
A newly discovered spyware campaign dubbed SparkKitty has infiltrated both the Apple App Store and Google Play, exfiltrating user photos in search of cryptocurrency wallet seed phrases.
The malware embeds itself in seemingly innocuous apps, including TikTok mods, casino games, and crypto utilities, using malicious frameworks and code injection techniques to steal sensitive user data.
The campaign was uncovered by Kaspersky researchers who linked it to SparkCat, first identified in early 2025. The earlier campaign distributed malicious SDKs through both official and third-party platforms, targeting screenshots of seed phrases using OCR (optical character recognition) to extract wallet recovery data. SparkKitty appears to be an evolution of this earlier effort, retaining key capabilities while expanding both technically and geographically.
Uncovering SparkKitty
Kaspersky analysts began investigating after noticing suspicious Android apps masquerading as TikTok mods. These apps displayed storefronts accepting crypto payments via embedded WebViews. Intriguingly, they also connected to a known configuration server, triggering deeper scrutiny. Upon further inspection, the researchers found similar activity targeting iOS users, where malicious provisioning profiles were used to sideload spyware-laced applications, bypassing App Store restrictions.
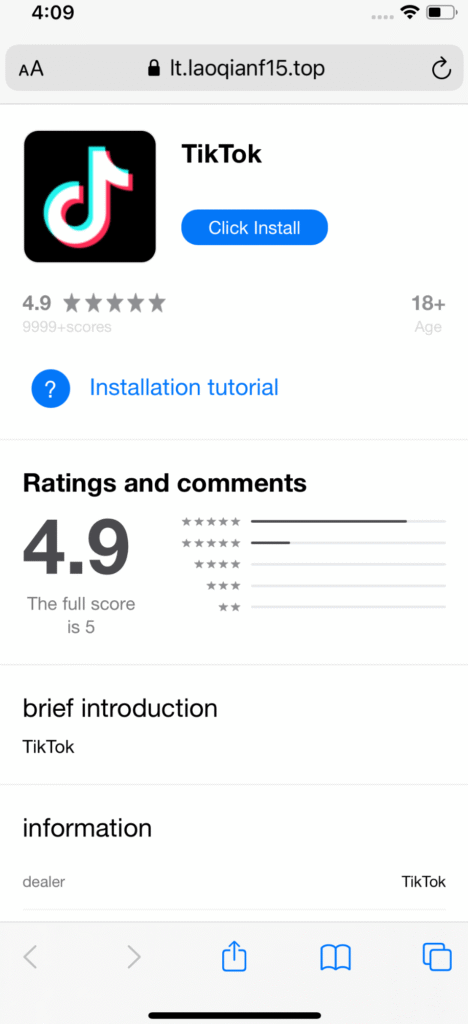
Kaspersky
What began as an inquiry into rogue e-commerce apps rapidly expanded into a wider campaign analysis. Through code analysis, dynamic testing, and cross-referencing with known SparkCat indicators, the team pieced together a sprawling operation using diverse infection vectors and targeting methods.
The SparkKitty campaign has been active since at least February 2024 and appears to focus on stealing cryptocurrency wallet recovery data through image theft. While most SparkKitty variants now indiscriminately steal images, many include machine learning models to filter and select photos containing text, consistent with an ongoing interest in crypto assets. Several infected apps even embed crypto-only e-commerce stores, reinforcing this theory.
Victims are predominantly located in Southeast Asia and China. Most infected apps are themed around gambling, TikTok modifications, or adult content — all popular vectors in the region. Many apps were distributed through domains hosting both APKs and progressive web apps (PWAs), with traffic often funneled via scam ads and crypto-related Ponzi schemes on platforms like YouTube.
iOS and Android mechanics
SparkKitty variants on iOS use modified libraries disguised as legitimate frameworks such as AFNetworking.framework, Alamofire.framework, or libswiftDarwin.dylib. The iOS payload activates via the +[AFImageDownloader load] selector, a hook executed at app launch. It decrypts embedded configuration files using AES-256 in ECB mode, extracts command-and-control (C2) server addresses, and initiates photo exfiltration only after receiving an explicit “OK” status from the server.
On Android, the malware comes in both Java and Kotlin variants. The Kotlin-based versions are deployed as Xposed modules, capable of hooking into app lifecycles and injecting code at runtime. One Android version checks a .DEVICES file containing an MD5 hash of the victim’s device identifiers. If conditions are met, it uploads photos to /api/putDataInfo, including user and device metadata.

