
A malicious update to the popular npm package TinyColor has triggered a supply-chain attack that spread to more than 40 other projects, exposing developers to credential-stealing malware.
Researchers from Socket discovered that the compromised version of TinyColor contained hidden code designed to run automatically when installed. The malware searched for sensitive data, including GitHub and npm tokens, cloud credentials, and other secrets, before sending the information to an external server.
Feross Aboukhadijeh, founder and CEO of Socket, said on X, “This is one of the more advanced attacks we’ve seen recently. It targets developers’ machines, CI/CD pipelines, and cloud infra.”
With over 2 million weekly downloads, TinyColor’s popularity significantly increased the reach of the attack. Dozens of downstream packages across the npm ecosystem were affected, raising concerns that many developers may already have inadvertently integrated the compromised code.
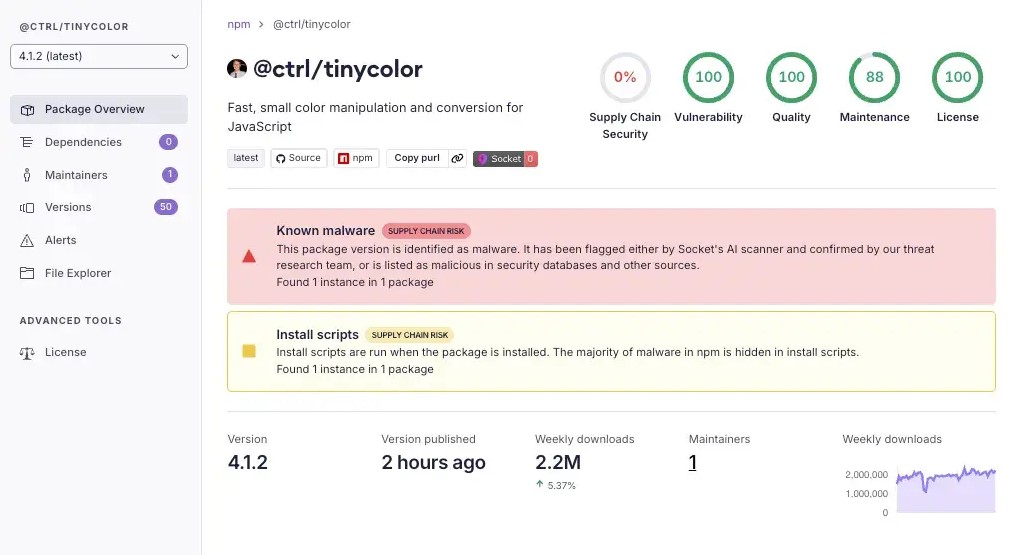
Security experts are advising developers to uninstall or roll back affected packages, rotate any exposed credentials, and carefully audit their systems for signs of compromise.
This marks the second major supply-chain attack on the npm ecosystem in under 10 days. On September 8, 2025, 18 widely used JavaScript packages were compromised, collectively amassing over 2 billion weekly downloads.







Leave a Reply