
A covert and technically advanced exploitation campaign targeting Ivanti Cloud Service Appliances (CSA) between September and November 2024 has been attributed to a threat cluster tracked as Houken.
France’s cybersecurity agency, ANSSI, has published a detailed report on the operation, which leveraged three zero-day vulnerabilities to breach networks across key French sectors, including government, telecom, media, finance, and transport.
ANSSI's analysis reveals that the Houken intrusion set exploited vulnerabilities CVE-2024-8190, CVE-2024-8963, and CVE-2024-9380 in Ivanti CSA devices to execute remote code and establish persistent access. Attackers used a base64-encoded Python script to extract admin credentials from local PostgreSQL databases, planted PHP webshells, tampered with legitimate scripts for covert access, and in some cases, installed a rootkit enabling full control over infected systems.
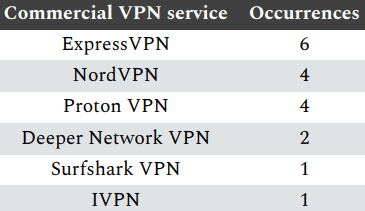
The infrastructure behind the Houken campaign was diverse and layered. Attackers routed their traffic through commercial VPNs, notably NordVPN, ExpressVPN, and Proton VPN, anonymization services like Tor, and residential or mobile IP addresses across China, the U.S., and India. Command and control (C2) traffic was traced to VPS providers like HostHatch, ColoCrossing, and JVPS.hosting. Some servers were used both for deploying reverse shells and for staging malware via curl or wget commands.
On the tooling side, Houken operators made heavy use of open-source utilities favored among Chinese-speaking threat actors. These included webshell frameworks like Neo-reGeorg and Behinder (“Ice Scorpion”), reverse shell tools like GOREVERSE and suo5, and credential-harvesting tools such as Searchall. The group also employed OAST tools (e.g., Eyes.sh and Interactsh) for application security testing.
A particularly alarming element was the discovery of a rootkit named sysinitd, composed of a kernel module (sysinitd.ko) and a userland binary. Once deployed, it enabled remote root command execution via TCP hijacking, a highly advanced persistence technique, suggesting the attackers viewed some targets as especially valuable.
ANSSI further identifies “Houken” as likely being operated by the same actor behind UNC5174, a threat group previously linked by Google's Threat Intelligence team to China's Ministry of State Security (MSS). This conclusion is supported by shared TTPs, reused infrastructure, and similar payloads, including the suo5 webshell (OutlookEN.aspx), which had previously been deployed in Chinese state-sponsored campaigns like Hafnium.
UNC5174 has a documented history of exploiting edge devices, including F5 BIG-IP (CVE-2023-46747), ConnectWise ScreenConnect (CVE-2024-1709), and Palo Alto (CVE-2024-3400). The Houken campaign represents a technical escalation in UNC5174's arsenal with the observed use of previously unknown zero-days and custom rootkits.
ANSSI warns that Houken's targeting extends globally, with preferred victims located in Southeast Asia, Western government bodies, NGOs, and educational institutions. While initial access appears to be the primary goal, likely for resale to state-affiliated actors, data exfiltration and even cryptomining were observed, underscoring a profit-driven component. As of mid-2025, both Houken and UNC5174 remain active, warns ANSSI, and further exploitation of internet-facing appliances is anticipated by the agency.







Leave a Reply