the latest available software/firmware, and limiting their network exposure to the absolute minimum required for their functionality.







Leave a Reply