
Despite a crippling global crackdown earlier this year, the LockBit ransomware group has returned with a new cross-platform variant, LockBit 5.0, exhibiting more advanced evasion and encryption capabilities than previous versions.
Trend Micro’s latest analysis reveals a concerted effort by the group to regain technical relevance, even as it continues to lose standing in the criminal underground.
Trend Micro researchers began analyzing new binaries found in early September 2025, shortly after LockBit marked its sixth anniversary with a public declaration of its latest iteration.
Trend’s analysis confirms that LockBit 5.0 includes fully functional variants for Windows, Linux, and VMware ESXi, underscoring the group’s persistent strategy of targeting entire enterprise ecosystems, including virtualized environments. This cross-platform capability, first seen in LockBit 2.0, remains central to the group’s approach.
Each variant shares core behaviors:
- Randomized 16-character file extensions post-encryption,
- Russian language system avoidance via locale and geolocation checks,
- Event log wiping, and
- Absence of traditional infection markers, making detection and forensic recovery more difficult.
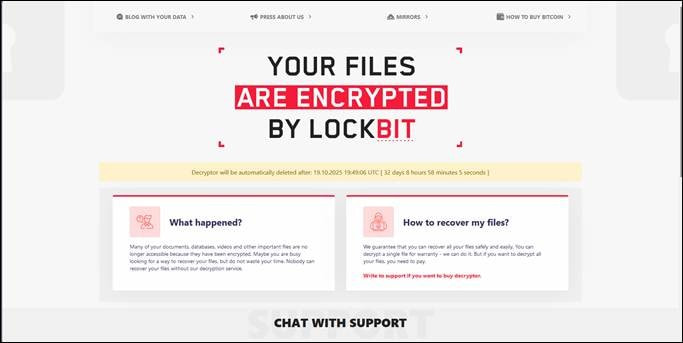
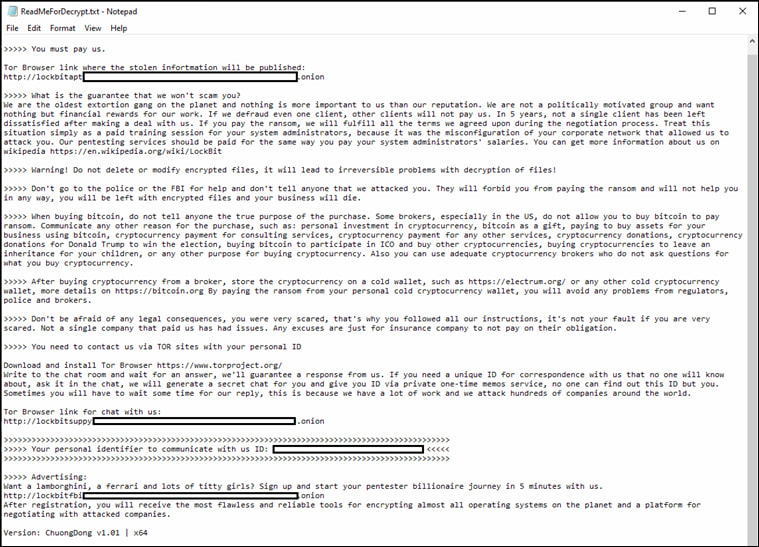
While no major victim disclosures have yet been made under this new version, the group has quietly updated its leak site infrastructure, which retains the “Chat with Support” interface used for ransom negotiations. Trend Micro notes that the overall architecture mirrors LockBit’s previous iterations, suggesting a return to form rather than innovation.
Trend Micro
Deep dive: Windows variant
The Windows payload, heavily obfuscated and packed, employs DLL reflection to execute its payload in memory, evading traditional detection tools. It also disables system logging by patching the EtwEventWrite API with a 0xC3 return instruction, effectively neutralizing Event Tracing for Windows (ETW).
Security services are terminated using hashed service names compared against a hardcoded list of 63 entries. Post-encryption, all system logs are cleared using the EvtClearLog API.
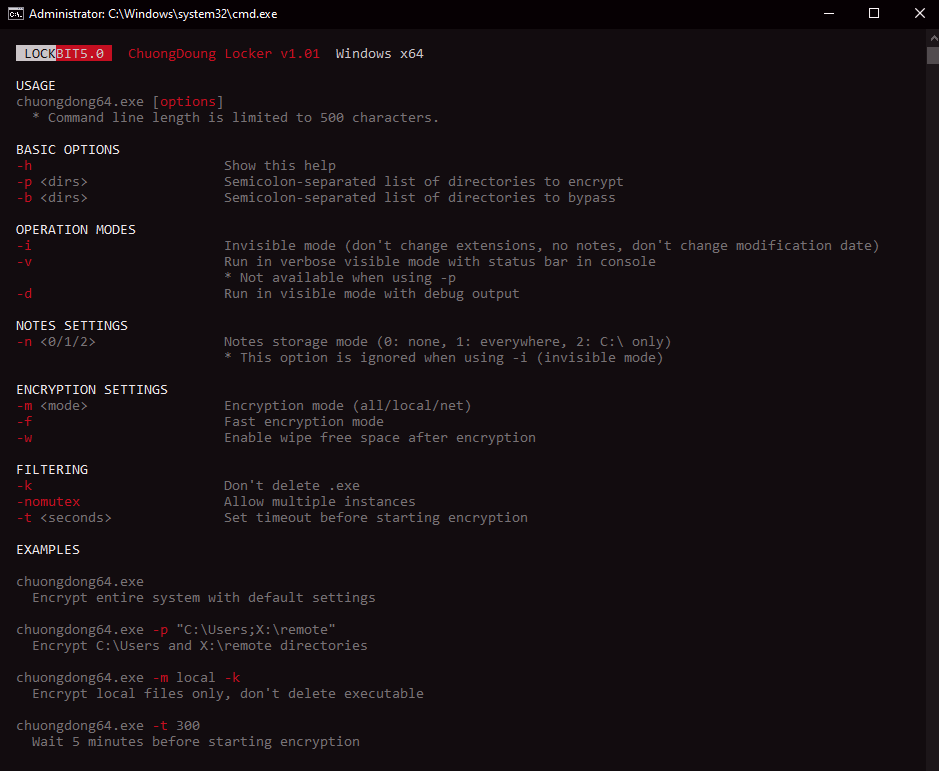
The Windows build supports extensive command-line customization, including an invisible mode (no file extension change, no ransom notes), network or local file encryption modes, wiping of free disk space, selective directory targeting or exclusions, and flexible ransom note delivery, including modes to drop them everywhere, on C:\, or not at all.
