Security intelligence firm GreyNoise has launched a free web-based tool that lets users instantly determine whether their home or business IP address has been used for malicious internet scanning.
As residential networks increasingly become unwilling participants in cybercrime infrastructure, the tool offers a rare and practical way for everyday users to check whether their IP address is being used as someone else’s weapon.
The tool, dubbed GreyNoise IP Check, was introduced by GreyNoise Labs and is the latest effort by the company to democratize access to threat intelligence data.
GreyNoise is a US-based cybersecurity company specializing in collecting and analyzing what it calls “internet background noise.” It operates a global sensor network designed to capture scanning and probing activity across the public internet. By cataloging the behavior of IP addresses seen interacting with their sensors, GreyNoise is able to differentiate between benign services, compromised endpoints, and active reconnaissance campaigns.
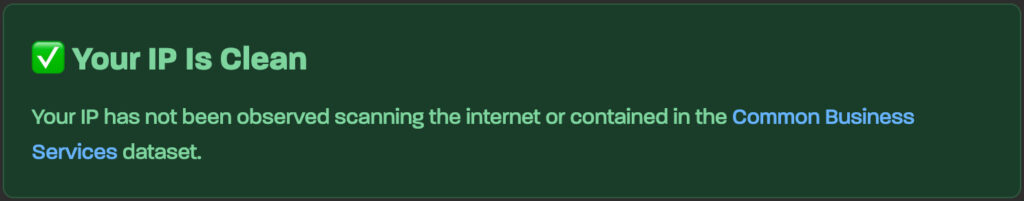
The IP Check tool analyzes the IP address of the device used to visit the site. Within seconds, users receive a verdict classifying their IP as either:
- Clean – No observed malicious or scanning behavior, typical of most residential connections.
- Suspicious/Malicious – Scanning behavior detected, such as probing for open ports, vulnerable services, or brute-force attack patterns.
- Known Business Service – The IP is part of a recognized infrastructure (e.g., VPN, cloud service, or corporate network) and not necessarily malicious.
GreyNoise
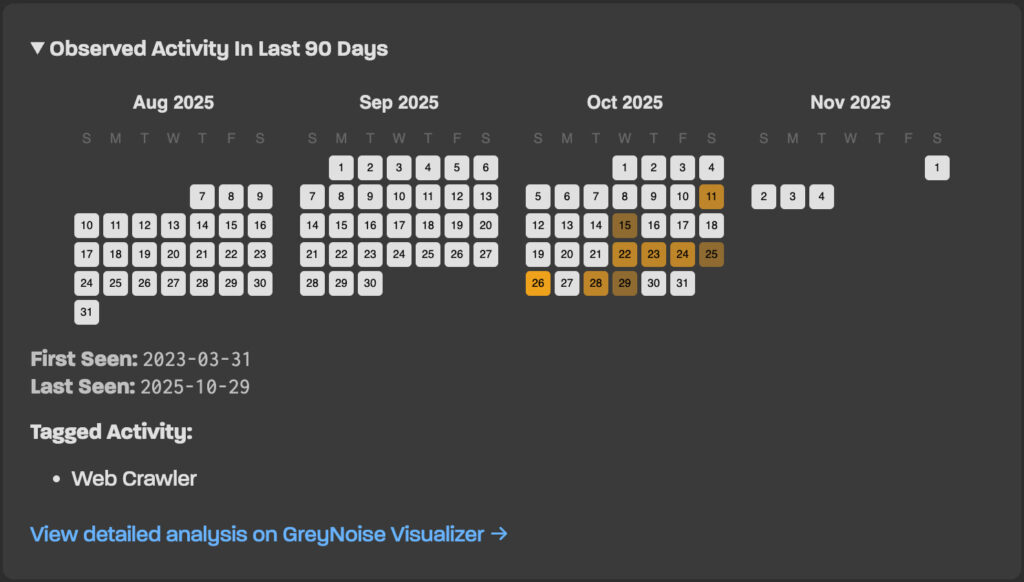
Users whose IPs fall into the latter two categories are shown a timeline of the detected activity over the last 90 days, including tags identifying the type of behavior (e.g., SSH probing, database hunting, web vulnerability scans). This can indicate the presence of malware on a local device, a compromised router, or an exploited IoT gadget.
GreyNoise
GreyNoise emphasizes that many residential users are unaware when their network is compromised. The devices continue to function normally, streaming, browsing, and emailing work just fine, while in the background, they may be participating in global cyberattack campaigns. This passive misuse can build a bad reputation for the IP address, potentially leading to emails being flagged, services being blocked, or logins triggering security alerts.
For technically inclined users, the company offers a no-authentication, JSON-returning API that can be queried using standard tools like curl. This makes it easy to embed IP reputation checks into custom workflows, such as remote device management, VPN login scripts, or automated Wi-Fi trust assessments. The API is open for reasonable use and designed for accessibility rather than monetization.
The tool essentially offers a lightweight, non-intrusive way to quickly assess whether one's home network might be part of a botnet or proxy service without needing to dig through device settings or run antivirus scans. It is recommended that users check their IP address periodically, update their router firmware, change default admin credentials, and use a reputable DNS filtering service.





It shows the wrong IP for my VPN.
Not impressed.