
A newly disclosed trick involving Safari's handling of custom cursors on macOS has reignited concerns over address bar spoofing.
The issue allows attackers to overlay spoofed text, such as “icloud.com,” over the Safari address bar, creating a misleading visual that could aid phishing attempts.
The report was first made public on August 28, 2025, by an independent researcher going by “RenwaX23”, who also shared a proof-of-concept on GitHub and a demonstration video on X. The trick hinges on Safari's failure to enforce strict cursor boundary checks, which some researchers refer to as the “Line of Death,” which browsers like Chrome and Firefox use to prevent page content from visually interfering with trusted UI elements like the address bar.
By crafting an oversized custom cursor image (128×128 pixels), attackers can visually superimpose text or graphics onto parts of Safari's UI. For example, hovering over a “Login to iCloud” button can trigger a cursor image that displays “icloud.com” in the same position as Safari's address bar, even though the user is still on a potentially malicious site.
This issue was tested and confirmed to work on Safari Version 18.4 (build 20621.1.15.11.5) running on macOS 15.4 Beta (24E5238a). However, some users on social media report partial mitigation in Safari 18.6, where cursor overlap appears reduced or blocked depending on interface variations such as the presence of bookmarks or whether Safari is in private browsing mode.
A legacy problem resurfacing?
The cursor-based spoofing method isn't entirely new. A flaw from 2009, tracked as CVE-2009-1710, described a similar issue in older versions of WebKit, where custom cursors combined with manipulated CSS hotspots allowed spoofing of browser UI elements, including the hostname and security indicators. There's speculation that the current behavior in Safari may be a regression of that older bug.
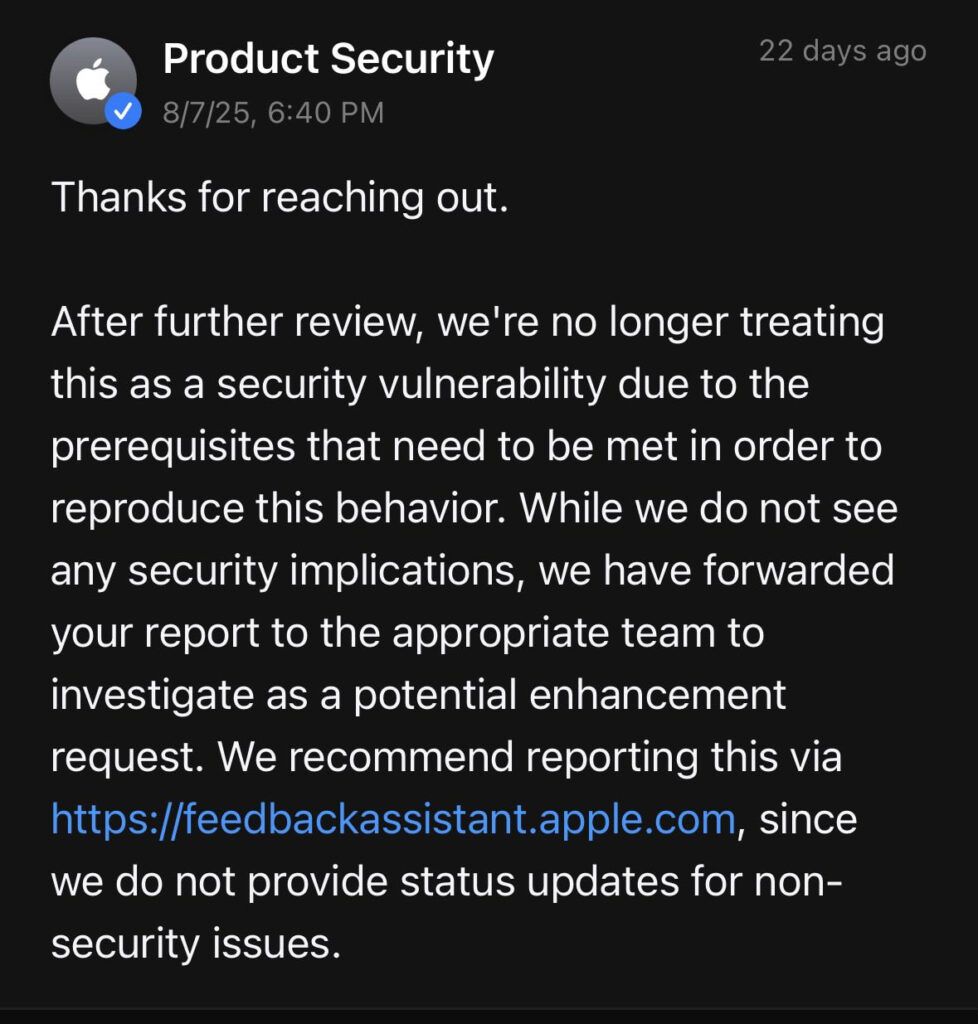
Despite the clear phishing potential, Apple has declined to classify this behavior as a security issue. The report was submitted to Apple on May 5, 2025, acknowledged later that month, and officially closed on August 7 with the statement that it does not meet the company's criteria for a vulnerability. This has prompted frustration in parts of the security community, with some arguing that modern phishing attacks often rely on subtle, visual tricks rather than technical exploits, and that Safari's UI should prevent such visual deception.
RenwaX23
Contested status
The disclosure has split the community. Some argue this is a high-risk UI deception flaw that undermines user trust in the browser's visual security cues. Others believe the issue is too circumstantial to be considered a true vulnerability, especially since Safari does not allow JavaScript-driven manipulation of the address bar itself, and cursor-based spoofing does not affect browser logic or credential autofill mechanisms.
It has also been pointed out that Safari's password manager and autocomplete functions do not trigger on the spoofed elements, offering some safeguard against direct credential theft.
While this isn't a vulnerability in the traditional sense, as there's no code execution or security sandbox escape, it does pose a potential phishing vector that relies on human error and trust in Safari's address bar. Therefore, Safari users should be aware of this potential threat. Attackers could combine this visual spoof with social engineering and off-platform tricks (like fake emails) to convince users to enter credentials on a lookalike site. The best approach would be using password managers that rely on domain matching to auto-fill credentials, which are unaffected by visual tricks like this.






Leave a Reply