
Doctor Web has identified a widespread infection targeting Android TV boxes through a malware strain dubbed Android.Vo1d. This backdoor trojan has affected nearly 1.3 million devices in 197 countries, compromising system files and enabling attackers to remotely install software on users' devices.
The issue came to light in August 2024 when several users reached out to Doctor Web after detecting suspicious changes in their TV boxes. Affected models include the R4, TV BOX, and KJ-SMART4KVIP, all running on different versions of Android, from 7.1.2 to 12.1. These devices displayed similar infection patterns, with notable system modifications that indicated the presence of Android.Vo1d.
Infection mechanism
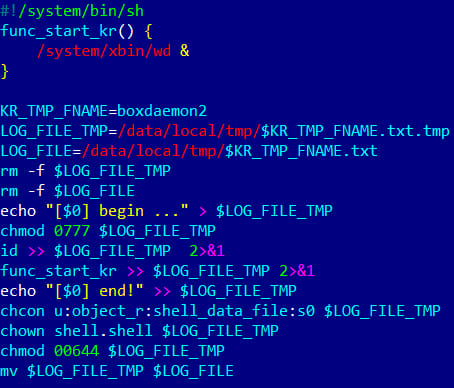
Doctor Web's analysis revealed that the trojan compromises the system by placing malicious components into the system's file storage and disguising them as legitimate system files. Key files altered in the infection include:
- /system/xbin/vo1d – The trojan's primary executable.
- /system/xbin/wd – A second key component, used to maintain persistence.
- /system/bin/debuggerd – Typically used for error reporting but replaced by a script to run the trojan.
- /system/bin/debuggerd_real – A backup of the legitimate debuggerd file, which the malware mistakenly moved twice, causing further dysfunction.
Doctor Web
The malware disguises itself by naming key components to resemble legitimate system programs, such as “vo1d,” a variant of the system process “vold,” with a subtle character change to avoid detection. The malware also registers itself in critical system files like install-recovery.sh, allowing it to persist through reboots. It also modifies daemonsu, which handles root privileges, to secure its auto-launch at startup.
The two main modules, Android.Vo1d.1 (responsible for launching Android.Vo1d.3) and Android.Vo1d.3, work together to maintain the infection. Android.Vo1d.3 installs additional malware and even monitors specified directories to automatically install APK files found there, making it a potent vector for downloading further malicious software.
Targets and impact
Android TV boxes, often running outdated versions of Android, are particularly vulnerable to these attacks. Many devices are shipped with older OS versions, such as Android 7.1, which have known, unpatched vulnerabilities. In some cases, manufacturers falsely advertise newer Android versions, further compounding security risks. These devices, being low-cost and less frequently updated, are prime targets for attackers.
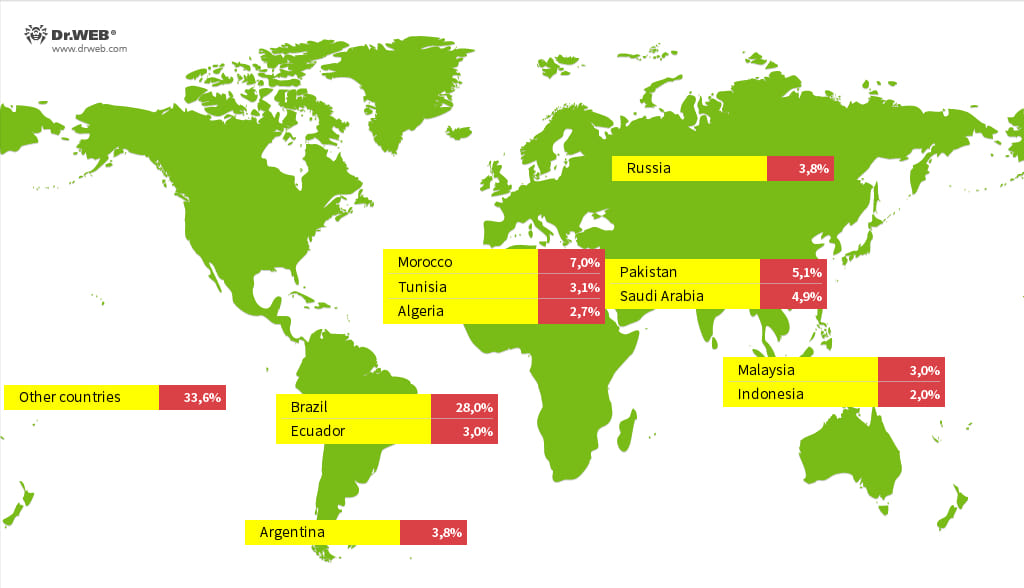
Doctor Web's analysis shows that the infection is widespread, with the highest numbers of compromised devices in countries such as Brazil, Morocco, Pakistan, Saudi Arabia, and Russia. The infection's global scale highlights the significant security risks that come with using devices that lack proper security updates and run outdated firmware.
Doctor Web
Potential infection vectors
While the exact infection vector remains unknown, two plausible methods have been identified. The malware could be exploiting vulnerabilities in the Android operating system to gain root privileges, or it could be introduced via unofficial firmware versions, which often come with pre-installed root access. Either method would allow Android.Vo1d to take full control of the device, enabling remote execution of malicious commands.
Recommendations
Users concerned about the Android.Vo1d malware can run scans with reputable mobile antivirus tools to detect and remove all known variants of the trojan. However, due to the malware’s ability to embed itself deep within the system files, full recovery may only be possible if root access is available.
To mitigate the risk of infection, users are advised to:
- Only use official updates provided by the device manufacturer.
- Ensure your Android TV box runs the latest firmware to minimize exposure to vulnerabilities.
- Use antivirus solutions to detect malware early.
- Only download apps from trusted sources, as sideloading increases malware risk.







Leave a Reply