
A new phishing-as-a-service (PhaaS) platform called Mamba 2FA has been identified, leveraging adversary-in-the-middle (AiTM) tactics to bypass multi-factor authentication (MFA). First discovered in May 2024 by Sekoia's Threat Detection & Research (TDR) team, Mamba 2FA has gained traction as a dangerous tool for cybercriminals seeking to exploit Entra ID accounts, Microsoft 365 services, and other enterprise systems.
Mamba 2FA was initially spotted when a partner alerted Sekoia to a phishing campaign using HTML attachments that mimicked Microsoft 365 login pages. These phishing kits could relay certain MFA methods, including one-time passwords and app notifications, thanks to the integration of the Socket.IO JavaScript library.
This setup allows real-time communication between phishing pages and back-end servers, helping attackers to bypass MFA protections. What first appeared as another variant of the Tycoon 2FA PhaaS platform turned out to be a previously undocumented kit, now known as Mamba 2FA.
Characteristics of Mamba 2FA
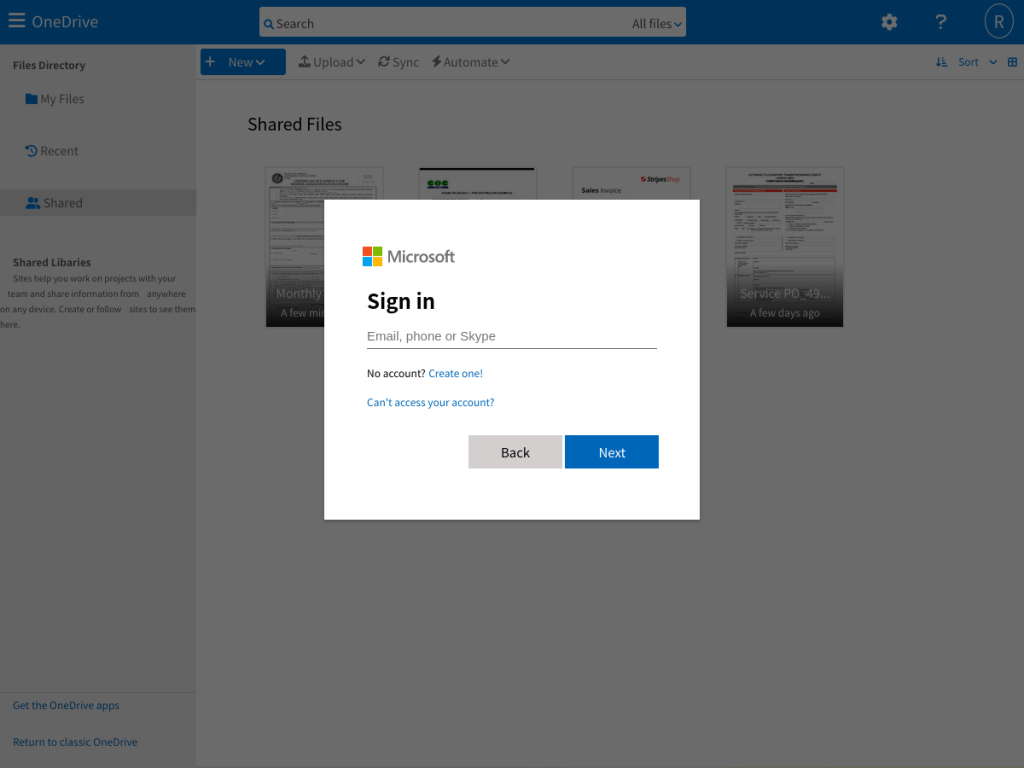
The phishing pages crafted by Mamba 2FA mimic legitimate Microsoft services, including OneDrive, SharePoint, and voice mail systems, to deceive victims. The phishing URLs follow a specific format, including Base64-encoded parameters that help identify the target and customize the phishing page accordingly.
