
Kaspersky's Global Research and Analysis Team (GReAT) uncovered a cyber-espionage campaign that targets Italian users, delivering a new Remote Access Trojan (RAT) named “SambaSpy.”
What sets this campaign apart is its region-specific infection chain, ensuring that only systems with Italian language settings were infected. While Italy was the main focus, Kaspersky's investigation revealed broader ties to Brazil and Spain, highlighting the attackers' ability to extend their reach across multiple regions.
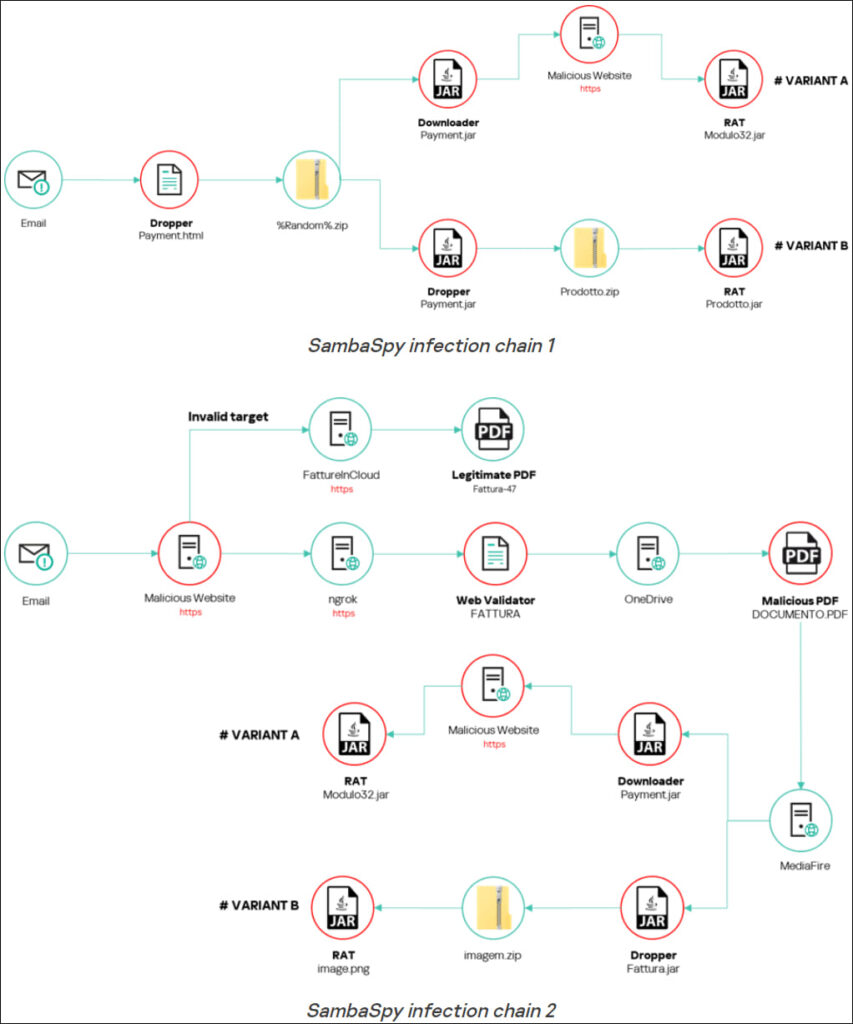
A precise infection chain
The campaign starts with phishing emails that appear to come from a legitimate Italian real estate company, written in Italian but sent from German email addresses. The emails lure victims into clicking a link, which redirects them to a legitimate cloud service used by Italian businesses for invoicing — FattureInCloud. While this redirection may seem innocent, users with Italian language settings on their browsers (Edge, Firefox, or Chrome) are instead forwarded to a malicious server.
Once the malicious webpage is loaded, victims are tricked into downloading either a dropper or downloader file, both of which initiate the deployment of SambaSpy. Key to this campaign is the thorough screening process that ensures only Italian users are infected, a tactic rarely seen in cybercrime, where broader, language-agnostic campaigns are more common.
