
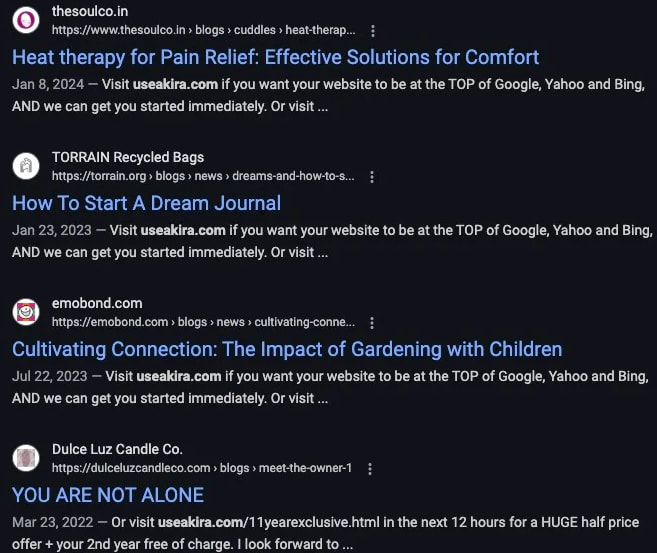
A large-scale spam campaign driven by an AI-enabled botnet dubbed AkiraBot has successfully targeted and spammed over 80,000 websites since last September, exploiting contact forms and live chat widgets to promote questionable SEO services.
Despite bearing the name “AkiraBot,” this operation is not related to the Akira ransomware group. The naming stems from the use of “Akira” in the spammed SEO service domains.
Discovered and analyzed by SentinelLabs, AkiraBot represents a notable evolution in spam frameworks. It combines modular design, evasive network behavior, and CAPTCHA bypass capabilities with OpenAI-powered message generation. Its operators have targeted over 420,000 sites in total, focusing primarily on small to medium-sized businesses using platforms like Shopify, Wix, Squarespace, and GoDaddy.
SentinelLabs
Unlike generic spam tools, AkiraBot employs the GPT-4o-mini model via hardcoded OpenAI API keys to craft individualized outreach messages. These messages are generated by scraping the target website's content using BeautifulSoup and feeding it into pre-defined templates. This results in tailored, human-like spam that can evade traditional spam detection systems due to its variability and contextual relevance.
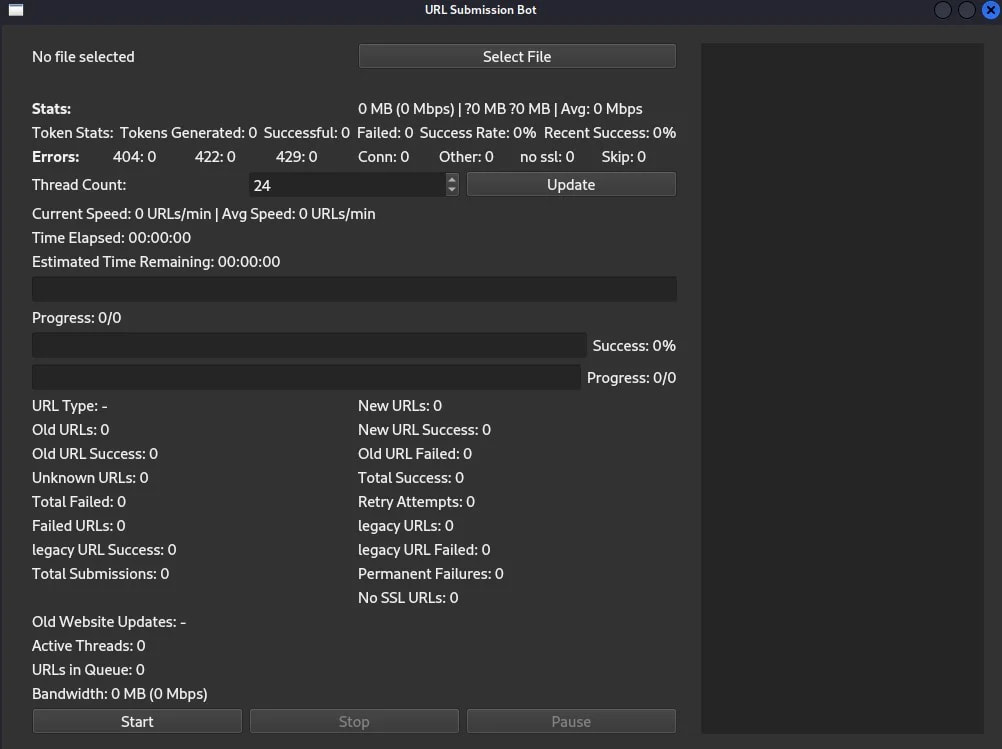
The toolchain shows signs of consistent development, with multiple versions found in archives bearing names like shopbotpyv2, wixbot, GoDaddy, and NextCaptchaBot-v6. Initial versions targeted Shopify sites, but later releases expanded their scope to contact forms and customer support widgets, including Reamaze integrations. A GUI interface allows operators to control threading, targets, and monitor real-time performance.
SentinelLabs
AkiraBot includes robust CAPTCHA bypass capabilities targeting services such as hCAPTCHA and Google reCAPTCHA. To defeat these, the bot employs a combination of browser fingerprint spoofing — manipulating audio context, WebGL, system memory, timezones, and navigator attributes — and automated CAPTCHA-solving services like FastCaptcha, Capsolver, and NextCaptcha. It achieves this through a headless Chrome instance that simulates user behavior using Selenium and custom JavaScript injections.
Network evasion is handled via SmartProxy, a legitimate service whose credentials have appeared in previous cybercriminal leaks. The tool rotates proxies using both data center and residential IPs to avoid detection and geographic restrictions. Logging and telemetry are handled via monitor.py and monitor_random.py scripts, which also report success metrics and CAPTCHA status to a Telegram bot linked to a user with the alias “hts” and handle “Shadow / hts.”
The targeted websites span a broad spectrum of small business operations, particularly those relying on low-code platforms for online presence and customer engagement. These businesses are often more susceptible to such attacks due to limited security resources and reliance on built-in anti-spam features.
In terms of infrastructure, domains linked to AkiraBot and its associated SEO services (marketed as Akira and ServiceWrap) rotate frequently to avoid detection. Early domains like akirateam[.]com, unj[.]digital, and goservicewrap[.]com have connections to infrastructure used in prior malicious campaigns. Reviews for these services on TrustPilot show patterns indicative of fabricated testimonials, with content that also appears AI-generated.
SentinelLabs
The scale, adaptability, and AI integration of AkiraBot marks a shift in spam operations, suggesting an emerging trend where adversaries weaponize LLMs to increase effectiveness and evade legacy defenses like keyword-based spam filtering.







Leave a Reply