
The Google Threat Intelligence Group (GTIG) has published its annual review of zero-day exploits for 2024, revealing a gradual but persistent rise in zero-day exploitation and a concerning shift towards enterprise-targeted attacks.
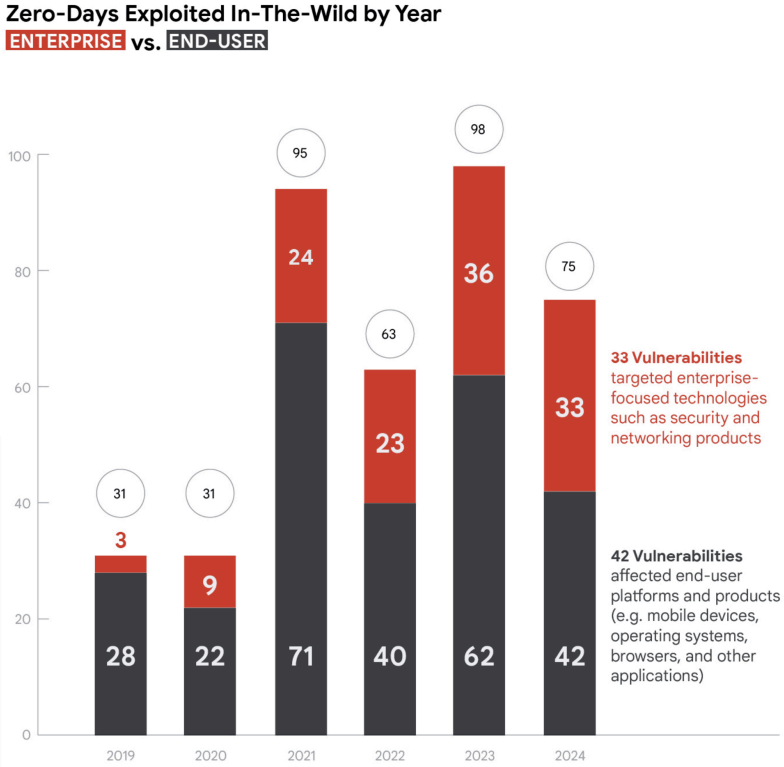
Despite a slight decrease from 2023 figures, with 75 vulnerabilities identified compared to 98 the year before, exploitation activity remains higher than 2022 levels, signaling an ongoing security arms race.
The report is built on GTIG's original research, breach investigations, and reliable open-source intelligence. It provides a comprehensive look at how threat actors evolved their techniques over the past year, reflecting both enduring and emerging attack patterns. The data was collected through 2024, with numbers possibly subject to revision as more forensic analyses come to light.
Key findings and trends
In 2024, enterprise technologies represented 44% of the exploited zero-days — a notable increase from 37% in 2023. This trend was driven by attacks on security and networking products, such as Ivanti's Cloud Services Appliance, Palo Alto Networks PAN-OS, and Cisco's Adaptive Security Appliance. These technologies, given their privileged positions within corporate environments, offer attackers efficient pathways to widespread system compromise.
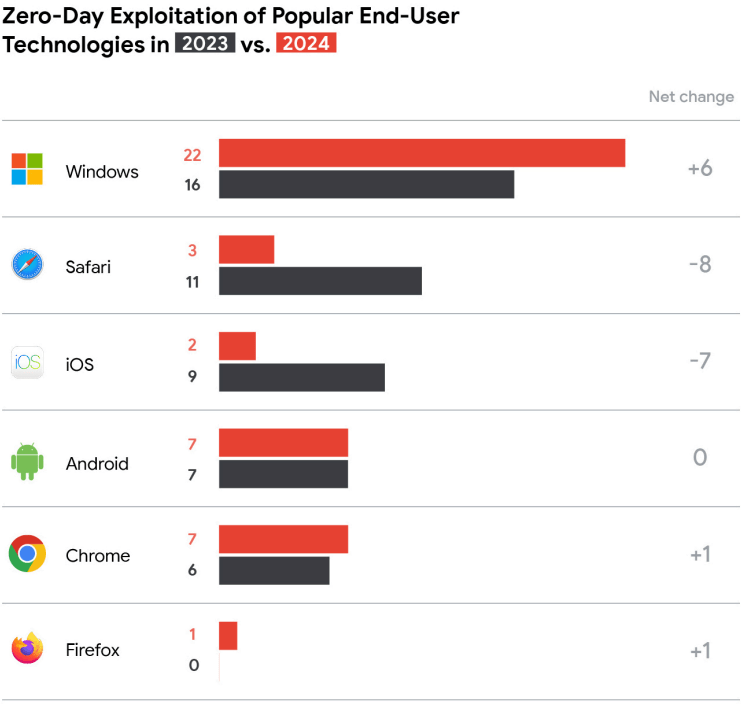
End-user platforms — browsers, mobile devices, and desktop operating systems — still dominated overall exploit targets. However, exploitation numbers for browsers and mobile devices dropped sharply compared to 2023, attributed to stronger mitigations by vendors. Chrome, due to its large user base, remained the most targeted browser, while Microsoft Windows continued to be the top desktop OS under attack, reflecting its ubiquity across personal and enterprise spaces.
