
A data breach at Cock.li, a privacy-oriented email provider known for its unconventional branding and anti-censorship stance, has exposed the login metadata of over 1 million users and contact details of more than 10,000 accounts.
The breach stems from a compromise of the provider’s outdated Roundcube webmail system and was confirmed by the service via an announcement published on its main website yesterday.
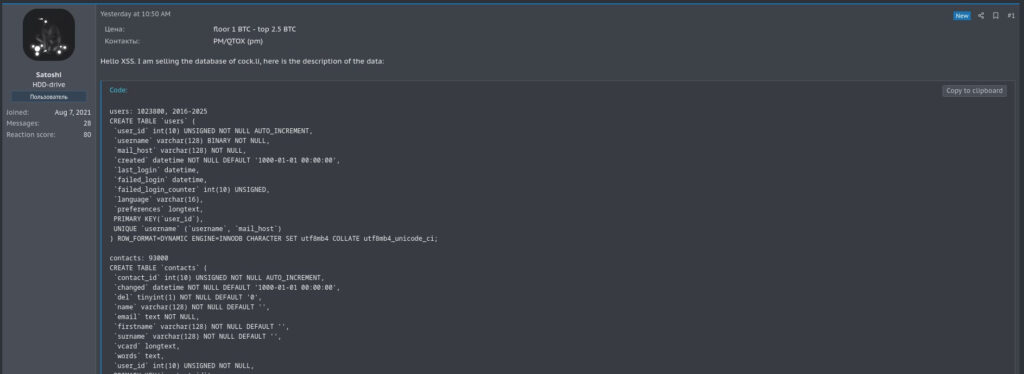
The breach came to light after a threat actor began circulating two database tables, users and contacts, on underground forums, claiming to have exfiltrated them by exploiting a known vulnerability in Roundcube. Initial signs of trouble surfaced days earlier, when Cock.li’s webmail portal was taken offline without warning. Users on social media noted the absence of a formal notice and speculated about the possibility of an exit scam. Soon after, a hacker claimed responsibility for compromising the platform via a Roundcube remote code execution (RCE) flaw, CVE-2025-49113.
@ReyXBF | X
Cock.li confirmed the validity of the breach based on sample data and column structure, stating that the exposed dataset includes roughly 1,023,800 user records. The compromised fields include email addresses, timestamps of first and last webmail logins, failed login attempt data, language preferences, and serialized Roundcube user settings such as webmail signatures and interface configurations. Additionally, approximately 93,000 contact entries associated with around 10,400 users were leaked, containing names, email addresses, comments, and vCard data.
Founded in 2013, Cock.li operates out of Germany and caters to users seeking pseudonymous email accounts. The service is widely used in online communities that value anonymity, including some that are politically fringe or marginalized from mainstream platforms. Despite its controversial branding, it has been recognized for maintaining a functioning and technically sound mail service for over a decade.
Despite this exposure, Cock.li emphasizes that no passwords, email message contents, or IP addresses were included in the breach. Passwords were stored in a separate sessions table, which was not among the leaked assets. The breach only affects users who accessed their accounts via Roundcube’s webmail interface at any point between 2016 and the feature’s deprecation earlier this month. Cock.li administrators sent targeted notifications to users with contact data included in the leak.
The likely root cause is an outdated instance of Roundcube running vulnerable code traced back to a PHP function dating from 2005. In their technical assessment, Cock.li references CVE-2021-44026, an older SQL injection vulnerability, as a potential culprit, though they stop short of confirming the exact exploit path. Interestingly, the administration had already disabled Roundcube permanently just prior to learning of the leak, citing long-standing concerns about its code quality and security track record.
In a characteristically candid announcement, Cock.li acknowledged that the breach could have been avoided with more proactive updates, noting, “Cock.li should not have been running Roundcube in the first place.” The team confirmed that no new webmail platform is currently in development and advised users to switch to desktop or mobile mail clients.







Let’s hope that most people were sane enough to use their own local mail clients instead of a web client, this is a prime example of why you should run your own mail client on your computer, rather than relying on any client provided as a service.