Trend Micro
The ransomware appends a randomized 16-character extension to each encrypted file and embeds the original file size in the footer, complicating identification and reverse engineering.
Trend Micro
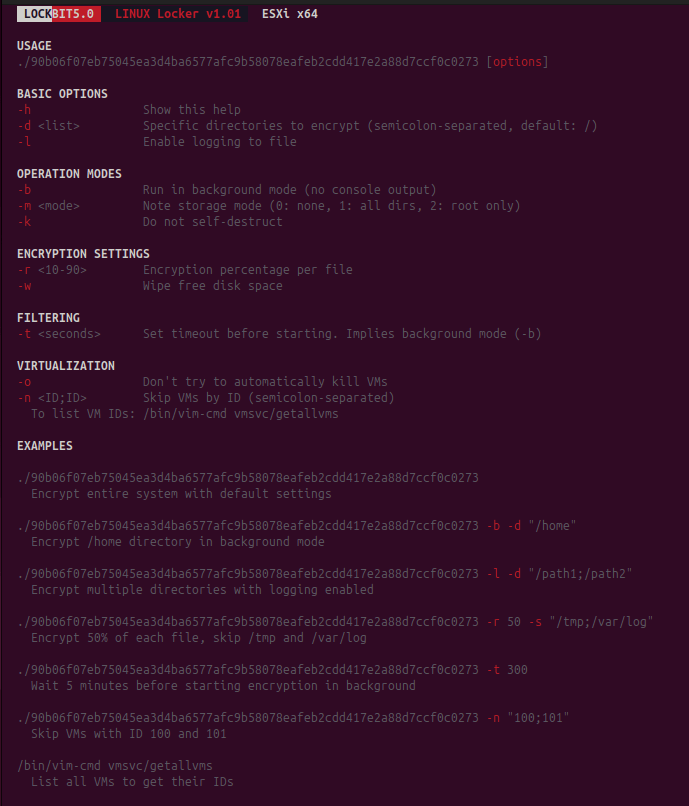
Linux and ESXi variants
LockBit 5.0’s Linux variant mirrors the Windows version’s functionality and layout, offering extensive command-line options. It logs each step of the encryption process, including file targeting and skipped folders.
The dedicated ESXi version targets VMware virtualization infrastructure, encrypting entire virtual machine environments through a single payload. This variant is particularly destructive in enterprise networks, where ESXi hosts often manage dozens or hundreds of VMs. Its interface and syntax remain consistent with the Windows and Linux versions, simplifying cross-platform deployments for attackers.
Trend Micro
Trend Micro found that LockBit 5.0 is not a rebrand or fork but an evolutionary upgrade from version 4.0. Code reuse is extensive, with the same hashing algorithms used for API resolution and string operations, and dynamic API calls follow nearly identical logic paths. The incremental updates, including more refined help menus, invisible operation modes, and enhanced anti-forensics, suggest a focus on usability and stealth.
LockBit in decline or in recovery?
LockBit operated as a Ransomware-as-a-Service (RaaS) since 2019, enabling affiliates to carry out attacks using shared infrastructure and tooling. It has been responsible for over 7,000 known attacks across 120 countries, with high-profile targets in healthcare, government, and critical infrastructure.
Operation Cronos, spearheaded by the UK’s National Crime Agency and supported by the FBI and international partners, dealt a major blow to the group in early 2024. It seized infrastructure, arrested members in the UK, France, and Spain, unmasked Khoroshev (LockBitSupp), and indicted developer Rostislav Panev, whose devices contained source code and control panel credentials.
LockBit’s reemergence with a technically refined variant raises important questions about its current standing. Following the global disruption from Operation Cronos, the group’s credibility has suffered among affiliates and the broader cybercriminal ecosystem.
While LockBit 5.0 demonstrates that the group retains some development capability, it remains unclear whether this latest version will achieve wide adoption. So far, there have been no high-profile breaches or victim announcements tied to the new variant.
Even with its criminal momentum stalled, security teams should remain vigilant and keep an eye out for potential LockBit 5.0 attacks, as the latest ransomware variant appears as capable as ever.






Leave a Reply