
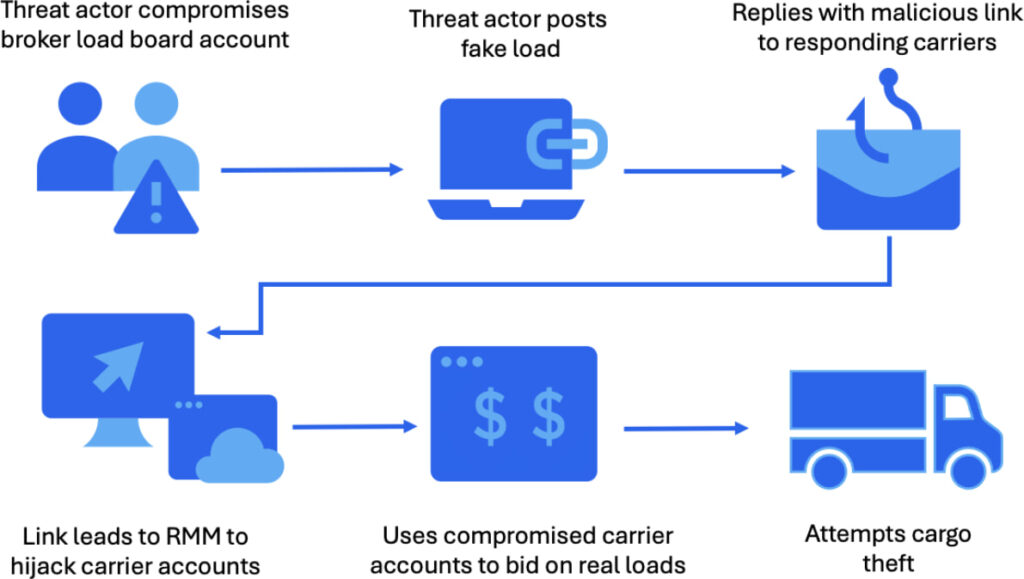
Cyber-enabled cargo theft targets North American trucking and logistics firms, where attackers use remote access software to infiltrate freight networks and orchestrate the theft of physical goods.
The campaign, uncovered by the Proofpoint Threat Research Team, links cybercriminal operations with organized crime groups. These actors exploit compromised accounts within logistics networks to fraudulently bid on legitimate cargo shipments and reroute them for theft, often reselling the goods domestically or overseas.
From digital intrusion to physical theft
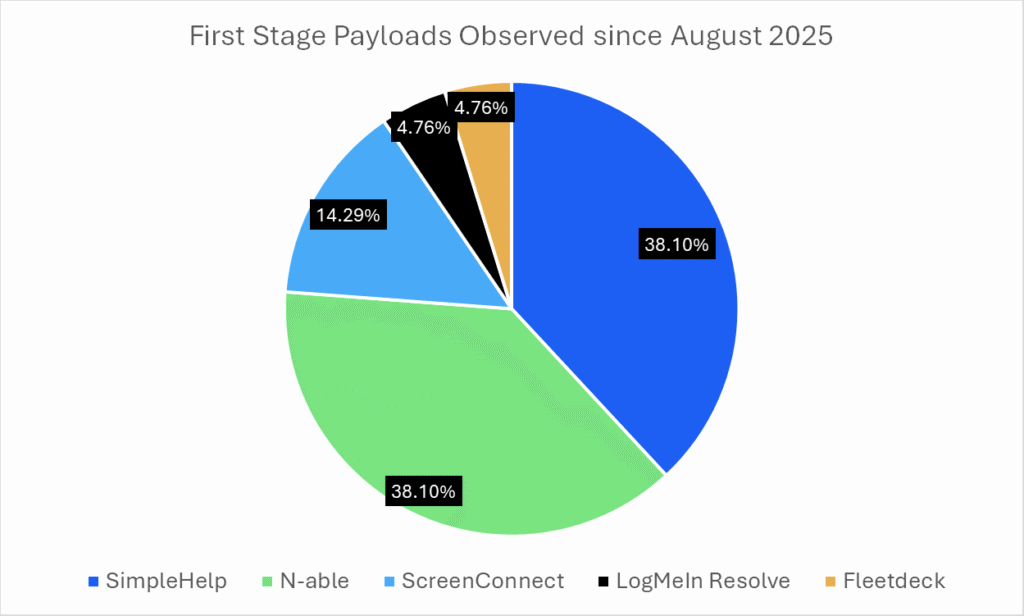
Proofpoint began tracking this threat cluster in June 2025; however, forensic evidence suggests the activity likely started as early as January. The attackers primarily use a suite of legitimate remote monitoring and management (RMM) tools, including ScreenConnect, SimpleHelp, PDQ Connect, Fleetdeck, N-able, and LogMeIn Resolve, as first-stage payloads to gain covert remote access. In many cases, these tools are installed through deceptive links distributed via phishing emails or inserted into ongoing conversations using hijacked email threads.