The GTIG observed 20 vulnerabilities in security and network appliances, suggesting attackers are strategically prioritizing targets that offer high-value rewards. Ironically, security products often lacked effective endpoint detection and response (EDR) coverage, giving adversaries opportunities for undetected compromise.
Who's behind the zero-day exploits?
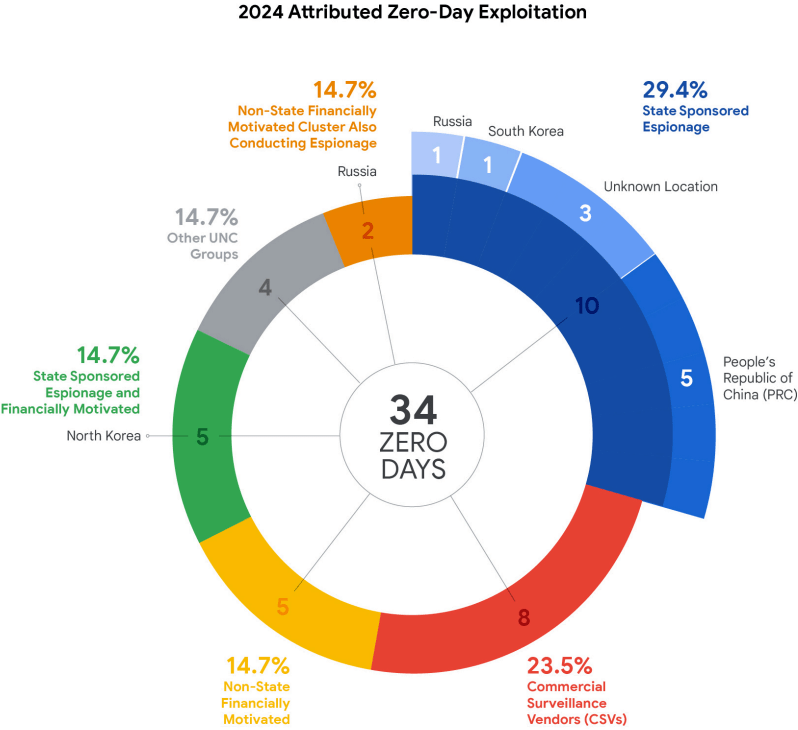
Over 50% of the attributable zero-day attacks in 2024 were linked to cyber espionage groups. China's state-backed actors exploited five vulnerabilities, exclusively in security and networking equipment, showcasing their continued focus on long-term access and data theft. North Korean actors matched China's numbers for the first time, exploiting five zero-days across Chrome and Windows, blending espionage with financially motivated cyber operations.
Commercial surveillance vendors (CSVs) also maintained a significant presence, accounting for eight exploited zero-days. Though their attributed activity dipped slightly, likely due to better operational security practices, their impact remains profound. Vendors like Cellebrite were cited, with CVE-2024-53104 exploited to compromise Android devices via malicious USB connections, targeting activists in politically sensitive regions.
Financially motivated threat groups like FIN11 also remained active, exploiting file transfer solutions such as Cleo products to steal and extort sensitive data.
GTIG researchers uncovered major zero-day chains in 2024:
- CVE-2024-44308 and CVE-2024-44309: An attack on the Diplomatic Academy of Ukraine's website weaponized WebKit vulnerabilities to steal cookies from MacOS Intel users, targeting login.microsoftonline.com sessions.
- CVE-2024-49039: Exploited alongside CVE-2024-9680 in Firefox and Tor browsers by the CIGAR group, this vulnerability enabled sandbox escapes and privilege escalation to SYSTEM level, bypassing critical Windows security mechanisms.
GTIG's analysis predicts a continued rise in zero-day exploitation, especially against enterprise technologies. The report underscores the importance of safe coding practices, rigorous code reviews, and updated security architectures, advocating for zero-trust models, continuous monitoring, and the integration of EDR into traditionally under-monitored products like networking appliances.







Leave a Reply