
The Hook Android banking trojan has received a significant update, adding ransomware-style extortion to its already formidable arsenal of surveillance and fraud tools.
Zimperium's zLabs research team has identified “Hook v3” as the most advanced iteration of the malware to date, with 38 new remote commands that push it beyond traditional banking threats into spyware and ransomware territory.
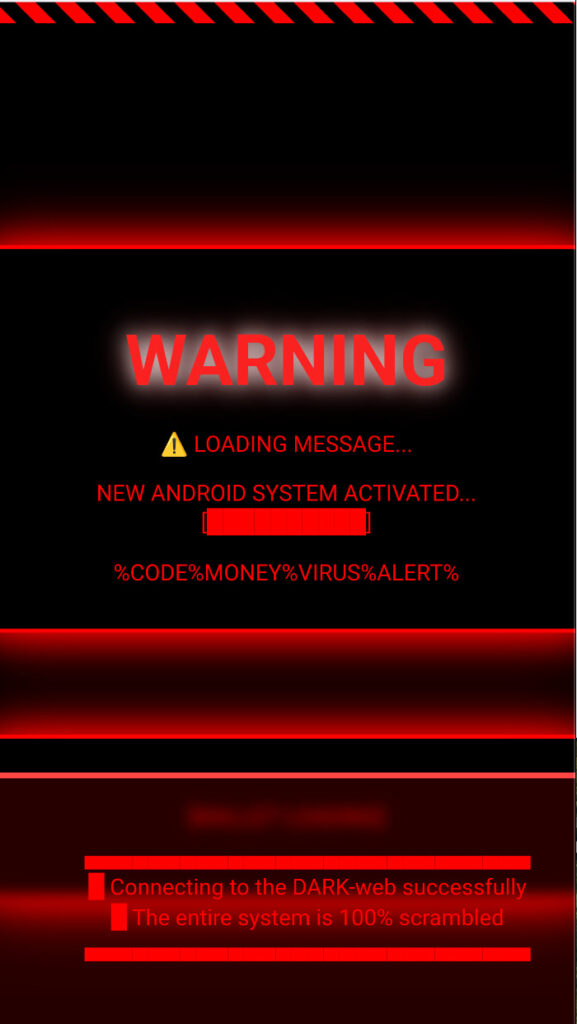
Hook, initially uncovered by ThreatFabric and previously tied to the Ermac malware family, has traditionally targeted financial fraud through remote control of infected Android devices. The latest variant escalates the threat level substantially. Among its new features is a full-screen ransomware overlay that mimics a traditional ransom note, displaying a threatening message and demanding payment via cryptocurrency, with wallet addresses and amounts dynamically fetched from its command-and-control (C2) infrastructure. This overlay is deployed via the ransome command and can be removed remotely by issuing a delete_ransome instruction.
Zimperium
Hook continues to abuse Android's Accessibility Services to automate user actions, hijack sessions, and collect credentials invisibly. It now supports 107 total commands, allowing attackers to stream device screens in real time, simulate user gestures, bypass lock screens, and deploy phishing overlays.
Zimperium's investigation revealed that Hook is being distributed not only through phishing websites but also via public GitHub repositories. Malicious APK files are being hosted alongside other Android malware families such as Brokewell and Ermac. This method of distribution increases the malware's accessibility to a wider range of threat actors and underscores the importance of code repository hygiene and proactive platform moderation.
Hook v3 also introduces fake NFC overlays (takenfc) designed to trick users into revealing sensitive data. These overlays use fullscreen WebView components and set up JavaScript interfaces for potential data capture, although Zimperium notes that some implementations are still incomplete, suggesting ongoing development. Similarly, the malware can mimic the Android lock screen via overlays (pincodep and patternp) to steal PINs and unlock patterns, which it then uses to unlock the device remotely using the unlock_pin command.
Zimperium
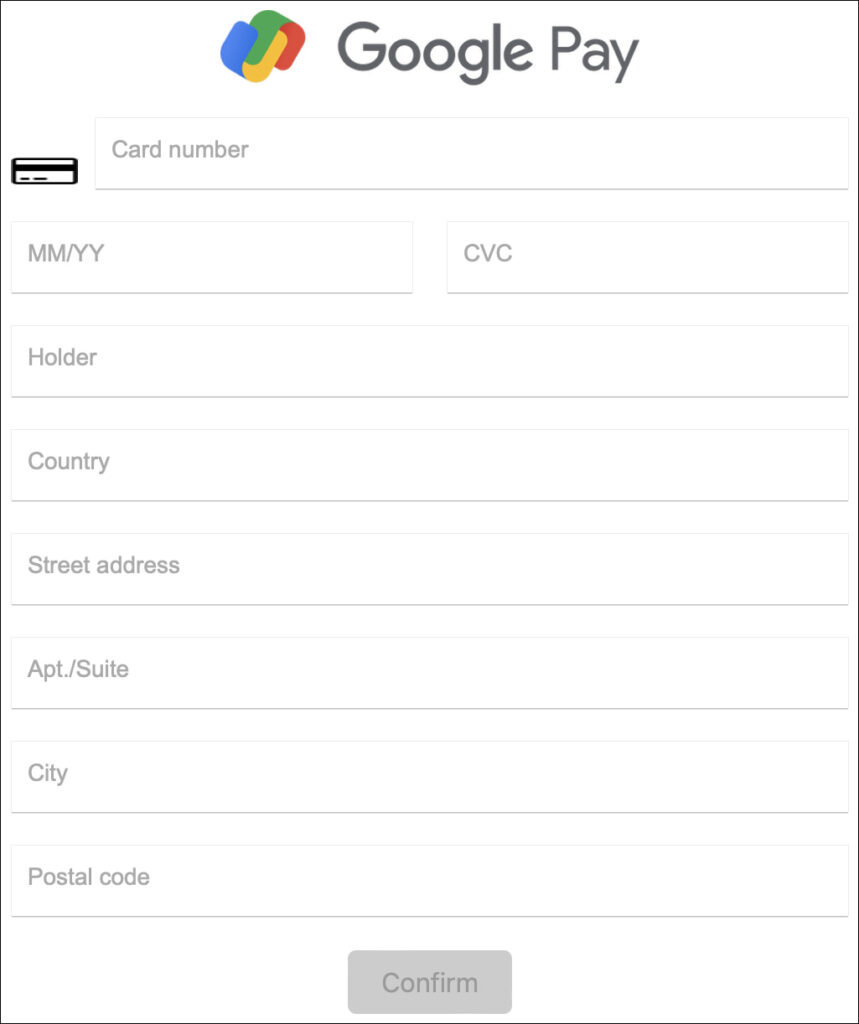
Hook is also capable of launching phishing overlays for apps like Google Pay (takencard) and cryptocurrency wallets, including MetaMask, Trust Wallet, and Coinbase, targeting credentials and seed phrases. Its keylogger, screen recording, and camera control functions allow it to operate as spyware, capturing audio, screen content, and even using the front-facing camera to take photos of the victim.
Strings and command structures indicate the malware may eventually leverage Telegram bots for additional command dissemination, although no functional implementation has been observed yet.
Hook's origin ties back to underground malware marketplaces where it was once openly sold, but the current variant appears to be under more centralized control, based on observed consistency in functionality and infrastructure.
Zimperium reports that it has worked with industry partners to remove at least one GitHub repository used for distributing Hook, but warns that the trojan remains an active threat.







Leave a Reply