
Wondershare RepairIt, a popular AI-driven image and video repair tool, has been found leaking sensitive user data and proprietary company assets due to hardcoded cloud credentials and insecure storage practices.
The discovery was made by Trend Micro researchers who published a detailed analysis revealing multiple serious security lapses in the way Wondershare RepairIt handled user data, cloud credentials, and software components. Initial disclosure was made in April through the Trend Zero Day Initiative (ZDI), but as of publication, Wondershare had not responded to the report. The associated vulnerabilities have been assigned CVE-2025-10643 and CVE-2025-10644.
Hardcoded credentials and exposed databases
The researchers began their investigation by analyzing a binary of Wondershare RepairIt, a desktop application that leverages artificial intelligence to restore corrupted photos and videos. During static analysis of the compiled executable, they found hardcoded access credentials for a cloud storage service embedded directly within the application code. These credentials granted read-write permissions to a cloud bucket containing:
- Thousands of user-uploaded images and videos, some dating back over two years
- AI model files and their configurations
- Signed binaries and application executables
- Container images and internal source code
Worse, the cloud storage lacked basic security measures as the data was unencrypted, access tokens were overly permissive, and identifiers such as bucket names and API endpoints were easily retrievable from the binary. The access token essentially acted as a master key, allowing anyone with technical knowledge to view, modify, or replace sensitive data and software components.
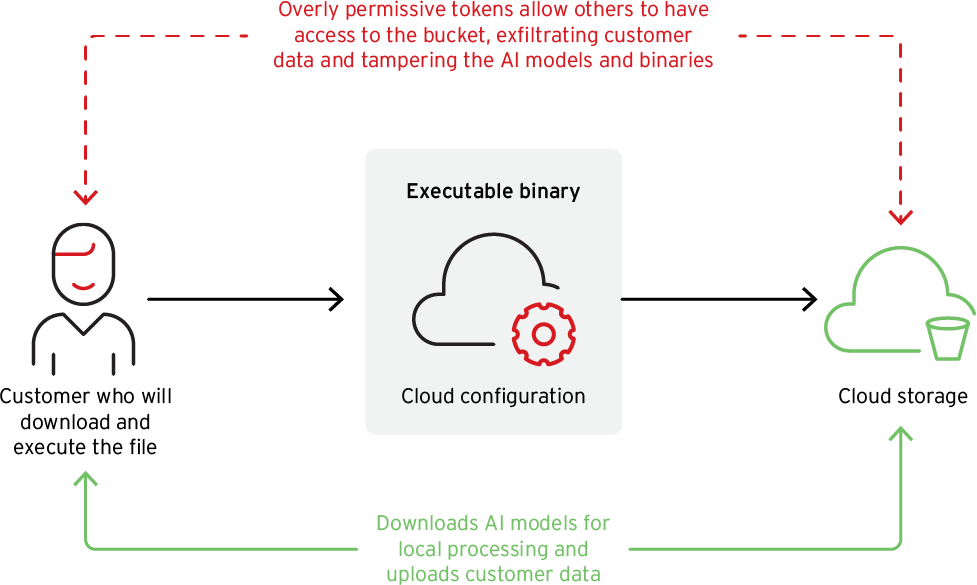
Wondershare RepairIt is developed by Wondershare Technology, a China-based software company known for producing multimedia and utility tools with a strong global customer base. Marketed as a user-friendly AI tool for restoring corrupted digital media, RepairIt uses a cloud-assisted architecture, where local software fetches AI models and processes files via online services.
Despite the company’s stated privacy policy claiming that uploaded user data is not stored, Trend Micro’s findings directly contradict this promise. User images were found stored in the cloud storage buckets accessed by the app, posing severe privacy concerns and potential violations of regulations such as GDPR and HIPAA.
Supply chain attack potential
Beyond data exposure, the hardcoded access to cloud storage presents a far graver risk, which is the manipulation of software components and AI models downloaded by users. RepairIt’s binary instructs the app to fetch AI models from the exposed bucket at runtime. If a malicious actor were to alter these models or replace signed binaries in the storage, the application would unknowingly distribute compromised components to users.
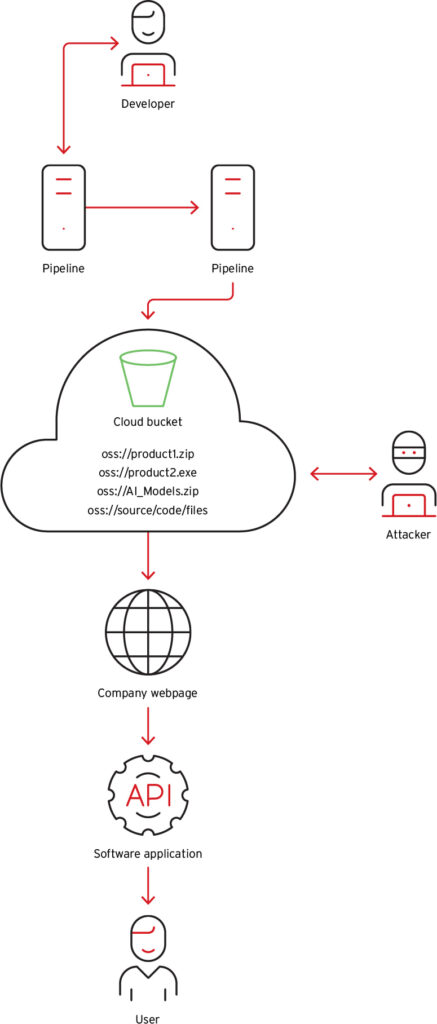
Such a scenario would enable attackers to distribute malware through signed updates, replace AI models with malicious variants executing arbitrary code, embed persistent backdoors into customer systems, or exfiltrate additional data during AI model inference.
Trend Micro disclosed the vulnerabilities in April 2025 and shared a final draft of their research prior to publication. As of September 23, no response has been received from Wondershare, and the vulnerabilities remain publicly exploitable.







Leave a Reply