
Researchers at Proofpoint have identified a way for attackers to bypass FIDO-based passkey authentication using a downgrade attack, potentially exposing accounts once considered “phishing-resistant” to adversary-in-the-middle (AiTM) compromise.
While the technique has not yet been observed in real-world campaigns, Proofpoint says the method is technically feasible and could be weaponized by sophisticated actors.
The discovery by Proofpoint threat researcher Yaniv Miron shows that attackers can adapt existing AiTM phishing frameworks, such as Evilginx, to force users away from FIDO authentication toward weaker fallback methods. The process relies on a custom “phishlet,” a configuration file used by phishing kits to impersonate legitimate websites and intercept login data. Most current phishlets fail against FIDO-protected accounts, but Proofpoint’s proof-of-concept shows how that limitation can be overcome.
FIDO (Fast Identity Online) standards, developed by the FIDO Alliance, are designed to eliminate passwords and resist phishing by combining cryptographic authentication with hardware tokens and biometrics. Many organizations implement FIDO through services like Microsoft Entra ID, often alongside a backup MFA method for account recovery. It’s this fallback option that the downgrade attack exploits.
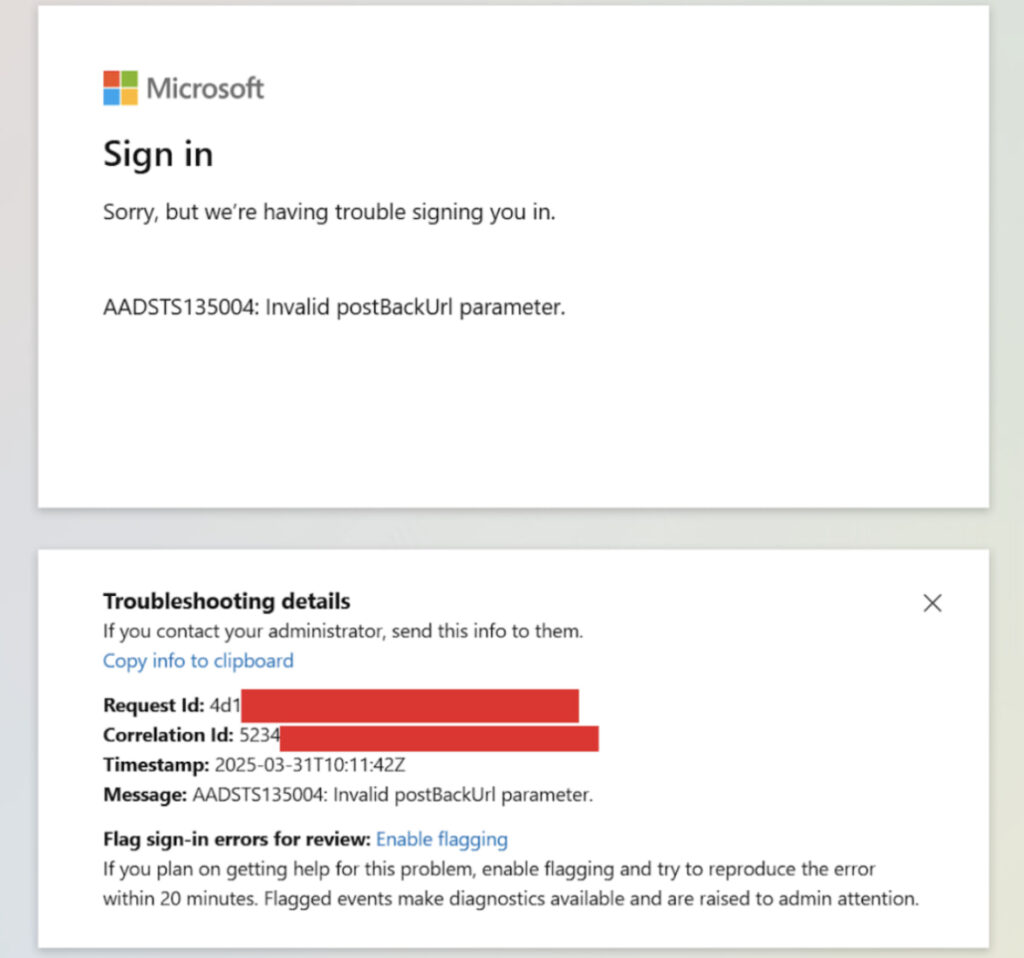
In the attack scenario described by Proofpoint, a victim is lured to a malicious link delivered via email, SMS, or an OAuth consent request. The AiTM setup spoofs a browser user agent that is incompatible with FIDO (for example, Safari on Windows). This triggers an authentication error, prompting the victim to select an alternative method, such as an authenticator app or SMS-based OTP.
Proofpoint
Once the victim completes this weaker authentication step, the attacker intercepts both credentials and the session cookie, enabling full account takeover without needing to solve another MFA challenge.
Proofpoint
Although there is no evidence of this technique being used in active campaigns, Proofpoint warns that it could appeal to advanced persistent threats (APTs) and technically adept cybercriminals in the future, especially as more organizations deploy FIDO-based protections. For now, most attackers prefer easier targets, such as accounts without MFA or those using less robust MFA methods, which can be compromised with existing phishing tools.
Defense recommendations
To mitigate the risk of FIDO authentication downgrades, Proofpoint advises:
- Enforcing FIDO-only authentication where feasible, without fallback to weaker methods.
- Monitoring for browser user agent anomalies that may indicate spoofing attempts.
- Being cautious when prompted to “try another sign-in method,” especially if their usual method fails unexpectedly.
- Restricting account recovery paths to secure, phishing-resistant channels.
While FIDO remains one of the strongest authentication options available, Proofpoint’s findings underscore that no security control is immune to adaptation by determined adversaries.







Leave a Reply