
Security researcher Kevin Beaumont has revealed the active exploitation of an undisclosed vulnerability in FortiManager, a Fortinet product used to manage large deployments of FortiGate firewalls.
The flaw, referred to as “FortiJump,” has not been publicly documented with a CVE (Common Vulnerabilities and Exposures) number, despite ongoing exploitation by state-sponsored actors for espionage purposes.
The vulnerability resides in the FortiGate to FortiManager Protocol (FGFM) and has been used to target Managed Service Providers (MSPs) in sophisticated attacks. Beaumont's discovery first surfaced on October 13, 2023, when he alerted the cybersecurity community via Mastodon after noticing malicious activity on his FortiManager honeypot.
His findings suggest that attackers can exploit the FGFM protocol to register rogue FortiGate firewalls with the FortiManager. Once connected, these attackers can gain remote code execution capabilities on the FortiManager, allowing them to control legitimate downstream firewalls, extract credentials, and modify configurations—potentially compromising multiple networks managed by MSPs.
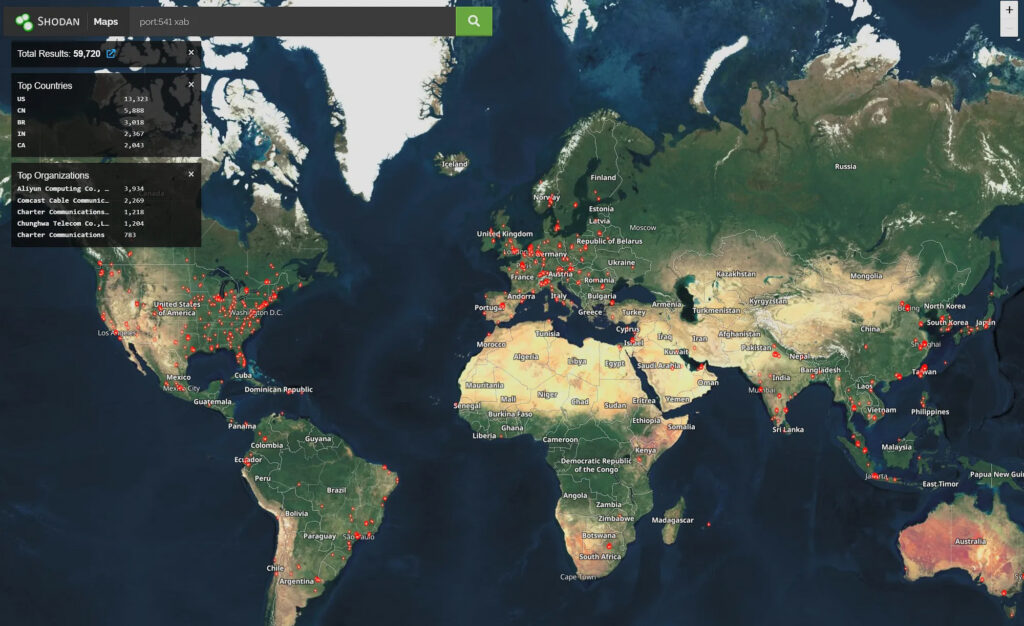
What makes the vulnerability particularly concerning is its wide exposure. Beaumont's investigation revealed that around 60,000 FGFM devices are internet-facing, making them easy targets for exploitation.
doublepulsar
The flaw is compounded by the fact that FortiManager, by default, allows any device with a valid certificate to register automatically, even if the device's serial number is unknown. Attackers can reuse certificates from FortiGate devices to bypass this requirement, making it relatively simple to gain unauthorized access.
