
A series of critical vulnerabilities in Bluetooth chips from Taiwan-based Airoha allow attackers within wireless range to hijack headphones, read memory, impersonate trusted devices, and, in some cases, eavesdrop on conversations.
The flaws, discovered by German cybersecurity firm ERNW and first reported by Heise Online, affect dozens of headphone models from brands such as Sony, JBL, Bose, and Marshall, with no comprehensive firmware fixes available yet.
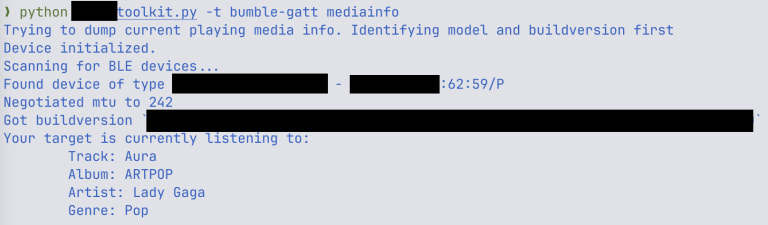
The vulnerabilities were first presented publicly at the TROOPERS 2025 security conference in Germany. According to ERNW’s follow-up security advisory, the flaws stem from a custom debugging protocol exposed via both Bluetooth Low Energy (BLE) and Bluetooth Classic (BR/EDR), implemented in Airoha’s reference software development kits (SDKs). This protocol, intended for vendor diagnostics or app features, lacks authentication entirely, allowing any nearby device to access memory and issue commands without pairing.
Turning Bluetooth earbuds into bugs
ERNW confirmed that three vulnerabilities (CVE-2025-20700, CVE-2025-20701, and CVE-2025-20702) enable full device compromise with no user interaction:
- CVE-2025-20700 – Missing authentication in BLE GATT services
- CVE-2025-20701 – Unauthenticated access over Bluetooth Classic
- CVE-2025-20702 – Critical protocol features allow arbitrary memory read/write
Attackers in Bluetooth range (~10 meters) can read RAM to determine what media is playing, extract phone numbers and call logs from connected smartphones, and hijack Bluetooth connections by stealing cryptographic pairing keys. Using these keys, adversaries can impersonate headphones to a victim’s phone, triggering silent calls or issuing voice commands. In lab settings, ERNW successfully turned headphones into listening devices by routing their microphone input to a rogue Bluetooth device or by initiating phone calls without user interaction.
ERNW
While these attacks are complex and require a local attacker with advanced tooling and close proximity, the danger is significant for high-risk individuals such as journalists, diplomats, and corporate executives.
Broad impact
Airoha is a major supplier of Bluetooth SoCs for the True Wireless Stereo (TWS) market, with its chips present in both budget and premium models. While Apple’s AirPods are unaffected, the following devices were confirmed by ERNW to be vulnerable:
- Sony WH-1000XM4/5/6, WF-1000XM3/4/5, LinkBuds S, ULT Wear, CH-720N, C500, C510-GFP, XB910N
- Marshall ACTON III, MAJOR V, MINOR IV, MOTIF II, STANMORE III, WOBURN III
- JBL Live Buds 3, Endurance Race 2
- Jabra Elite 8 Active
- Bose QuietComfort Earbuds
- Beyerdynamic Amiron 300
- Jlab Epic Air Sport ANC
- Teufel Airy TWS 2
- MoerLabs EchoBeatz
- Xiaomi Redmi Buds 5 Pro
- earisMax Bluetooth Auracast Sender
ERNW emphasizes that this is only a partial list. Due to opaque supply chains and frequent outsourcing, many manufacturers may be unaware they are using Airoha components. Some devices exhibit partial mitigation of certain CVEs, but whether this was intentional or coincidental remains unclear.
Patch status
The vulnerabilities were responsibly disclosed to Airoha on March 25, 2025, but the company only responded on May 27, after multiple contact attempts. Airoha issued updated SDKs to partners on June 4, but as of late June, most manufacturers have not issued firmware updates. Many products still run firmware older than the SDK fix, making this a live zero-day in millions of devices.
Adding to the challenge, firmware updates for headphones are typically distributed via proprietary mobile apps, which users seldom install or open. In some cases, older or budget models may no longer receive updates at all.
It is recommended that users check manufacturer apps regularly for firmware updates, turn off Bluetooth when not in use to reduce exposure, and avoid using headphones in sensitive locations.







Leave a Reply