Kaspersky
Several trojanized apps, including the crypto-themed 币coin and SOEX Messenger, were found live in Google Play and the App Store. Notably, some iOS samples used Apple’s enterprise provisioning profiles issued under the name “SINOPEC SABIC Tianjin Petrochemical Co. Ltd.” to sideload spyware onto users’ devices, bypassing standard App Store safeguards.
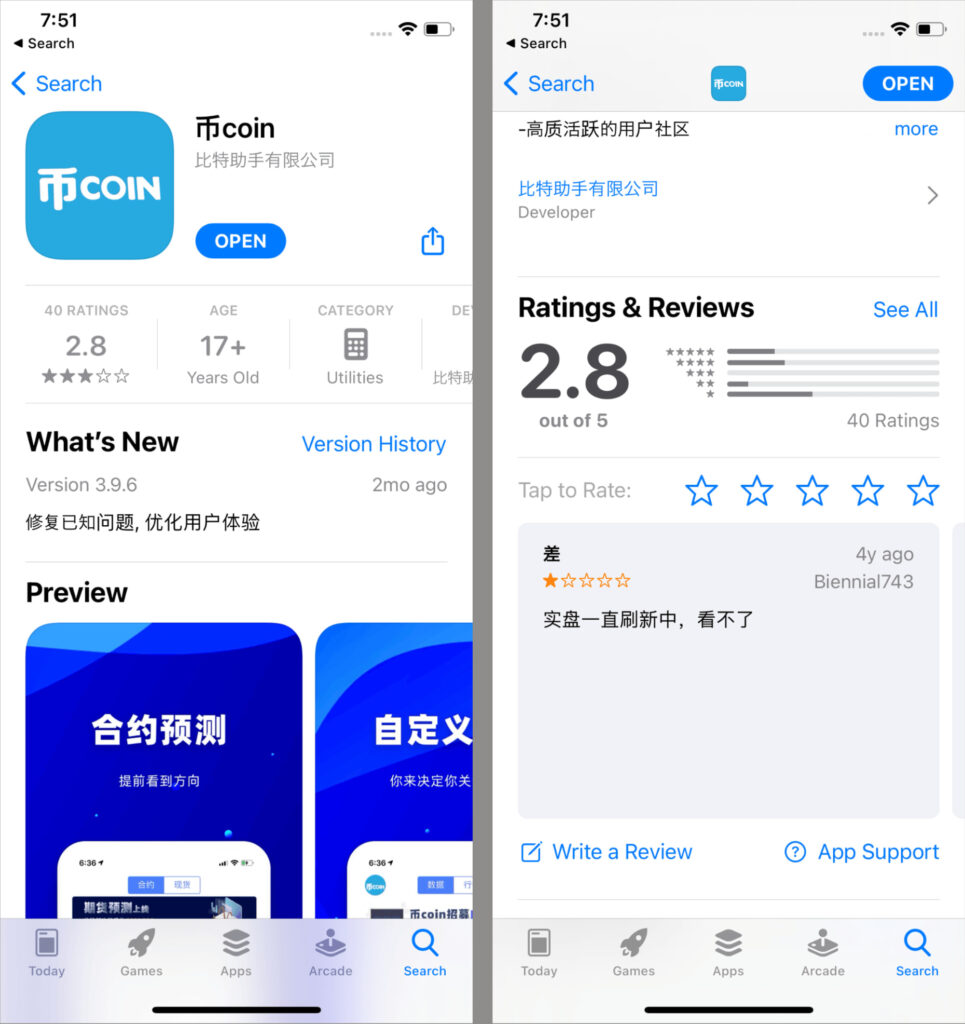
Kaspersky
To protect against SparkKitty:
- Avoid downloading apps from unofficial sources or links shared via social media or untrusted websites.
- When downloading from official sources, always read user reviews, research the publisher’s trustworthiness, and look for suspicious signs.
- On iOS, never install provisioning profiles unless absolutely necessary and only from trusted sources.
- On Android, be cautious of apps requesting gallery or storage access without a clear reason.
- Keep security software updated and regularly scan for spyware or unauthorized configurations.
- Revoke permissions for apps that don’t need access to personal media, especially photo galleries.







Leave a Reply