
The Tor Project has introduced a new privacy tool named oniux, offering robust traffic isolation for Linux applications via kernel-level namespace separation and Tor routing.
Developed by privacy advocate cve and built on top of the Arti Tor implementation and onionmasq, oniux aims to eliminate common data leakage risks associated with SOCKS-based Tor proxies like torsocks.
The tool was released on GitLab as a command-line utility targeting Linux environments where security and anonymity are paramount, such as activist workflows, journalistic investigations, and sensitive research. Rather than relying on traditional proxy wrapping, oniux uses Linux kernel namespaces to isolate individual applications within separate network stacks, routing all their traffic exclusively through Tor. This ensures that even misconfigured or malicious applications cannot accidentally bypass Tor by making raw system calls.
The innovation behind oniux lies in its deep integration with Linux’s isolation primitives. By creating a unique network namespace, oniux removes the application’s access to the system’s network interfaces (like eth0) and instead assigns a custom interface called onion0. This virtual interface is linked to the Tor network through onionmasq, a Tor-aware DNS and routing tool.
The project leverages Rust’s safety and concurrency features, employing the clone(2) syscall to create isolated child processes with their own network, mount, PID, and user namespaces. After establishing the environment, oniux configures DNS resolution and drops all elevated privileges. The application is then launched within this sandboxed environment, securely and transparently routed through Tor.
For context, the Tor Project — a nonprofit known for its flagship anonymity network — has been actively developing Arti, a new Tor implementation in Rust, to replace the long-standing C-based CTor. oniux is among the first high-level tools to fully embrace this new stack, combining it with modern Linux security features for improved isolation and reduced attack surface.
In contrast to the well-established torsocks, which intercepts network calls at the libc level and routes them through a SOCKS proxy, oniux takes a kernel-assisted approach. This mitigates risks posed by statically linked binaries or applications that bypass libc entirely — an increasingly relevant threat vector with the rise of languages like Zig and Rust.
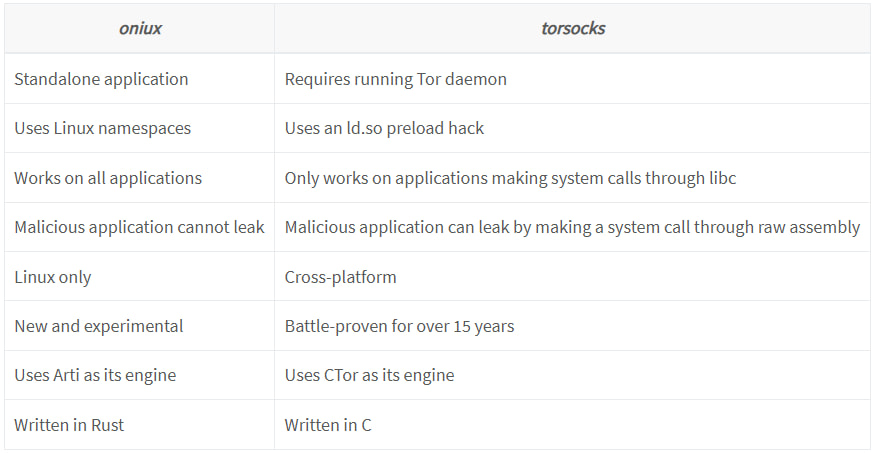
The differences between the two approaches are clear:
- oniux is Linux-only and uses namespaces and Rust-based Arti, offering high security guarantees.
- torsocks is cross-platform and time-tested but vulnerable to bypasses by non-libc system calls.
Tor Project
Installing oniux requires a Linux system with Rust’s Cargo toolchain. Users can then run applications like curl, bash, or even graphical programs such as hexchat through the Tor network by simply prefixing them with oniux.
Despite its promising architecture, the project is still labeled experimental. The developers acknowledge that while it’s functional and already quite capable, it lacks the maturity and widespread testing of tools like torsocks. Users are encouraged to test and contribute, helping move the tool toward production readiness.







Leave a Reply