
Over the summer of 2024, nearly 5% of all Adobe Commerce and Magento stores were hacked, impacting high-profile brands like Ray-Ban, National Geographic, Cisco, Whirlpool, and Segway.
A new report from the Sansec Forensics Team reveals that at least seven different cybercriminal groups exploited the CosmicSting vulnerability, first disclosed in June, to plant payment skimmers on compromised checkout pages.
CosmicSting: widespread and ongoing threat
Since the vulnerability, identified as CVE-2024-34102 (CosmicSting), was disclosed on June 11th, hackers have breached over 4,275 stores. This follows warnings from Adobe about a critical security flaw and illustrates a major failure in patching across the e-commerce landscape. Despite Adobe issuing a security patch on July 8th and providing steps for manual key removal, many store owners did not invalidate old cryptographic keys, leaving their systems vulnerable to unauthorized access.
This comes after earlier reports in June and July that already warned of this critical threat, emphasizing how hackers exploited secret cryptographic keys to access store data and insert malicious payment skimmers into checkout processes via CMS blocks.
Threat groups and their techniques
Sansec identified seven separate groups exploiting CosmicSting, each using different approaches to steal cryptographic keys and plant skimmers. Unusually, because of the vulnerability’s nature, one hacker group cannot “lock out” another. This has led to multiple groups, sometimes up to three, competing over control of the same store.
Sansec
Each hacking group employs unique methods to obfuscate and deliver their skimming malware:
- Bobry: Hides malware within Unicode characters that are interpreted as JavaScript, making the code difficult to detect.
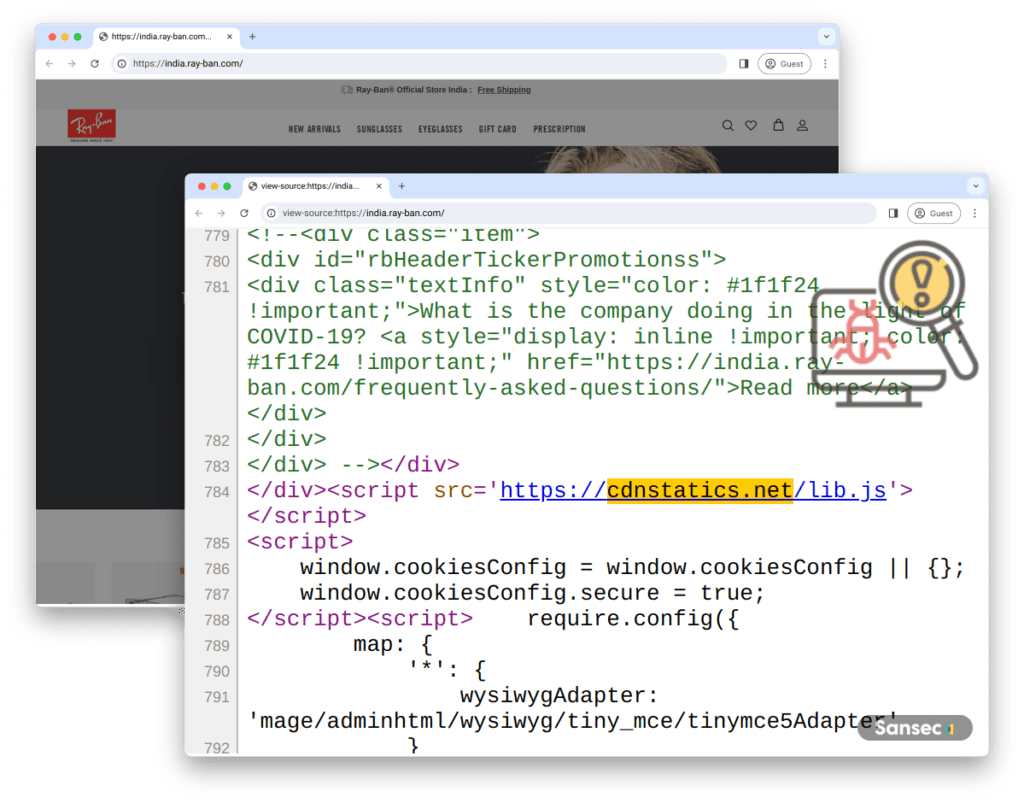
- Polyovki: Uses straightforward script injections hosted on cdnstatics.net, affecting over 650 stores, including Ray-Ban.
- Surki: Uses the number 42 for encryption, operating through domains like fallodick87-78.sbs to hide their skimmer payload.
- Burunduki: Connects to a websocket (wss://jgueurystatic.xyz:8101) to dynamically load the skimmer code in real time.
- Ondatry: Targets large merchants and customizes malware to match specific payment solutions, such as MultiSafePay in the Netherlands.
- Khomyaki: Exfiltrates data via two-character URI endpoints like cdn.myshopper.io/bo/, targeting high-profile stores like Cisco.
- Belki: Leverages CosmicSting with CNEXT for remote code execution (RCE), hiding backdoors in server files and processes.
Mitigation and defense
Sansec advises store operators to immediately upgrade to the latest version of Adobe Commerce or Magento and to rotate encryption keys, as failing to revoke old keys is a critical point of vulnerability. Merchants are strongly encouraged to use malware and vulnerability monitoring tools like Sansec’s eComscan, which has effectively shielded its users from CosmicSting attacks.
As of the report, approximately 75% of all Adobe Commerce and Magento installations remain unpatched, making the CosmicSting threat far from over. The attacks underscore the necessity of quick response to vulnerabilities and the importance of proactive monitoring to safeguard e-commerce stores against data breaches and financial theft.







Leave a Reply