
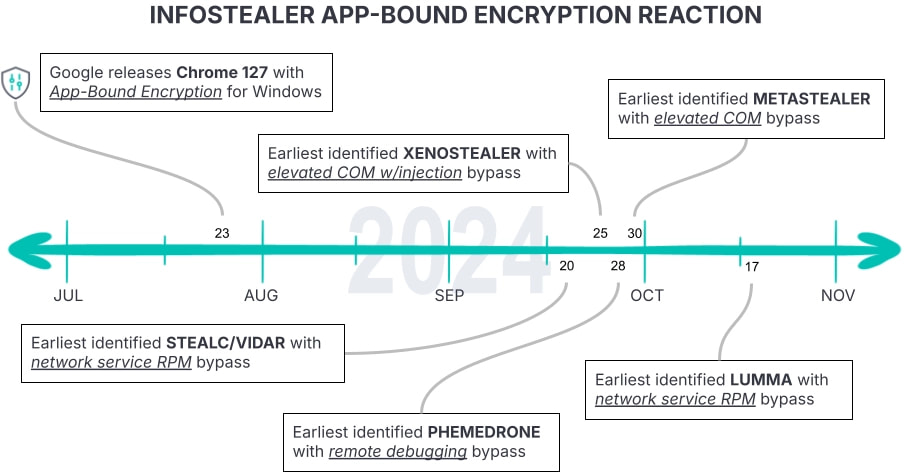
Infostealers targeting Google Chrome users are bypassing the browser's newly implemented Application-Bound Encryption (ABE) to steal cookie data, a feature introduced in Chrome 127 to restrict cookie access to authorized processes only.
Security researchers at Elastic Security Labs outlined the various techniques that malware creators have developed to circumvent this protection, revealing the rapid adaptation of malware strains like Vidar, Lumma, and Stealc.
Chrome's Application-Bound Encryption, launched in July 2024, was intended to shield cookies and other sensitive browser data by encrypting it and limiting decryption access to verified Chrome processes.
However, prominent infostealers have responded by integrating sophisticated bypasses, each leveraging unique methods to access cookies stored in Chrome, including debugging interfaces, in-memory attacks, and COM object exploitation.
Elastic
Here's how some of the most prominent infostealers are defeating Chrome's defenses:
STEALC, a derivative of VIDAR, bypasses ABE by injecting code into Chrome processes and targeting Chrome's CookieMonster component, which is responsible for cookie management. The malware locates the CookieMonster object in Chrome's memory using pattern-matching techniques borrowed from the ChromeKatz tool, an offensive security utility. This allows it to read decrypted cookie data directly from memory. STEALC scans Chrome processes, terminating any that block access, and starts a new process to avoid detection, ultimately extracting cookies through memory traversal and reading Chrome's decrypted data structures.
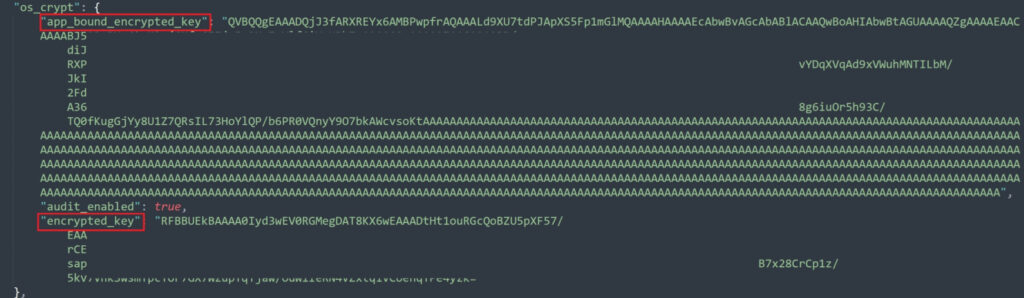
Updated in late September, METASTEALER operates by impersonating the SYSTEM user token to elevate privileges and directly interact with Chrome's encryption service, known as GoogleChromeElevationService. It accesses Chrome's local JSON files where encryption keys are stored, including the app_bound_encrypted_key used in the latest Chrome versions. By invoking the DecryptData method via COM, METASTEALER successfully decrypts cookies for extraction, bypassing the application-bound restrictions without administrative privileges, according to the malware developers.
Elastic
Leveraging Chrome's debugging protocol, PHEMEDRONE initiates a hidden Chrome session in remote debugging mode to access cookies. This method allows it to connect to Chrome's DevTools API and issue a request to retrieve cookies in plaintext. By running Chrome off-screen and using WebSocket connections, PHEMEDRONE can stealthily pull cookie data without directly interacting with Chrome's core encryption mechanisms, circumventing restrictions while avoiding detection.
Hosted on GitHub and actively maintained, XENOSTEALER uses a method similar to METASTEALER by launching a Chrome instance, injecting code, and employing the Chrome elevation service for decryption. The malware accesses the app_bound_encrypted_key and decrypts it within Chrome's own process environment. This approach, which relies on injecting into Chrome's own memory space, allows XENOSTEALER to sidestep the need for elevated privileges by embedding itself within the targeted browser process.
The LUMMA infostealer uses pattern-based memory scanning to locate Chrome's CookieMonster instances in chrome.dll, the module where cookies are managed. By scanning Chrome's memory, it finds and decrypts cookies in real time and then transmits them to its command-and-control (C2) server. LUMMA's creators obfuscate the pattern signatures within the malware code to avoid detection, ensuring that it can reliably extract cookies from Chrome even as security updates are rolled out.
User action required
As infostealers continue to evolve in response to Chrome's new security measures, organizations and users can take several proactive steps to mitigate the impact:
- Monitor for instances of Chrome being spawned by unverified parent processes or accessing cookie files as these can be signs of infostealer activity.
- Enable multi-factor authentication (MFA) to add a second layer of protection that prevents unauthorized access even if cookies are compromised.
- Limit administrative access to reduce the effectiveness of malware that relies on privilege escalation.
- Regularly clear cookies to minimize the amount of data available for potential theft.
- Implement endpoint monitoring to identify suspicious process injections or unauthorized COM object usage to be able to detect these advanced malware techniques.
Google's Application-Bound Encryption was intended to make attacks against cookies more observable and detectable, yet infostealers are aggressively adapting. By understanding their methods, users can better equip themselves to detect and prevent these increasingly sophisticated cookie-stealing techniques.






Leave a Reply