
A new Android malware dubbed Albiriox has surfaced as a potent and rapidly evolving Malware-as-a-Service (MaaS) threat, enabling remote control of infected devices for financial fraud.
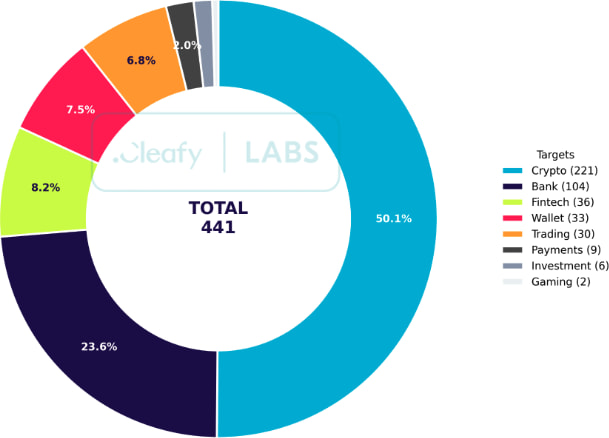
Discovered by Cleafy's Threat Intelligence team, Albiriox has already demonstrated extensive on-device fraud (ODF) capabilities, with over 400 hardcoded targets in the global financial and cryptocurrency sectors.
Cleafy
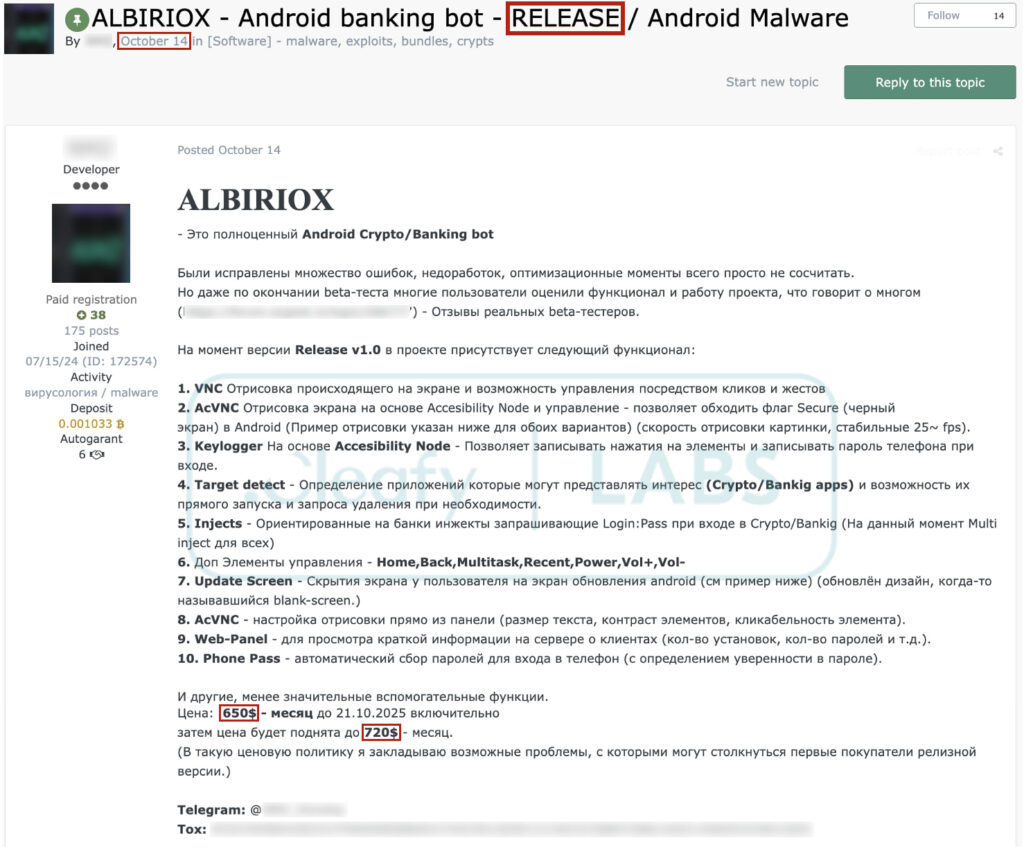
Cleafy researchers began monitoring Albiriox in September 2025, when it was first introduced in private Telegram chats and later promoted on Russian-speaking cybercrime forums. Initially offered to a closed group of high-reputation threat actors, it entered public MaaS distribution in October 2025, with subscription pricing starting at $650 per month, rising to $720 post-launch. Its development and distribution infrastructure, along with linguistic clues, strongly suggest the operation is run by Russian-speaking cybercriminals.
