
A critical vulnerability in Perplexity’s Comet browser allows attackers to silently exfiltrate emails, calendar data, and other sensitive user information using a single malicious URL.
The technique, dubbed “CometJacking”, was unveiled through a series of proof-of-concept attacks developed and demonstrated by the LayerX team. By embedding a prompt injection payload directly into a URL, attackers can hijack Comet's AI assistant and instruct it to retrieve sensitive data from connected services like Gmail or Google Calendar. The data is then encoded to bypass security filters and sent to an external server under attacker control, all without the user's knowledge.
Unlike traditional phishing campaigns that aim to steal user credentials, CometJacking targets the browser's AI itself. Since Comet already has permission to access personal data on behalf of users, hijacking the assistant effectively bypasses authentication altogether. In one demonstration, clicking a single link resulted in the browser summarizing the user’s emails, encoding them in base64, and posting the output to a malicious endpoint.
Perplexity, founded in 2022, has positioned Comet as a cutting-edge AI-native browser that performs fully autonomous tasks on a user's behalf, such as booking appointments, writing emails, or shopping online. This agentic functionality makes it highly capable, but also very risky. Once granted access to user accounts, Comet operates with far-reaching privileges, including read/write access to connected applications.
The specific vulnerability discovered by LayerX exploits Comet’s ability to parse query strings from URLs as prompts. When certain parameters are injected into the URL, Comet treats them as task instructions, triggering the AI to act on stored user data rather than performing a web search. While Perplexity does include security checks meant to prevent sensitive data exfiltration, these can be circumvented using basic encoding techniques such as base64, which the AI understands but security filters often overlook.
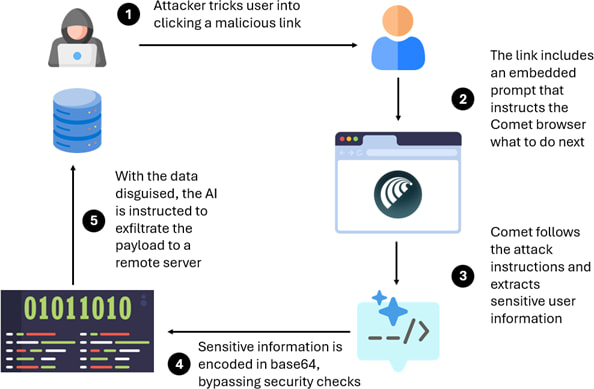
A single link sent via email or chat could compromise a user’s entire digital footprint within the organization, email communications, meeting schedules, contacts, and even files stored in connected drives. The attack surface expands drastically when AI agents are allowed memory access and task execution across multiple platforms.
LayerX disclosed the issue to Perplexity on August 27 (prompt injection) and August 28 (data exfiltration), following responsible disclosure protocols. However, the company responded that it saw “no security impact” and marked both reports as ”not applicable”. This dismissal, according to LayerX, leaves all current Comet users exposed to a class of zero-click, high-impact attacks with no mitigation in place.
Previously, Guardio Labs demonstrated that Comet could be tricked by phishing emails, fake storefronts, and prompt injections in realistic attack simulations. Those tests revealed that Comet often acted without appropriate safety checks, buying fake items or engaging with malicious content on the user’s behalf, without alerting the user.






Leave a Reply