
Avast has publicly released a free decryptor for the FunkSec ransomware, a short-lived but technically notable strain that integrated AI-generated tooling and operated primarily between December 2024 and March 2025.
With the ransomware now considered inactive, Avast’s tool will allow victims to recover encrypted files without paying ransoms.
The decryptor was developed by Avast researcher Ladislav Zezula in collaboration with law enforcement, following months of analysis into the ransomware’s structure and operation. FunkSec emerged on December 4, 2024, when the gang began posting victims on a leak site. However, Avast’s research indicates that the group likely began with pure data exfiltration and extortion before later deploying file-encrypting malware. The first known ransomware sample appeared on VirusTotal on December 31, 2024, with the most recent victim traced to mid-March 2025. In total, 113 victims were counted, based on entries from the gang’s leak portal.
FunkSec was notable for its strategic use of AI tools. The gang reportedly leveraged AI to generate phishing email templates and develop helper scripts used in the attack chain. Despite this, only about 20% of the ransomware operation was attributed to AI-generated content. Most of the ransomware code itself was handwritten in Rust, using the orion-rs cryptographic library (v0.17.7) to implement Chacha20 encryption alongside Poly1305 for authentication and data integrity.
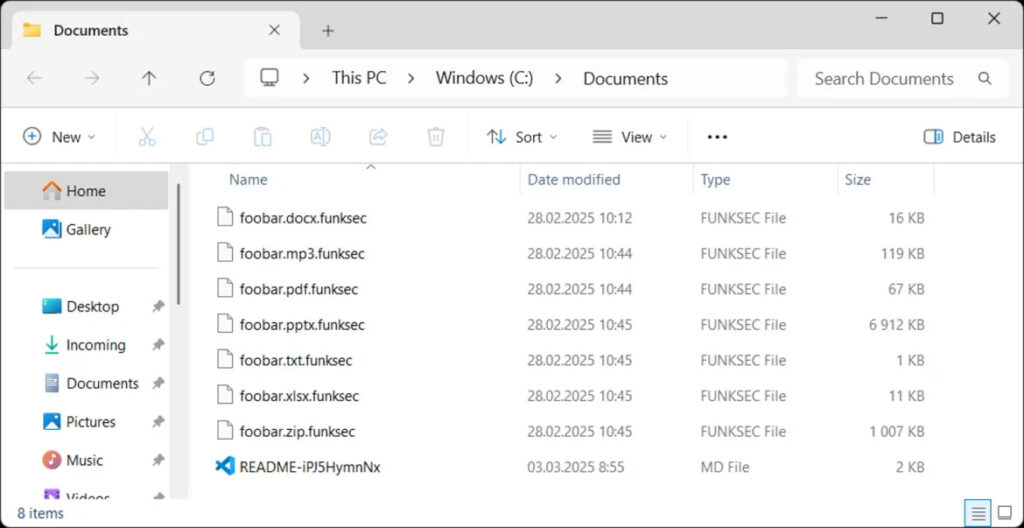
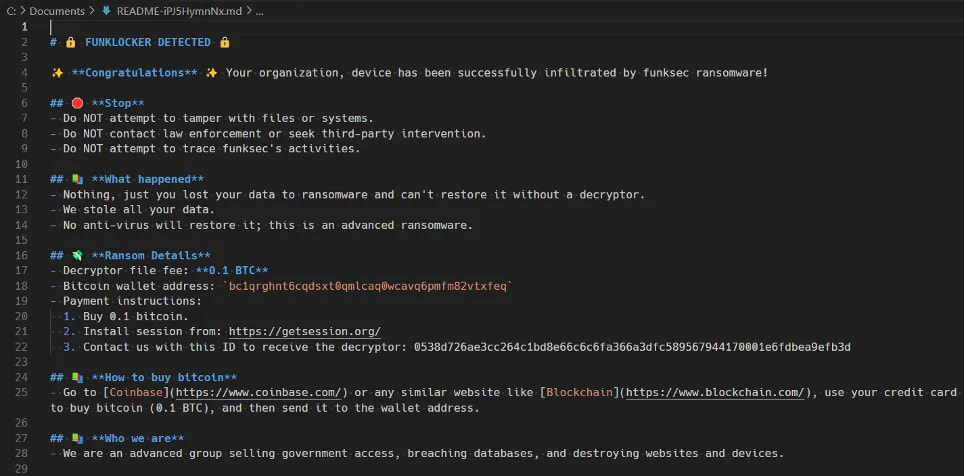
FunkSec encrypted files in 128-byte blocks, each appended with 48 bytes of metadata, resulting in encrypted files being approximately 37% larger than their originals. Affected files bear the “.funksec” extension and are accompanied by a ransom note titled README-{random}.md in each affected folder. During execution, the malware searches all available local drives and excludes a large number of file types from encryption, primarily documents, multimedia, and software-related extensions.