Kaspersky
SambaSpy RAT capabilities
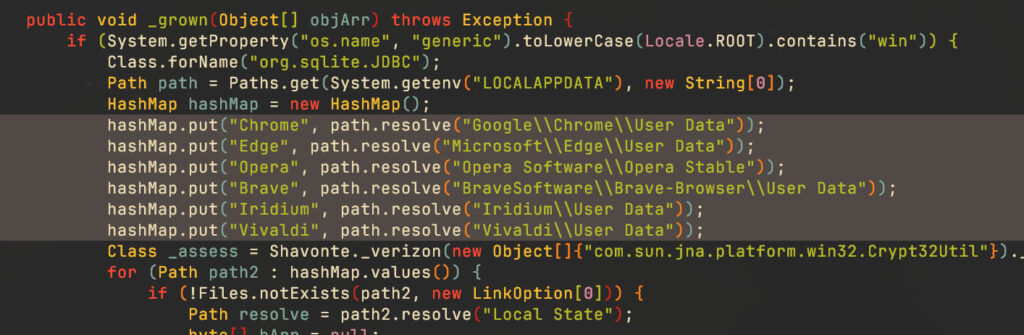
SambaSpy is a highly capable RAT written in Java, with its code obfuscated using Zelix KlassMaster. This malware provides attackers with complete control over infected systems, allowing them to:
- Manage the file system and processes
- Log keystrokes and clipboard content
- Steal credentials from browsers like Chrome, Edge, and Opera
- Access webcams and take screenshots
- Control remote desktops
- Load additional plugins for extended functionality
The malware also performs extensive checks to confirm it is running on Italian systems, reinforcing the attackers' interest in highly targeted, region-specific infections.
Kaspersky
Broader links to Brazil and Spain
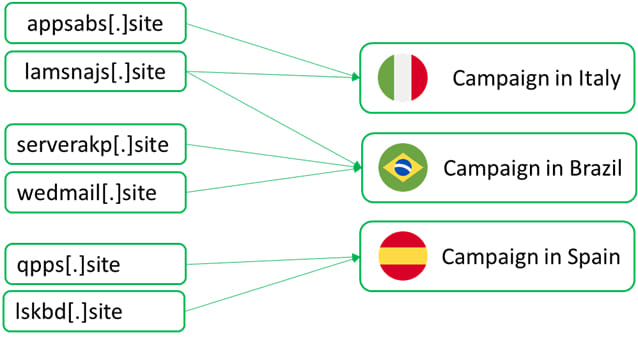
Though this attack was tailored for Italian victims, researchers uncovered links to campaigns targeting users in Brazil and Spain. Domains registered by the same threat actors were used to distribute malware in these regions. However, unlike the Italian campaign, these operations did not include language-specific filters, indicating a broader targeting approach.
Kaspersky
The attackers' connection to Brazil became apparent through code comments and language artifacts found in the malware, which were written in Brazilian Portuguese. This suggests that while Italy was the focal point of this particular campaign, the attackers have also shifted their sights to Latin American and other European targets, broadening their criminal activities.
While attribution remains uncertain, the use of Brazilian Portuguese in the code and infrastructure linked to campaigns in Brazil and Spain strongly points to threat actors with connections to Brazil. These actors have shown a pattern of targeting countries with closely related languages, such as Italy, Spain, and Portugal, making their campaigns more effective by taking advantage of linguistic and cultural similarities.







If you live and breathe, cyber warfare is a pervasive and evolving threat, affecting various regions and entities worldwide. Cyber warfare is a global phenomenon, with various nation-states, non-state actors, and private entities engaged in a range of activities, from espionage and disruption to theft and sabotage. The landscape is constantly evolving, with new TTPs emerging and old ones adapting to countermeasures.
The recent incidents involving exploding pagers used by Hezbollah members in Lebanon have raised concerns about the expansion of cyber-espionage to kinetic attacks. Within the recent news reports having highlighted incidents of exploding 2-way radios, specifically targeting walkie-talkies used by Hezbollah in Lebanon.
Malware-induced overheating, Structured vulnerability, Escalation concerns, Global significance. Near recent significant in cyber incidents, such as Chinese espionage activity against Canadian parliamentarians and U.S. government employees, demonstrate the ongoing threat of cyber-espionage. The investigation into the leak of sensitive information on Seoul’s espionage activities in South Korea also underscores the importance of securing sensitive data.
Tampered or hacked communication devices have been involved in various conflicts and contexts throughout history, from early wireless telegraphy demonstrations to modern state-sponsored cyberattacks.
The exploding pagers incident in Lebanon serves as a warning about the expanding scope of cyber-espionage, where malware and cyber attacks can trigger physical harm. As cyber-physical attacks become more sophisticated, it is essential for governments, organizations, and individuals to prioritize device security and potential energy source protection to mitigate the risks of such incidents.