
AngelSense, a company specializing in GPS tracking and assistive technology for individuals with special needs, inadvertently exposed a vast amount of sensitive user data due to an unsecured Elasticsearch database.
Researchers at UpGuard discovered the data exposure on January 17, 2025, and after multiple attempts to notify the company, the database was finally secured on January 27. The exposed data included GPS locations, personal details, passwords, and AI-generated insights on the status of monitored individuals.
AngelSense, headquartered in New Jersey, provides GPS tracking devices and an AI-powered monitoring platform designed to enhance the safety of individuals with disabilities. The company’s services are widely used by law enforcement agencies, caregivers, and parents to track vulnerable individuals and respond to potential safety threats. AngelSense’s mobile app has thousands of customers and is marketed as a critical tool for ensuring the well-being of those with special needs.
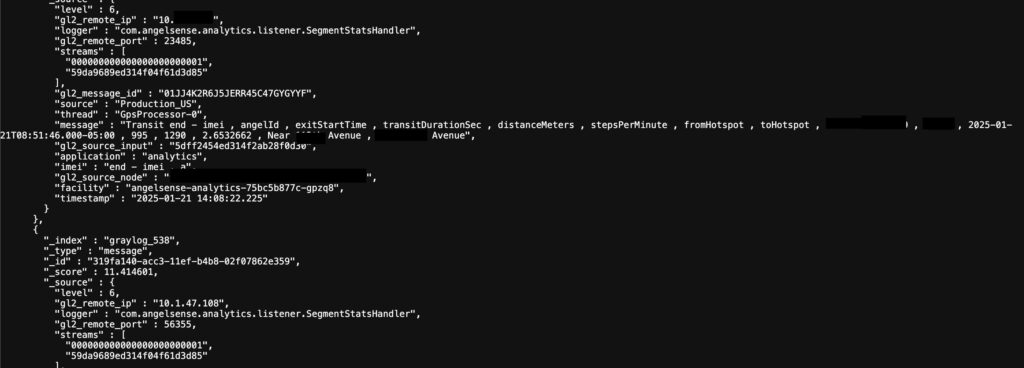
The exposed database, which lacked password protection, contained 30 indexes of log files, each holding approximately 120 million entries. The logs captured system-generated data from AngelSense’s devices and services, exposing over 3 billion data objects totaling 1.8 terabytes in size. UpGuard accessed sample records using Elasticsearch queries, revealing highly sensitive user information.

UpGuard
The leaked information primarily came from logs generated by AngelSense’s “Production_US” system, which stored customer and device-related data, including:
- Personal details: Names, shipping addresses, email addresses, and phone numbers of device purchasers and monitored individuals.
- Payment information: Last four digits of credit cards and expiration dates.
- Account credentials: User email addresses and passwords stored in plaintext.
- GPS data: Real-time locations, movement patterns (speed, heading, and steps per minute), and associated metadata.
- Health-related information: Details on the special needs of tracked individuals, including autism, dementia, and Down syndrome.
- AI decision logs: System-generated insights summarizing user activity based on GPS data.
- Partner organization details: Names of U.S. police departments and care facilities, along with their Wi-Fi SSIDs.
UpGuard
Company response
AngelSense CEO Doron Somer confirmed the security lapse, attributing the delayed response to the company initially mistaking UpGuard’s email report for spam. It was only after receiving a phone call from UpGuard that the company took action to investigate and resolve the issue.
Somer stated that AngelSense had no indication that any unauthorized parties accessed the exposed database beyond UpGuard researchers. However, he did not confirm whether the company has technical monitoring systems in place to detect potential unauthorized access before the breach was discovered. Furthermore, AngelSense has not yet committed to notifying affected customers, stating that it is still evaluating whether notifications are necessary.
This incident highlights the ongoing risks associated with misconfigured cloud databases, a common cause of large-scale data leaks. Just yesterday, we reported about a database misconfiguration by DeepSeek AI exposing user prompts potentially containing sensitive information, API keys, and network infrastructure information.
AngelSense’s security practices came under scrutiny as its Trust and Security page claims that data is encrypted in transit and at rest, but it does not mention compliance with security frameworks like ISO 27001 or SOC2. The presence of plaintext passwords and sensitive personal data in log files further raises concerns about the company’s security protocols.







Leave a Reply