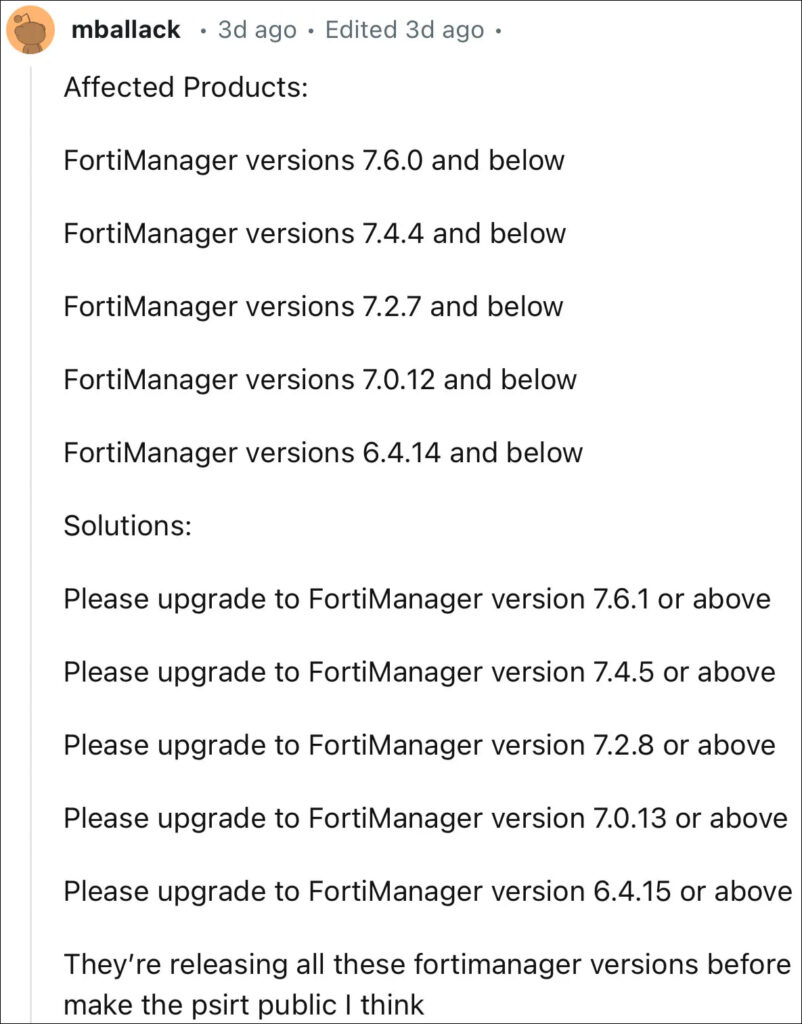
Despite the significant security implications, Fortinet has not yet assigned a CVE to the vulnerability or made a public disclosure. Patches have been made available for some FortiManager versions, but as of writing this, some versions, such as 7.6.0 and 6.4.14, remain without fixes.
doublepulsar
Notably, Beaumont has criticized Fortinet's lack of transparency, highlighting inconsistencies between their public commitment to “radical transparency” and the handling of this issue. According to the researcher's account, many infosec professionals were unaware of the vulnerability, relying on his Mastodon posts for updates rather than any formal Fortinet announcement.
Fortinet
FortiManager is a centralized network management platform that enables administrators to manage multiple FortiGate firewalls. Its primary users include MSPs, who deploy it to handle firewalls across various client environments. A vulnerability like FortiJump could have far-reaching consequences, as attackers can compromise a single FortiManager instance and then propagate their access across all the managed devices.
Beaumont's findings point to a specific pattern of exploitation involving IP addresses from Vultr, a VPS provider. These IPs were used to connect to his honeypot, demonstrating that state-sponsored actors are actively leveraging the vulnerability. Beaumont has shared a VirusTotal Graph highlighting the malicious IP addresses used in the attacks, which originated from the U.S., South Korea, and Japan.
Security recommendations:
- If running an exposed FortiManager instance, update to patched versions, including 7.4.5, 7.2.8, or higher.
- Disable the FortiGate to FortiManager protocol unless absolutely necessary. However, this option does not work on some versions, including 7.6.0 and 6.4.14.
- Administrators should monitor FGFM traffic (port 541 for IPv4 and 542 for IPv6) for unusual activity and check for any signs of rogue device registration.
- Cross-check network traffic against known malicious IPs provided by Beaumont, particularly those identified in Vultr's range.
Fortinet has been slow to disclose the vulnerability publicly and share details with the security community, and hence administrators using FortiManager may not have realized the urgency of the situation but should act urgently to protect their systems from exploitation.
Article update – Fortinet eventually released the details in a security advisory published after the publication of this post.
A spokesperson for the cybersecurity firm sent CyberInsider the below comment.
“After identifying this vulnerability (CVE-2024-47575), Fortinet promptly communicated critical information and resources to customers. This is in line with our processes and best practices for responsible disclosure to enable customers to strengthen their security posture prior to an advisory being publicly released to a broader audience, including threat actors.
We also have published a corresponding public advisory (FG-IR-24-423) reiterating mitigation guidance, including a workaround and patch updates. We urge customers to follow the guidance provided to implement the workarounds and fixes and to continue tracking our advisory page for updates. We continue to coordinate with the appropriate international government agencies and industry threat organizations as part of our ongoing response.” – Fortinet







Leave a Reply