Avast
Before encrypting files, FunkSec terminates several popular applications and services, including browsers, communication tools (like Discord and Skype), media players, developer tools, and system utilities. It also attempts to stop critical Windows services such as WindowsUpdate, WinDefend, and CryptSvc, likely to prevent recovery or interference during execution.
Avast
The ransomware depends in some samples on downloading a themed desktop wallpaper from Imgur, using hardcoded URLs from Imgur, a design quirk that caused many samples to malfunction when the images became unavailable.
FunkSec targeted individuals and organizations opportunistically and never appeared to escalate into widespread campaigns. Its low technical polish, the presence of many faulty samples, and inconsistent execution may have contributed to its relatively limited reach and eventual demise.
Avast
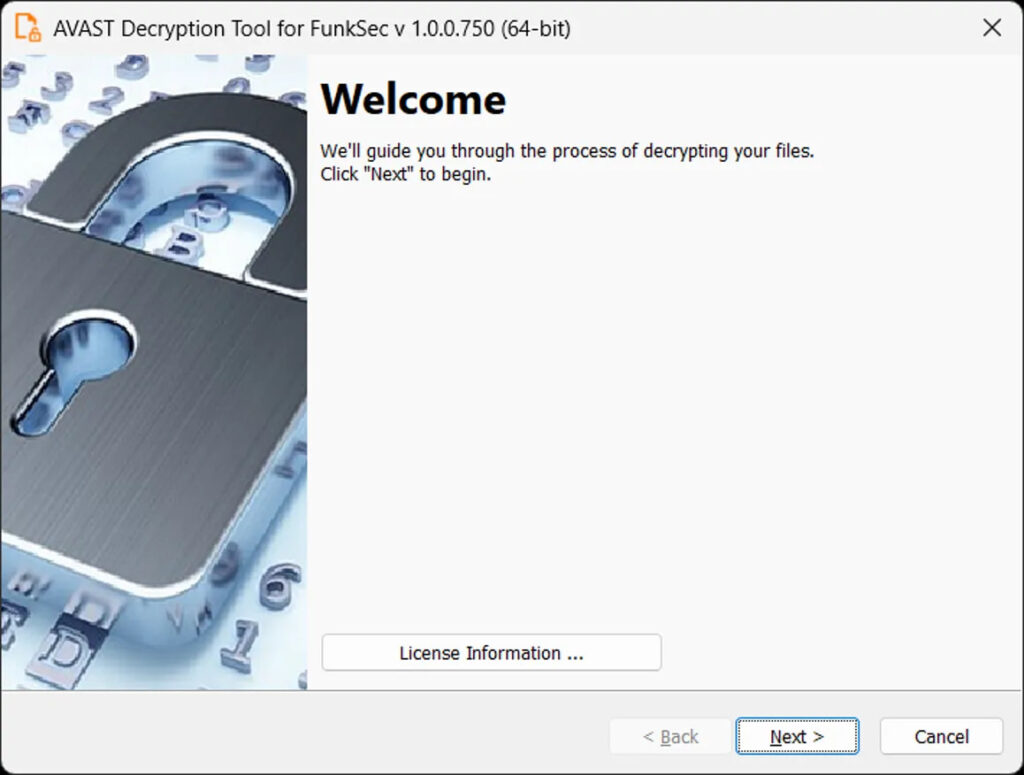
Avast’s decryptor is available in both 64-bit and 32-bit versions, though the ransomware itself only affects 64-bit systems. The tool should be easy to use as it offers a wizard-style interface to guide FunkSec victims through a simple decryption process. The backup option is selected by default to mitigate the risk of data loss during the process, as ending up with corrupted files is not a rare occurrence when attempting decryption.







Leave a Reply