
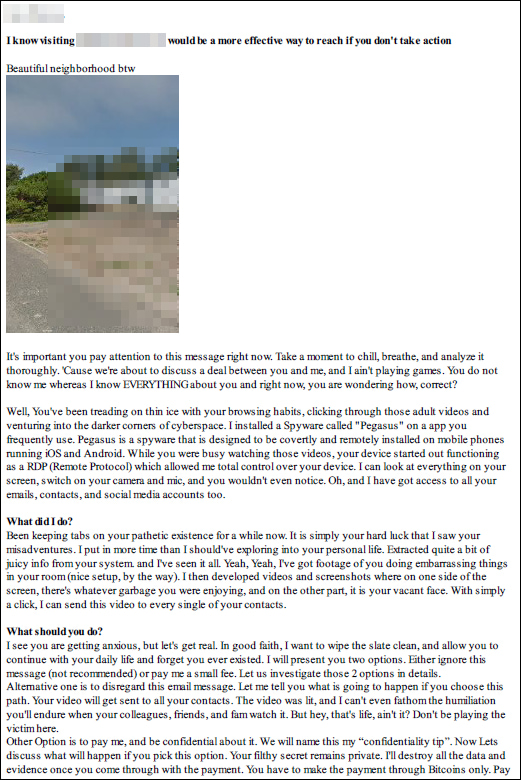
A new sextortion scam is alarming victims in the U.S. and Canada by using personal details, including images of targets' homes from Google Street View, to manipulate and extort them. This wave of scams takes a more invasive approach, leveraging personal information collected from data breaches to make the threats appear more credible.
Avast reports that the scammers use a combination of phishing and extortion tactics to intimidate victims into paying ransoms. The emails include PDF attachments containing the victim's name, phone number, and even images of their homes, adding a chilling sense of personalization. These details are likely obtained from public sources or data breaches, enhancing the sense of threat and urgency for victims.
The scam follows a typical sextortion formula, where the attackers claim to have hacked the victim's device using the notorious Pegasus spyware — an advanced tool typically reserved for state-sponsored surveillance of high-profile individuals. The attackers falsely assert they have recorded compromising videos of the target while watching adult content and threaten to release the footage unless a Bitcoin ransom is paid. In reality, there is no evidence supporting these claims, and the threats are purely psychological.
Avast
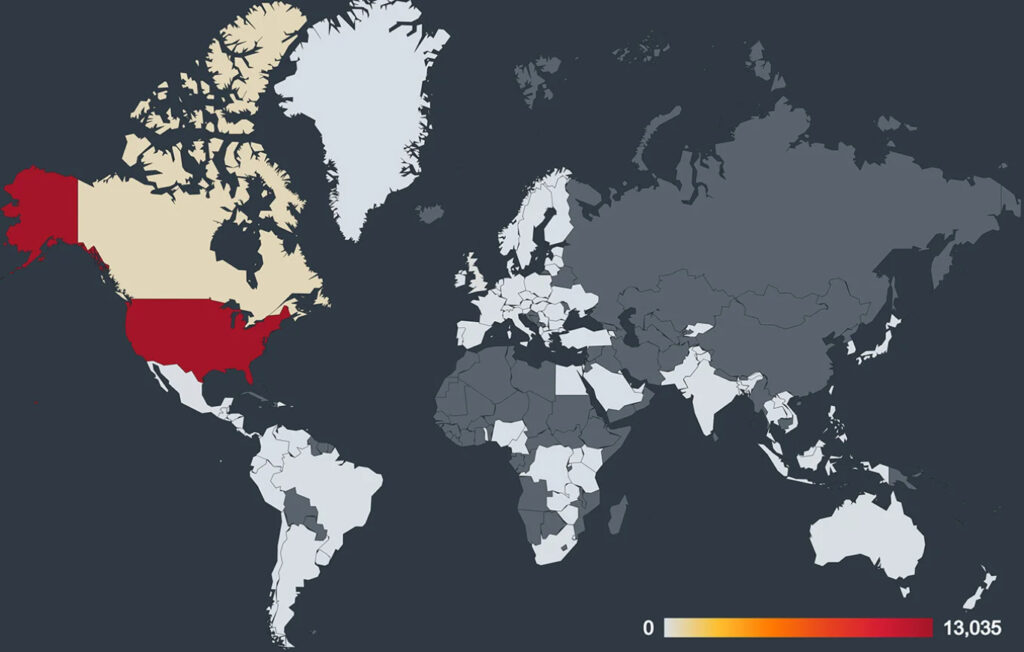
Victims are directed to pay via Bitcoin using a provided wallet address or QR code. Avast has identified over 15,000 unique Bitcoin wallets associated with this scam, although only two wallets have recorded transactions so far, totaling $3,674. A deeper investigation revealed that these funds were consolidated into a primary attacker wallet, which holds approximately $128,114 in Bitcoin. This indicates that the true scope of the operation may be far larger, with numerous undiscovered transactions across other wallets.
Avast's report highlights the unsettling evolution of sextortion scams, moving from generic threats to more personalized attacks that exploit publicly available data like Street View images. The combination of real-life details with false spyware claims creates a potent scare tactic designed to pressure victims into paying.
Avast
The use of Google Street View adds a novel layer of personalization to these scams, setting them apart from more traditional phishing attempts. This tactic plays into the victim's fear that their privacy has been invaded on a deeper level. While Google Street View images are publicly accessible, the inclusion of such imagery in sextortion emails makes the threat seem more tangible and immediate.
Users are advised to do the following to defend against those threats:
- Avoid responding or engaging with the sender.
- Avoid opening PDF attachments or links sent via unsolicited communications.
- Mark these messages as spam to help prevent others from being targeted.
- If you're targeted by sextortionists, report it to the authorities.
- Be cautious when sharing personal information online.
- Create strong, unique passwords and enable two-factor authentication (2FA) on your accounts.







Leave a Reply