
Cloudflare has launched a fully end-to-end encrypted version of its video calling app, Orange Meets, marking a significant step toward private real-time communication without sacrificing scalability or usability.
The implementation relies entirely on client-side encryption using the Messaging Layer Security (MLS) protocol, requiring no changes to Cloudflare's media-forwarding infrastructure.
The development follows the 2024 debut of Cloudflare Realtime (formerly “Cloudflare Calls”) and the open-source video app Orange Meets. While the platform already offered scalable video calls via a Selective Forwarding Unit (SFU), this central routing model typically introduces a privacy tradeoff, allowing the SFU to potentially view or process the unencrypted content. Cloudflare has now addressed this limitation by integrating true end-to-end encryption (E2EE) into Orange Meets using a standards-based, client-only approach.
Privacy at the protocol level
Unlike text-based communication apps, where messages can be encrypted multiple times for each participant, video conferencing demands a more efficient encryption scheme due to real-time and high bandwidth constraints. Cloudflare implemented MLS, a group key exchange protocol standardized by the IETF, as the foundation for securing communications between participants.
The encryption system is built entirely on the client side using WebAssembly (WASM)-compiled Rust code. A dedicated encryption worker processes WebRTC video and audio frames before transmission and performs decryption upon receipt. To remain compatible with common codecs like VP8, the implementation preserves specific unencrypted byte headers in each frame, following an approach documented by Discord's DAVE protocol.
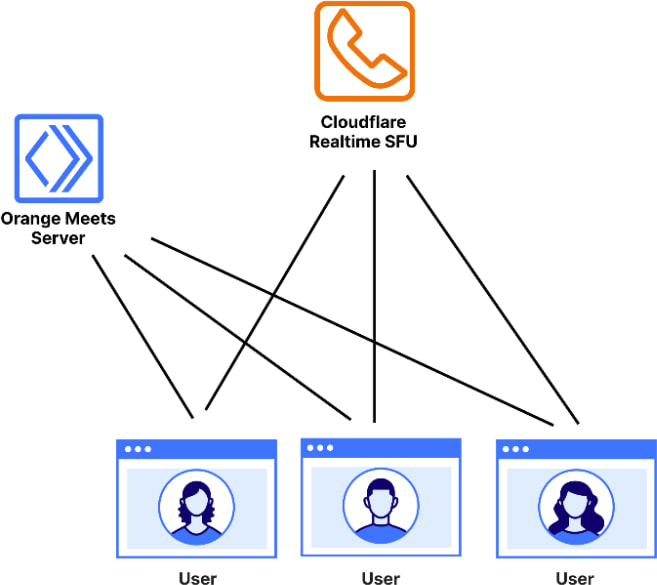
Orange Meets is built on three key components:
- Client: Each user runs the encryption and decryption logic locally.
- Orange Meets Server: A lightweight coordination service built with Cloudflare Workers, responsible for managing room states (e.g., participant lists, mute status).
- Cloudflare Realtime SFU: Forwards media streams without inspecting or modifying content.
Importantly, the SFU remains agnostic to encryption, forwarding UDP-based video/audio packets regardless of whether the contents are encrypted.
Cloudflare
“Designated Committer” algorithm
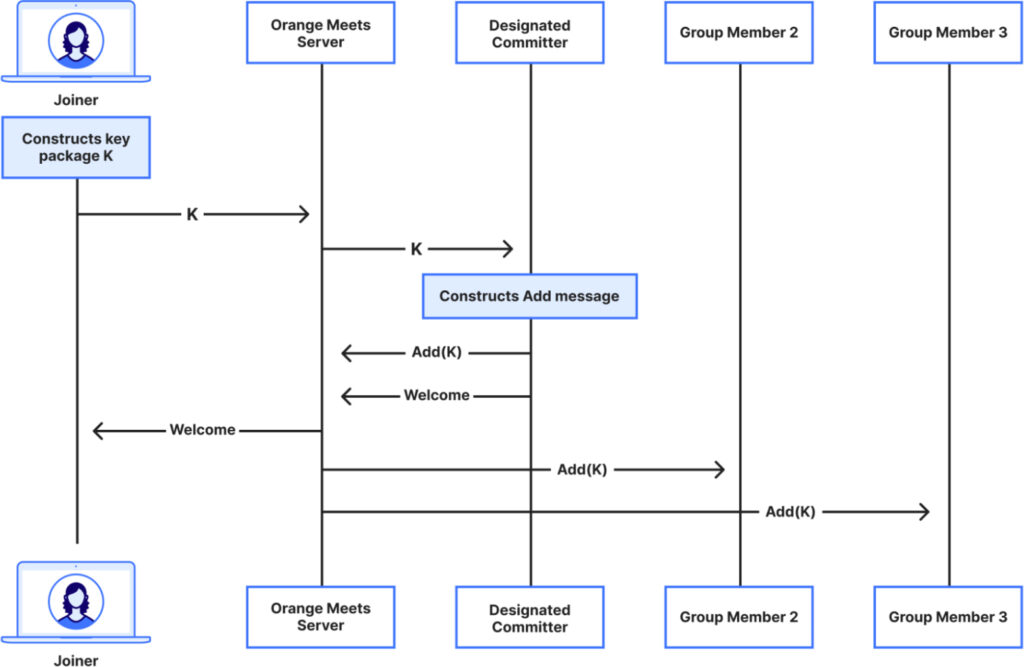
One technical hurdle in encrypted group video chats is managing dynamic membership securely, especially when users join or leave during a call. Rather than relying on centralized control or modifying the coordination server, Cloudflare introduced a lightweight algorithm called the designated committer.
When a new user joins, they send cryptographic material to one existing participant (the designated committer), who constructs and disseminates MLS group updates. The role of committer dynamically shifts if users disconnect, with group state ensuring continuity. This approach avoids involving the backend server in cryptographic operations, preserving decentralization and transparency.
To ensure correctness and handle edge cases, the algorithm was formally modeled and verified using TLA+, a specification language and model checker. This verification process helped uncover and fix subtle race conditions in scenarios involving membership churn.
Cloudflare
Ensuring authenticity
To guard against “monster-in-the-middle” attacks, where a compromised server injects malicious key material, Orange Meets displays a cryptographic safety number on the screen. Participants are advised to confirm this number via an external, trusted channel, such as a Signal group chat. This mechanism mirrors best practices seen in secure messaging apps and deters tampering with user keys.
Looking ahead, Cloudflare is exploring Web Application Manifest Consistency, Integrity, and Transparency, akin to its Code Verify project for WhatsApp, as a defense against malicious JavaScript delivery, a known vulnerability in browser-based encryption setups.
Cloudflare's implementation is open-source, modular, and adaptable to any WebRTC-based infrastructure, making it a promising foundation for other developers aiming to bring E2EE to group video communication. While further improvements are planned, including identity verification enhancements via OpenPubkey, the core system is functional and ready for deployment today.
Users can try the encrypted version of Orange Meets at e2ee.orange.cloudflare.dev, or self-host their own instance using the available codebase on GitHub.







Leave a Reply