Proofpoint
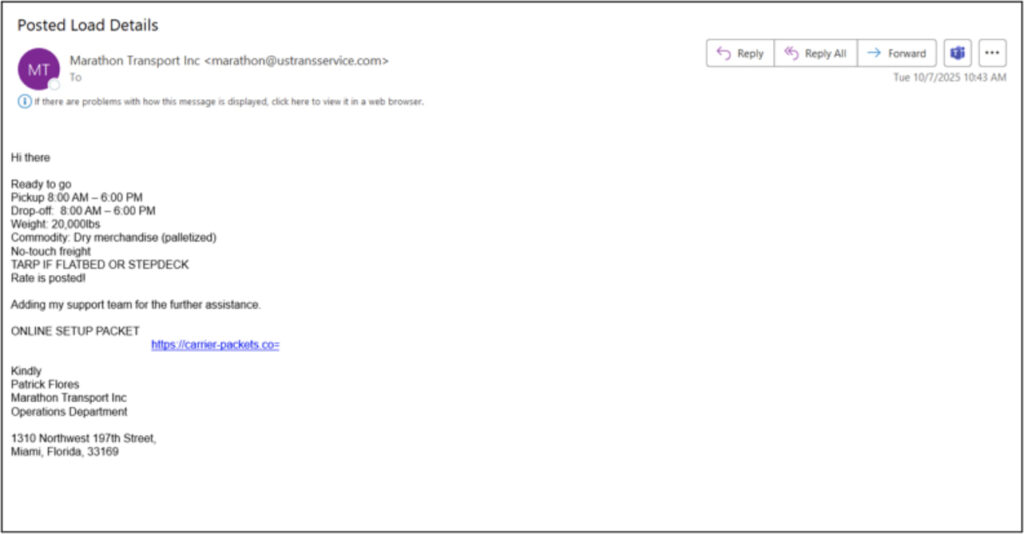
Once initial access is established, threat actors perform reconnaissance and deploy tools like WebBrowserPassView to harvest credentials. The intrusion often begins with the compromise of load board accounts, widely used platforms that connect freight brokers and carriers. From there, attackers can post fraudulent listings, lure real trucking companies, and then impersonate them to hijack actual shipments.
Proofpoint
While the attackers’ identities remain unconfirmed, their operational familiarity with logistics industry workflows, including freight booking processes and dispatch systems, strongly suggests insider knowledge or access to previously compromised entities.
A high-stakes industry under siege
The logistics sector, particularly in the US, has become a prime target for cyber-enabled fraud due to its rapid digitization and often fragmented security practices. Load boards, brokerage systems, and dispatch tools offer efficient interfaces, but they also create new attack surfaces. Even small or family-run trucking firms are not spared, as attackers appear indiscriminate and opportunistic, often targeting anyone who engages with a fake load posting.
Organizations affected include freight brokers, asset-based carriers, and integrated logistics providers. Once a threat actor successfully infiltrates a target, they may delete existing load bookings, block dispatcher alerts, and even reroute calls to attacker-controlled devices, effectively seizing control of the victim’s logistics operations.
Proofpoint
According to the National Insurance Crime Bureau, cargo theft increased by 27% in 2024 and is projected to rise by 22% in 2025. Food and beverages remain the most frequently stolen commodities, though electronics, medical equipment, and even energy drinks have also been documented as targets.
This new campaign builds on techniques observed in earlier threat activity in 2024 and early 2025, including operations that distributed DanaBot, NetSupport, Lumma Stealer, and StealC malware. However, the growing reliance on legitimate RMM tools marks a strategic shift where attackers favor stealth and persistence over traditional malware.






Leave a Reply