Cleafy
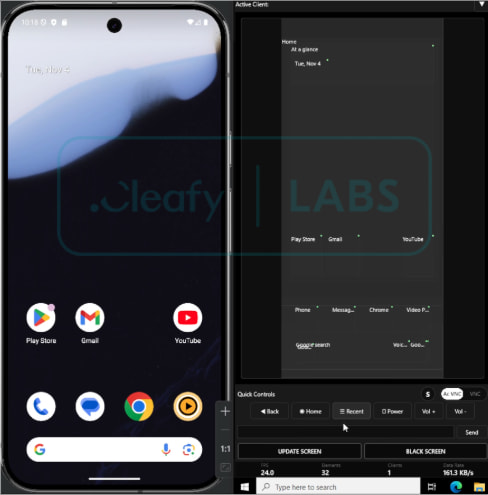
Albiriox is engineered to achieve full device takeover using a VNC-based Remote Access Tool (RAT) and a classic overlay attack mechanism. These dual functionalities enable attackers to both interact in real-time with the infected device and harvest credentials by spoofing legitimate app interfaces.
Unlike traditional banking trojans that merely harvest data, Albiriox facilitates real-time fraud by allowing attackers to perform transactions from within the victim's legitimate session. This is achieved via a custom-built Accessibility VNC (AcVNC) module that leverages Android Accessibility Services, granting attackers visibility into otherwise protected applications, particularly those using Android's FLAG_SECURE protection to block screen captures.
Cleafy
Albiriox's codebase includes a hardcoded list of target applications, grouped under a class called AppInfos. The list encompasses a broad spectrum of apps, including traditional banks, fintech startups, crypto wallets, and payment platforms, underscoring the malware's global ambitions. The infected devices become part of a botnet that communicates via unencrypted TCP sockets, sending device information such as hardware ID and OS version during the initial handshake.
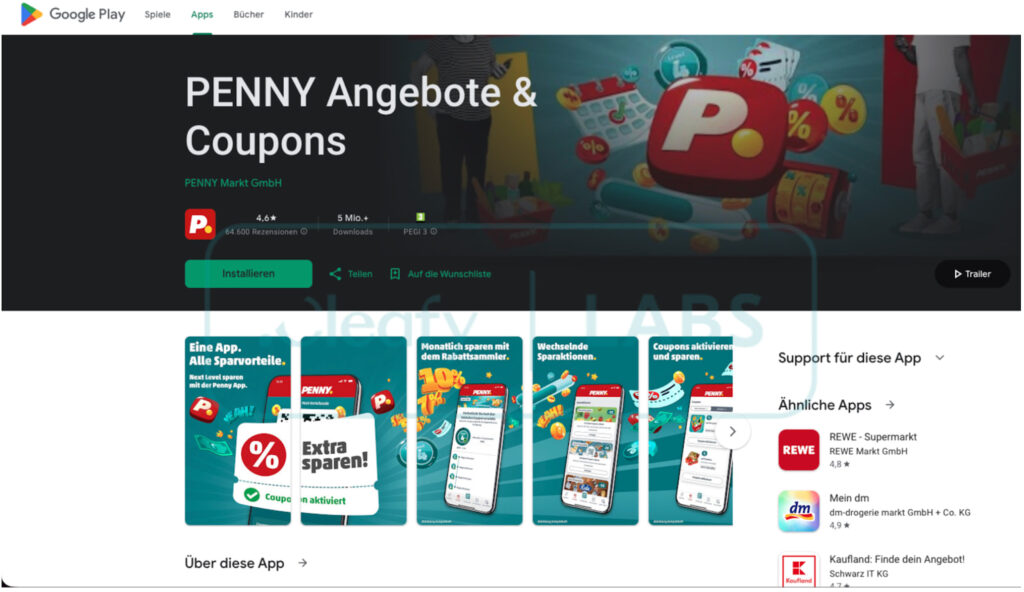
The malware is distributed through social engineering. One observed campaign targeted Austrian users through SMS phishing and fake Google Play pages impersonating popular retail chains. These lures led to the download of malicious APKs acting as droppers. The dropper apps employed the JSONPacker obfuscation technique and manipulated users into granting installation permissions under the guise of a system update.
Cleafy
A later version of the phishing campaign introduced a WhatsApp-based delivery system, requiring victims to input Austrian phone numbers before receiving a download link, data that was sent directly to a Telegram bot controlled by the threat actors.
Albiriox developers bundle a custom APK builder integrated with Golden Crypt, a third-party crypting service widely used to evade mobile antivirus detection. This service allows affiliates to generate fully undetectable malware payloads (FUD), enabling smoother deployment and longer dwell time on victim devices.
During analysis, Cleafy uncovered a full set of remote commands enabling UI navigation (e.g., click, swipe, home), data exfiltration (get_phone_password), concealment (black_blank_screen), and application control (launch_app, uninstall_app).
To protect from Albiriox infections, avoid installing apps from unofficial sources or links received via SMS, disable the “Install Unknown Apps” permission, and regularly perform Play Protect scans.






Leave a Reply