Sekoia
For instance, these pages can display organization-specific branding to make the phishing attempt more convincing. If an invalid Base64 parameter is detected or automated browsing activity is identified, the page redirects the user to a benign error page, such as a 404 error on Google.
Key features of the phishing platform include the ability to:
- Handle non-phishing-resistant MFA methods like one-time codes and push notifications
- Support both corporate and consumer accounts, including Entra ID and AD FS
- Relay credentials and cookies to attackers in real time via Telegram bots
- Evade detection by blocking security scanning tools.
Mamba 2FA uses a sophisticated two-layer infrastructure comprising link domains, which handle initial phishing attempts, and relay servers, which are responsible for stealing credentials and completing login processes on behalf of the attacker. These relay servers, powered by the Socket.IO protocol, enable real-time communication between the victim’s actions (like entering an email or MFA code) and the phishing infrastructure.
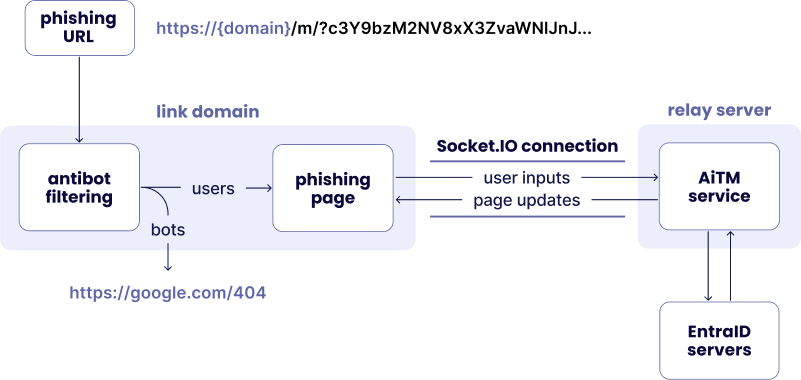
Sekoia
Commercialization and distribution
The service is marketed as a subscription-based phishing toolkit on Telegram, with a starting price of $250 for a 30-day access plan. Customers of Mamba 2FA can generate phishing links and HTML attachments on demand. These HTML attachments often contain benign-looking content to evade detection, with a hidden JavaScript snippet that redirects users to the phishing page.
Mamba 2FA has been in circulation since November 2023, although it gained wider attention in March 2024 when it was advertised on Telegram following the shutdown of its previous sales platform, ICQ. Since then, the developers have continuously updated the platform to circumvent new defensive measures, and the phishing infrastructure is regularly altered to avoid detection.
Impact and infrastructure
The ongoing phishing campaigns leveraging Mamba 2FA pose a significant threat to enterprises and individuals, especially those relying on Microsoft’s ecosystem for authentication. The phishing platform targets both consumer and enterprise accounts, with stolen credentials rapidly sent to attackers. Relay servers used by the kit can impersonate the victim to complete MFA-protected logins, and the phishing URLs are frequently rotated to prevent blacklisting.
The relay servers, previously exposed through authentication logs, are now masked by commercial proxies, making it harder for organizations to trace the attacks. Mamba 2FA maintains a dozen active domains at any given time, rotating them weekly to evade detection.
Defense recommendations
Organizations using Microsoft services should stay vigilant for phishing campaigns employing HTML attachments or redirecting users to unfamiliar URLs. To defend against Mamba 2FA attacks:
- Implement phishing-resistant MFA methods, such as hardware tokens or biometrics, where possible.
- Regularly monitor authentication logs for unusual sign-ins from proxy IP addresses.
- Use security solutions capable of detecting Base64-encoded parameters in phishing URLs and inspecting HTML attachments for hidden redirection scripts.
Key IP addresses and domains linked to Mamba 2FA’s relay servers are available in Sekoia's report to aid in detection. Regularly updating blocklists with these indicators of compromise can reduce exposure to phishing attempts leveraging this PhaaS.






Leave a Reply