
Rapid7 has publicly disclosed a critical permission bypass vulnerability in multiple versions of OnePlus's OxygenOS that allows any installed app to silently access SMS and MMS content without user consent, interaction, or even the READ_SMS permission.
As of September 23, 2025, the flaw (CVE-2025-10184) remains unpatched, and OnePlus has not responded to multiple coordinated disclosure attempts.
The vulnerability affects the Telephony content provider in OxygenOS versions 12 through 15. By exploiting poorly protected custom content providers added by OnePlus to its Android implementation, a malicious app can extract the contents of SMS messages, including Multi-Factor Authentication (MFA) codes, without any declared permissions or user notifications. The attack vector also enables blind SQL injection, allowing for the exfiltration of full message data from the underlying SQLite database.
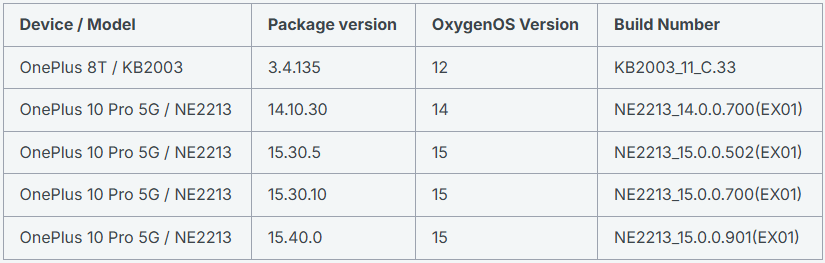
According to Rapid7, the bug does not exist in OxygenOS 11, suggesting it was introduced starting with OxygenOS 12 (released in 2021). The vulnerability was confirmed on a OnePlus 8T running OxygenOS 12, and several OnePlus 10 Pro 5G units running builds from OxygenOS 14 and 15, but is likely to affect many more models due to the systemic nature of the flaw in OnePlus’s platform codebase.
Rapid7
OnePlus, founded in 2013 and now a sub-brand under OPPO, is known for shipping high-performance Android phones with its customized OxygenOS skin. Despite offering a bug bounty program, the company has not responded to Rapid7’s disclosures since May 2025. Attempts to escalate through OnePlus support and through OPPO’s CNA representative also failed, and Rapid7 ultimately classified OnePlus as a non-responsive vendor.
Technical details
At the core of the issue is OnePlus’s modification of the com.android.providers.telephony package. Unlike stock Android, OnePlus ships additional exported content providers, namely:
com.android.providers.telephony.PushMessageProvider,
com.android.providers.telephony.PushShopProvider, and
com.android.providers.telephony.ServiceNumberProvider.
These components are misconfigured with weak permission enforcement, specifically allowing arbitrary client apps to perform read and write operations using SQL injection vectors in content provider queries. Rapid7 identified that the ServiceNumberProvider implements full insert and update methods without sanitization, making it possible to leverage blind SQL injection to infer and reconstruct SMS data, character by character.
An attacker can inject payloads into the WHERE clause of the update operation, using inferential boolean logic to determine the contents of SMS messages stored in the system's sms table. To support exploitation even when the database table is empty, the provider’s insert method allows adversaries to seed dummy data, satisfying exploitation preconditions.
Rapid7 demonstrated this attack using a proof-of-concept (PoC) app that requires no permissions and can infer recent SMS messages, including time-sensitive codes such as MFA tokens. The implications are serious, as even if a user exercises best practices around app permissions, malicious apps could silently defeat SMS-based authentication or exfiltrate private messages.
Rapid7
Until OnePlus publicly responds or issues a fix, users should remove unnecessary apps from their devices and switch from SMS-based MFA to authenticator apps. Also, use end-to-end encrypted messaging apps instead of SMS for sensitive communications.






Leave a Reply