
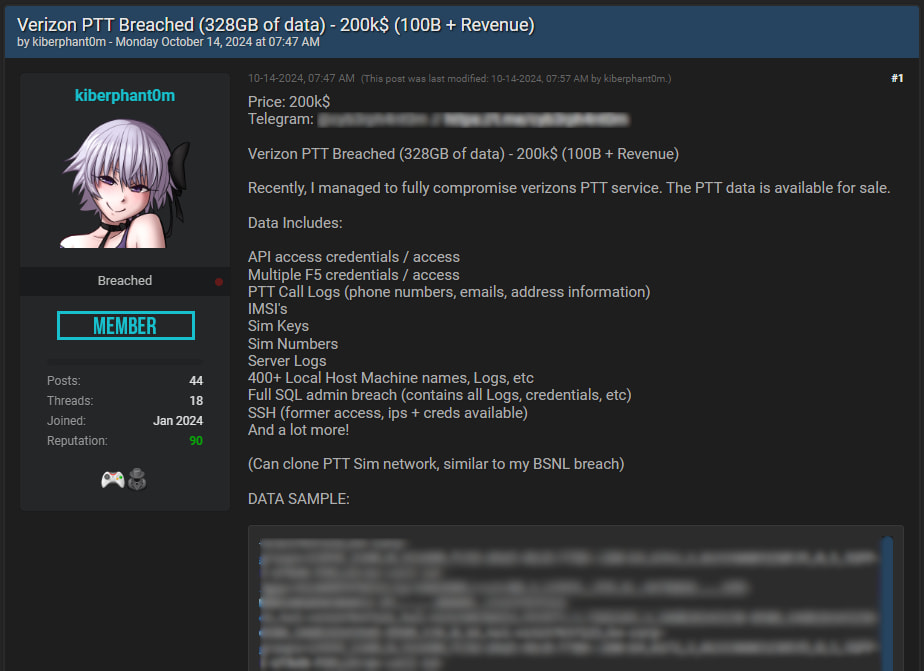
A hacker going by the alias “kiberphant0m” has claimed responsibility for breaching Verizon's Push-to-Talk (PTT) service, leaking 328GB of sensitive data.
The threat actor is offering this trove for sale on the notorious BreachForums platform for $200,000, according to a post published earlier this week. The breach allegedly includes critical information such as API access credentials, F5 system credentials, call logs containing personally identifiable information (PII), server logs, and more.
The breach includes API access, IMSI (International Mobile Subscriber Identity) numbers, SIM keys, and sensitive call logs. Additionally, the hacker claims to have access to over 400 host machine logs, SQL admin credentials, and SSH access to internal systems. The post also indicates that cloning Verizon's PTT SIM network could be possible, as was previously done in a similar breach involving BSNL (Bharat Sanchar Nigam Limited), a major Indian telecom company.
Proof of breach
As part of the threat actor's announcement, a “proof of breach” was included in the form of several screenshots showing network traffic logs and call information related to Verizon's internal systems. These logs appear to reveal real-time communication metadata and network infrastructure details, such as device IP addresses, MAC addresses, and call setup times. These network traces, captured from internal systems, display traffic related to PTT services, which suggests that kiberphant0m gained access to Verizon's PTT infrastructure.
The displayed logs appear to show:
- IP addresses and MAC addresses for devices on Verizon's internal network.
- Real-time communication traces, including timestamps, protocol information, and SIP (Session Initiation Protocol) messages, which are critical to handling VoIP (Voice over IP) calls.
- Call log details, such as phone numbers, IMSI numbers, and other identifying information linked to active Verizon PTT sessions.
This form of evidence is typical in such breaches, as it proves access to sensitive, operational data that would normally be securely stored within the company's systems.
Verizon data for sale
According to the post, the data for sale includes:
- API access credentials: Enabling potential manipulation of Verizon's PTT services.
- F5 credentials: Critical for accessing load balancers, potentially allowing network manipulation.
- PTT call logs: Includes phone numbers, emails, addresses, and other customer metadata.
- IMSI numbers: Key for identifying mobile subscribers on cellular networks.
- SIM keys and SIM numbers: Sensitive data used to authenticate devices on a mobile network.
- Server logs: Detailing internal Verizon operations, likely including network activity and security measures.
- SQL database credentials: Full access to Verizon's SQL databases, which could include all logs, stored data, and further credentials.
- SSH access: Shell access to internal systems, allowing for remote manipulation.
Potential impact
Verizon, with its $100 billion+ annual revenue, serves millions of customers globally, making the alleged breach a serious threat. If validated, the leak could compromise a significant number of users, exposing personal information and network operation details.
Verizon's PTT service, which allows near-instantaneous communication often used by enterprises, government agencies, and large-scale organizations, is highly sensitive. The leaked data could, in the wrong hands, enable malicious actors to spy on communications, clone SIM cards, and launch more sophisticated attacks against Verizon's infrastructure.
At the time of this writing, Verizon has not responded to our inquiries regarding the breach, and hence, the validity of the threat actor's claims has not yet been confirmed.
Earlier this month, we reported about Chinese state-sponsored hackers infiltrating several U.S. telcos, including Verizon, to collect data from the firms' legitimate wiretapping system, used at the request of law enforcement agencies. The latest data breach claims are not related to that campaign.
Update – Verizon has sent CyberInsider the following statement regarding the incident:
This is a security issue involving a widely used third-party technology service provider that does not have access to T-Mobile customer information. T-Mobile systems were not compromised, and no T-Mobile customer data was impacted.
Although the above statement confirms a data breach at a third party provider, it refutes the threat actor's allegations regarding the direct access of Verizon systems and also the leak of customer personal data, including names, email addresses, addresses, and phone numbers.







Leave a Reply